Keeper - HackTheBox
CTF Writeup for Keeper from HackTheBox
This is based on bad password hygiene.
Starting with the nmap scan: 22/tcp[SSH] and 80/tcp[HTTP]. Linux host.
Start with checking the HTTP page..
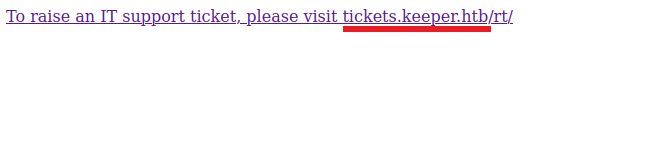
From this we now know the domains 'keeper.htb' and 'tickets.keeper.htb' .
Now following the link to 'tickets.keeper.htb/rt/' ..
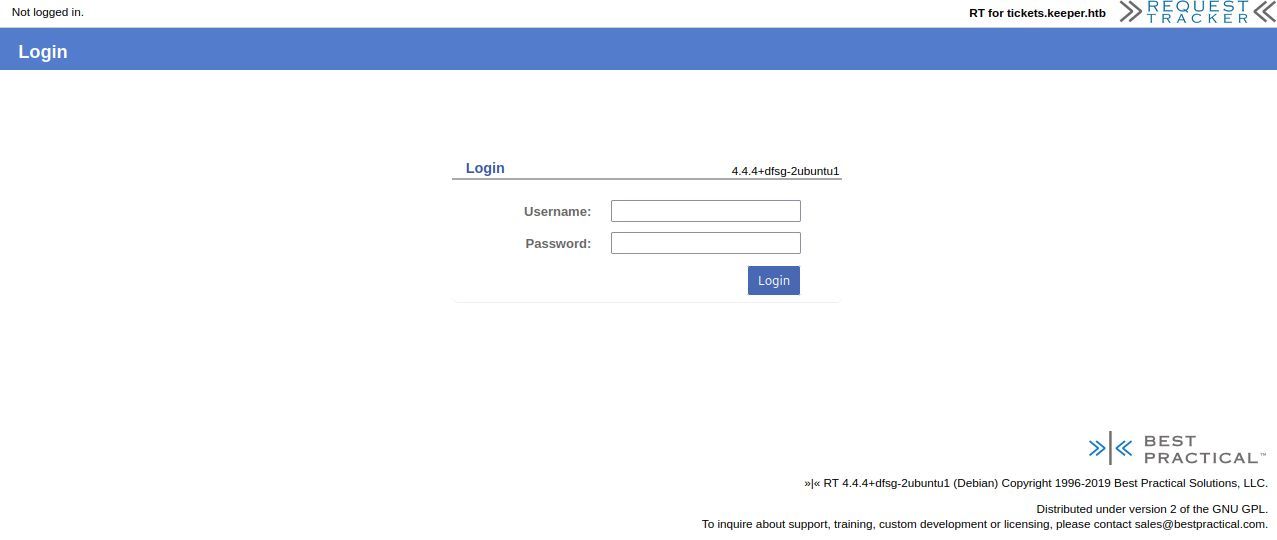
Now we have something to look into. Firstly though before we do any search for vulnerabilities or exploits/PoCs, we can try to see if RT has Default Credentials and if they work.
It did.
Time for enumeration: as I'm unfamiliar with the internal workings of RT (If it has OS ran scripts, pages, etc..) it will have to be walked first.
I stumbled upon a interesting page..
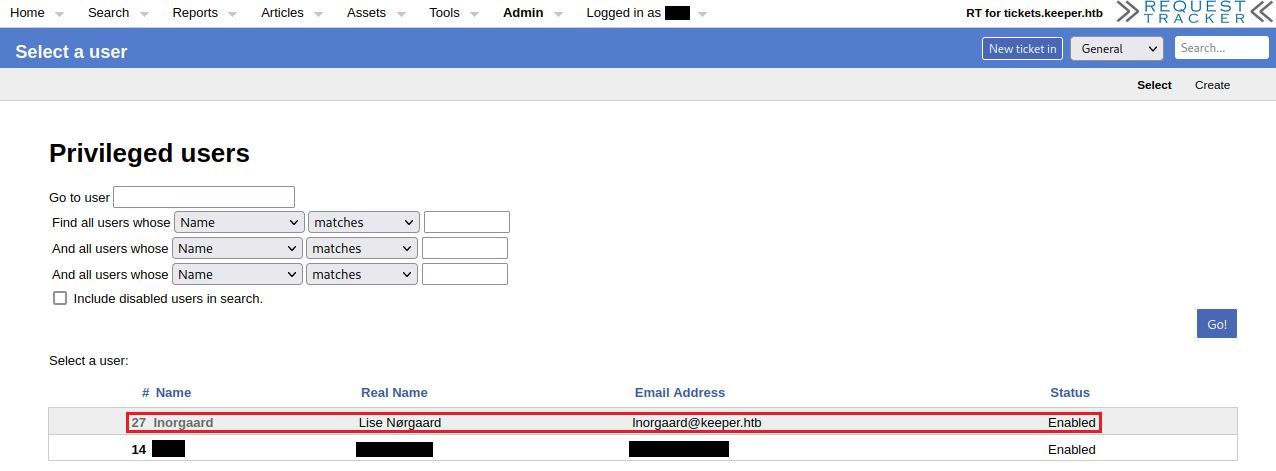
Checking out the Users information..
