TakeOver - TryHackMe
CTF Writeup for TakeOver from TryHackMe
This CTF is based on careful subdomain enumeration.
First off with the nmap scan. We find 22/tcp[SSH], 80/tcp[HTTP], and 443/tcp[HTTPS]. Its a Linux host.
When navigating to the given host domain 'futurevera[.]thm', we find a landing page.
After enumerating (directories / walking) for short while we find this page has no help for us; we can move onto enumerating subdomains.
user$ gobuster vhost -w subdomains -u http://futurevera.thm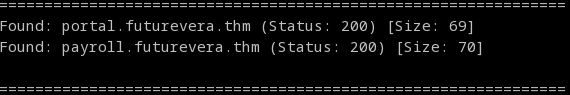
user$ gobuster vhost -w subdomains -u https://futurevera.thm -k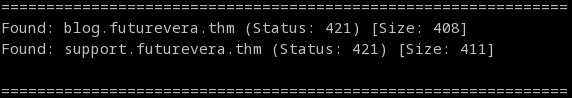
We have two different results for the HTTP/HTTPS VHOST enumeration, we will start with checking the HTTP subdomains.


In these two results of their HTTP pages, after enumeration there is nothing of sustenance; when checking their HTTPS counterpart, it gives back original site.
Now to check the HTTPS subdomains.
When enumerating these two subdomains we don't find anything in their contents, mostly Space Ipsum (Lorem Ipsum Space Version). We can check their SSL/TLS certs for any additional information.
The blog page's cert had nothing of interest, but support's did.
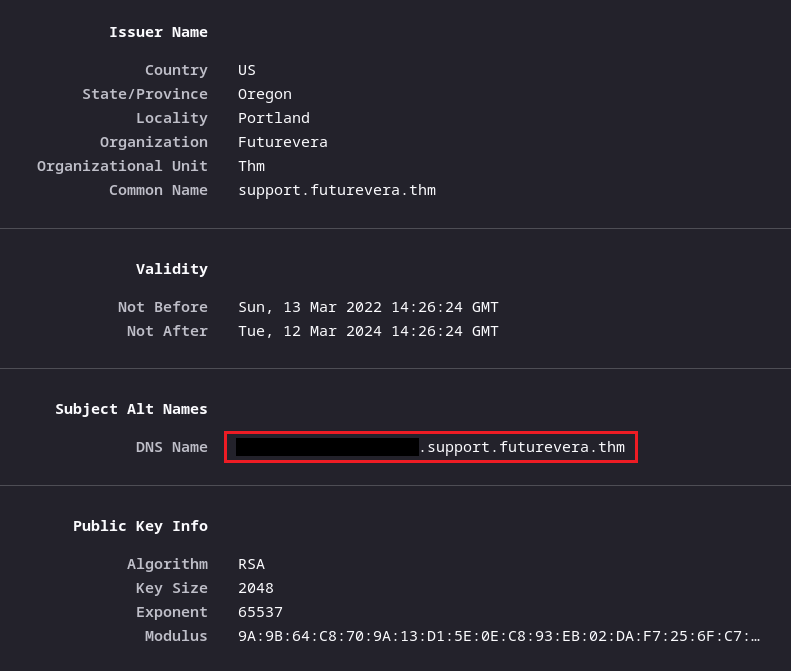
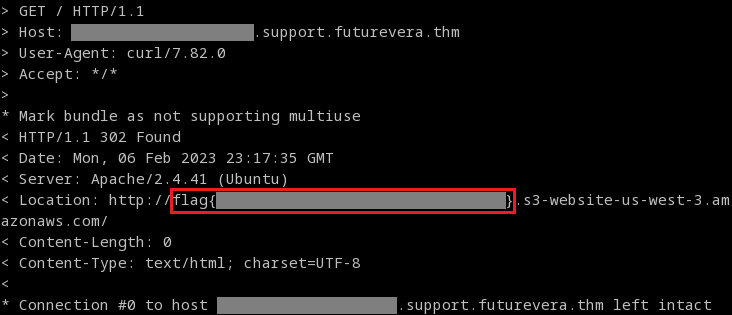
When we navigate to this hidden subdomain, we find our flag.
This CTF is a very good teaching of why to do careful enumeration.
That's all :) .