MD2PDF - TryHackMe
CTF Writeup for MD2PDF from TryHackMe
This CTF is based on web enumeration.
Starting off with an nmap scan; We find 22/tcp[SSH], 80/tcp[HTTP], and 5000/tcp[upnp?]. Its a Linux host.
Navigating to the 80/tcp we find the MD2PDF website.
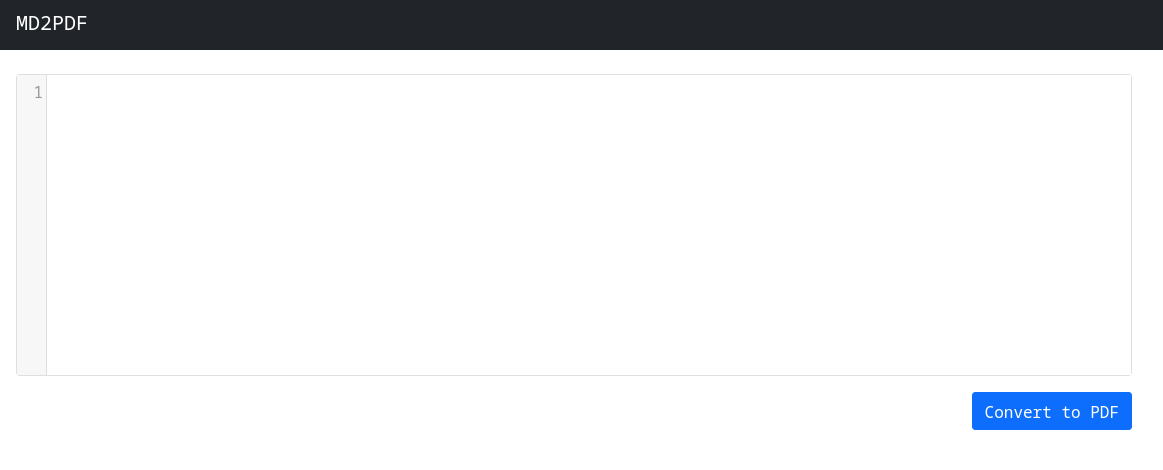
Now we need to enumerate to potentially find what we're looking for to get our flag; we'll do a gobuster dir scan first.
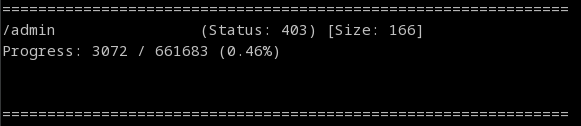
Interesting, we have a supposed 'admin' page; let's see it.

Well, now it seems our target path will be to use the MD2PDF tool to get a view of the 'admin' webpage that's only accessible through the localhost.
When testing payloads, MD/PDF can use HTML elements to abuse LFI/RFI, webpage source and etc. I used a 'iframe' element and its harbored good results.
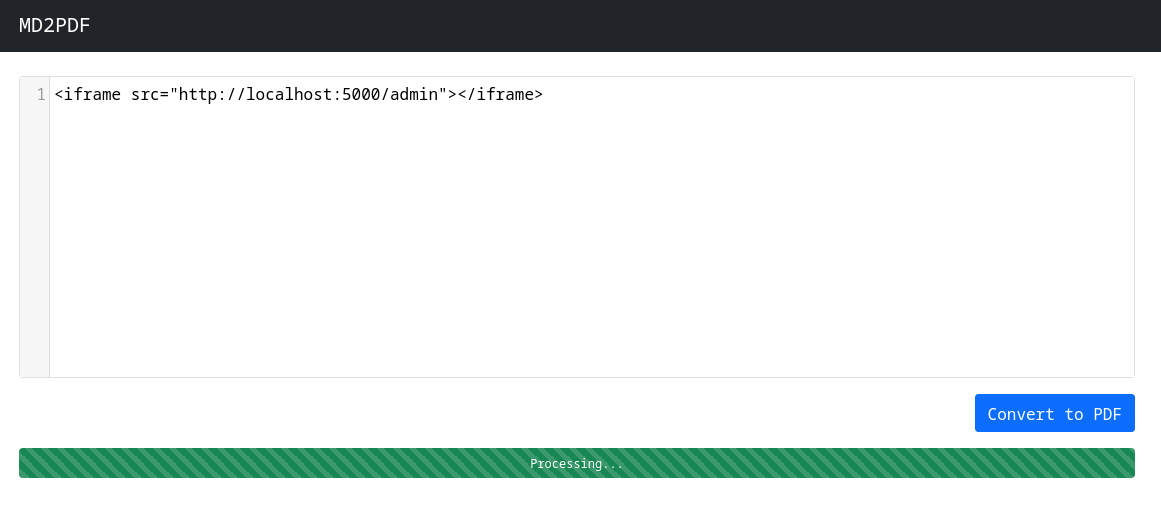

We now have our flag.
That's all :) .