Surfer - TryHackMe
CTF Writeup for Surfer from TryHackMe
This is a CTF by TryHackMe based on SSRF abuse.
Seemingly this is purely going to be a web based assignment, so I'm going to skip doing the nmap scan for this, and directly go into the website.
When we go to the CTF url, we are prompted by a login screen., interesting.
Okay; so to start I want to run a gobuster scan just to make sure I don't miss anything of the initial enumeration, something that could make this easier.
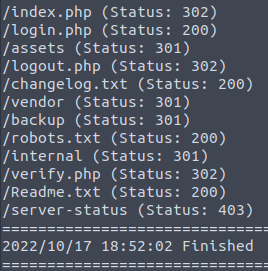
From these results we see a lot of redirects; lets look at /robots.txt as per usual enumeration, cause this could reveal what they don't want indexed.
Navigating to the /robots.txt we find a Disallow for '/backup/chat.txt'; this is unusual but might as well give it a look for the sake of it.
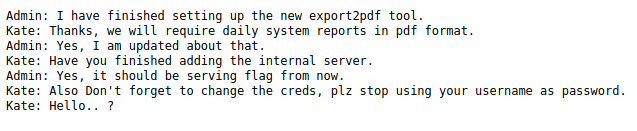
So this page reveals a conversation between the Admin (oh?) and a person named Kate. So they have some new software, internal server serves the flag (noted), and apparently the Admin is using their username as their password, understood.
Using this info (admin:admin) it allows us to login into the server. On the right side bar, we see a mention of internal pages being served at '/internal/admin.php', navigating to it we are unable to view since it is only viewable internally.
The other item on the page of interest is 'Export to PDF' button; when used it generates a report of the page '127.0.0.1/server-info.php'. Checking the network traffic within the browser we can see the parameters of this tool usage.
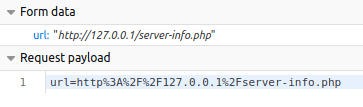
Seeing this, we can see that its parameter is to a specific page '/server-info.php'.
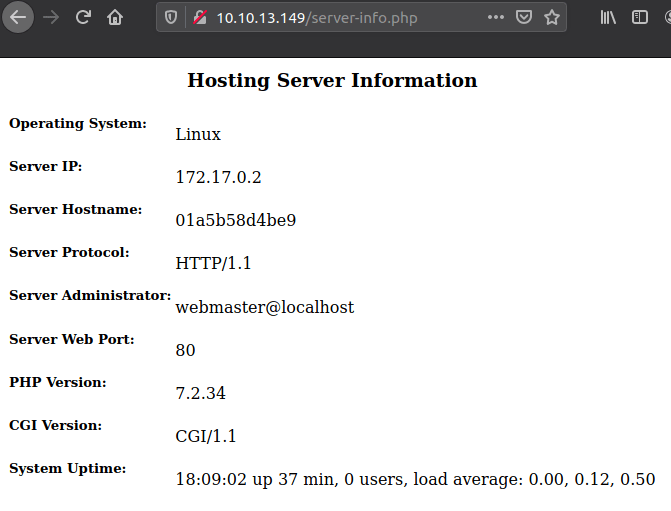
Now from checking how this PDF tool works, and how the parameters are given, lettuce manipulate this to get our '/internal/admin.php' page and our flag.
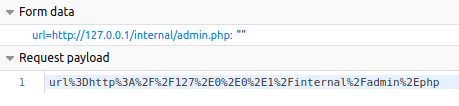
This parameter change, in theory, should now generate a PDF of the page '127.0.0.1/internal/admin.php' that as previously mentioned could only be accessed internally, of which this PDF tool is.
Once sent, the response payload should be a base64 encoded string. We will now take that and convert it to a usable PDF for us to view.
user$ echo "<response>" | base64 -d > flag.pdf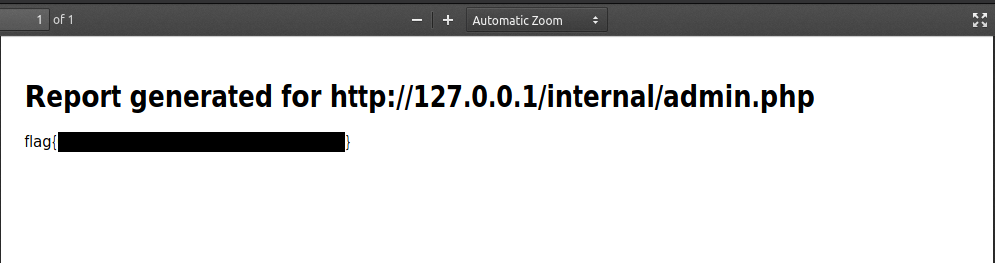
This was a good medium level CTF, made by TryHackMe, demonstrating SSRF.
That's all :) .