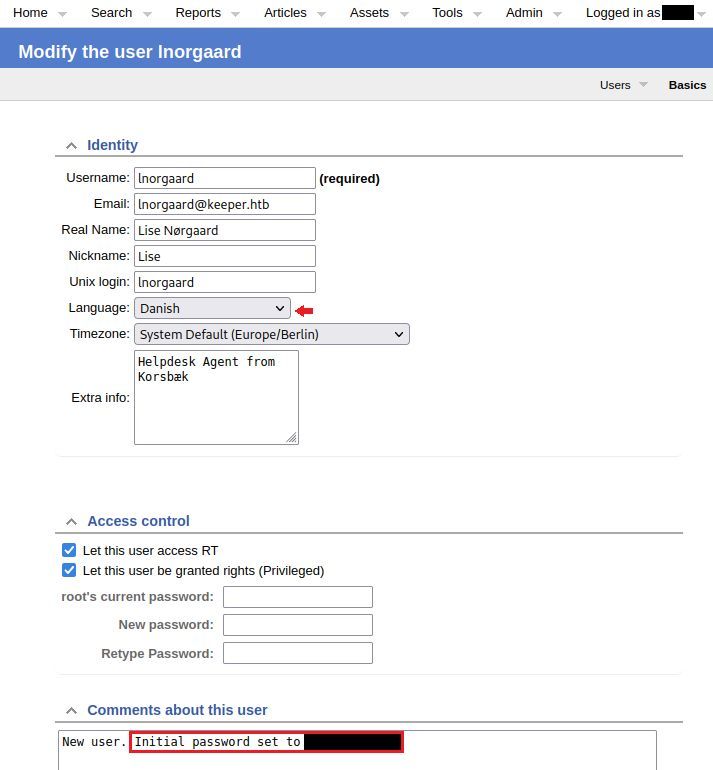
Using this newly found information we can now login through SSH.
Grab the 'user.txt' flag.
lnorgaard$ cat ./user.txt
> ********************************Collection of user flag.
Upon login, we find a file 'RT30000.zip'. When unzipping we find two output files, one is a KeePass DB and other being what seems to be a memory dump; seems to suggest CVE-2023-32784.
CVE-2023-32784
Description: In KeePass 2.x before 2.54, it is possible to recover the cleartext master password from a memory dump, even when a workspace is locked or no longer running. The memory dump can be a KeePass process dump, swap file (pagefile.sys), hibernation file (hiberfil.sys), or RAM dump of the entire system. The first character cannot be recovered. In 2.54, there is different API usage and/or random string insertion for mitigation.
TLDR; KeePass <v2.54 it is possible to retrieve (mostly) cleartext master password from memory, through various methods.
I uploaded – using my Krampus tool – the ZIP to my machine to do this process.
For this I found three options to choose from: .NET, Python and Rust. I personally used the Python variant as not in the mood to mess with .NET shit.
user$ python3 poc.py ~/Downloads/uploads/KeePassDumpFull.dmp
> 2023-08-29 14:47:09,997 [.] [main] Opened /home/user/Downloads/uploads/KeePassDumpFull.dmp
> Possible password: ●,dgr●d *** fl●**
> Possible password: ●ldgr●d *** fl●**
> Possible password: ●`dgr●d *** fl●**
> Possible password: ●-dgr●d *** fl●**
> Possible password: ●'dgr●d *** fl●**
> Possible password: ●]dgr●d *** fl●**
> Possible password: ●Adgr●d *** fl●**
> Possible password: ●Idgr●d *** fl●**
> Possible password: ●:dgr●d *** fl●**
> Possible password: ●=dgr●d *** fl●**
> Possible password: ●_dgr●d *** fl●**
> Possible password: ●cdgr●d *** fl●**
> Possible password: ●Mdgr●d *** fl●**The astericks are my obfuscation.
With this, you can go down the route of creating a wordlist with crunch, but why dive in deep depression if not needed? Instead, we can just look it up in the search engine and see if anything pops up.
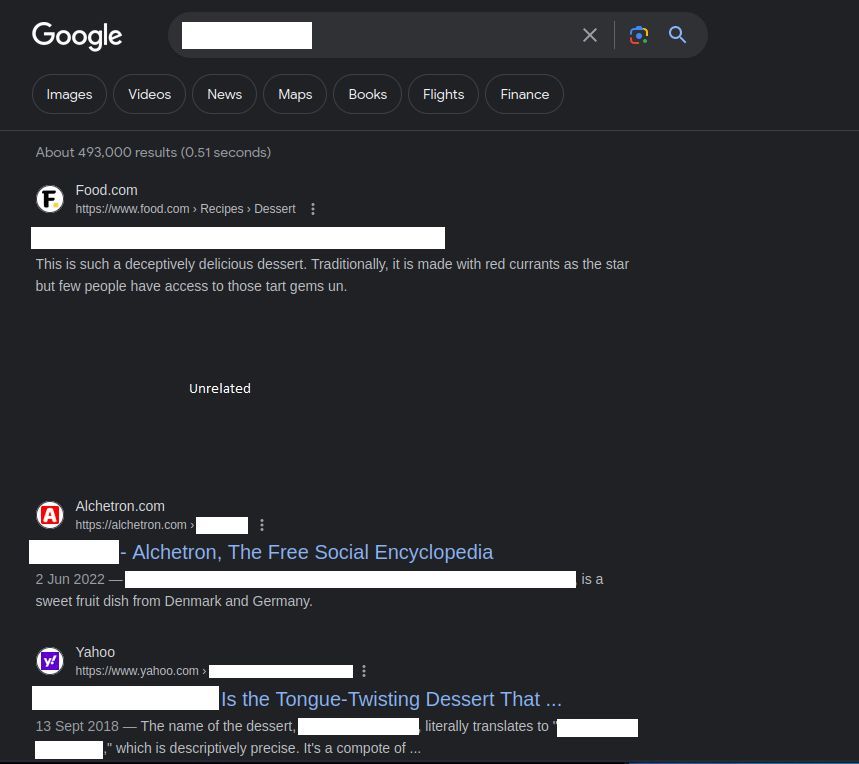
If you need extra hint to find it: look for the red arrow in the RT user enumeration photo, and add the word as a search keyword.
Now we can unlock the KeePass DB with some letter modification (A->a) .
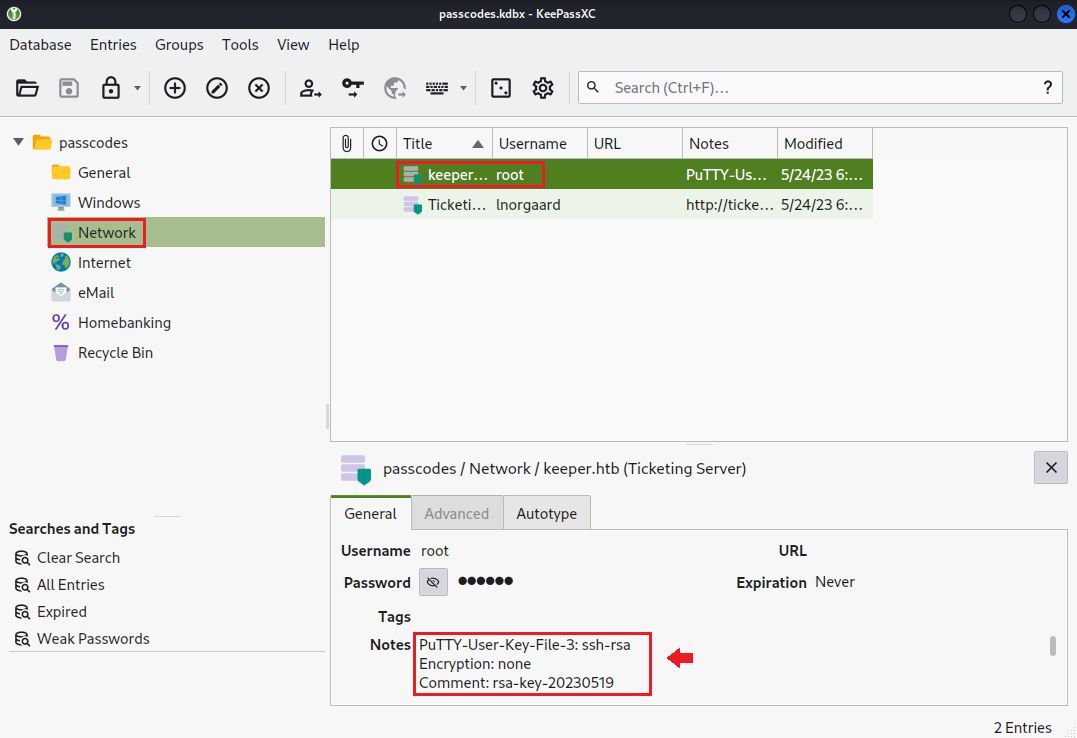
When looking, we find the credentials to seemingly the root user; password doesn't work when I tried, but what about the note? It's a PuTTY version of SSH-RSA key.
Copy the note contents to a file and login using the PuTTY tool ( or you can convert it to OpenSSL type) .
Now we have a root shell. Collect 'root.txt' flag now.
root# cat ./root.txt
> ********************************Collection of the root flag.
That's all :) .