Corridor - TryHackMe
CTF Writeup for Corridor from TryHackMe
This CTF explores a simple IDOR vulnerability, made by the legend John Hammond.
Ports: 80/tcp
This CTF has only one port open being HTTP; so when we go to it and we are presented by a image of, as the CTF name implies, a Corridor. In this corridor we see that there are a total of 13 doors, each with a mouseover with links to their theoritical linked rooms.
By clicking on the first room we are presented with a empty room, and to save you the time of reading, all 13 rooms are empty. With all of them being empty, they all also do not have any CSS or JS that is any bit interesting, so this really is purely a IDOR room.
Within the links to these rooms are hex codes, which also are to be MD5 hashes. To save the time of clicking through each room to copy the links, you can instead look at the browsers requests on the root page to see all the hashes.
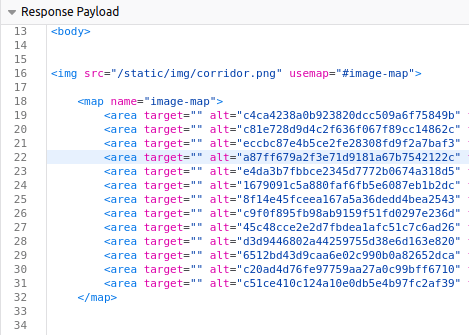
Now, you can copy each one and dump it into Crackstation to do the work.
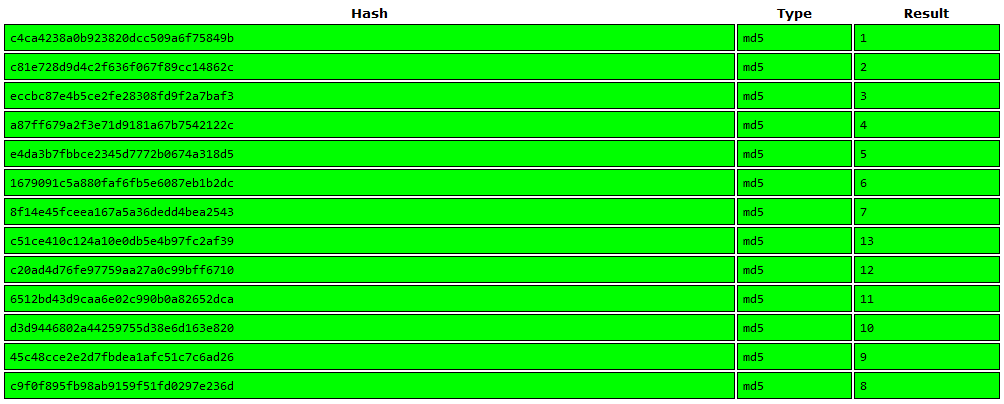
Well.. so we just essentially got the room numbers, which doesn't mean anything to us, or does it...? This is IDOR after all so lets try a different number, maybe 14? Using Cyberchef we hash it with MD5 and.. nope, 14 is a 404 error, along with 15 and 16. Ok, time to go under then; so we try 0 and kachow we get our flag.

Yes, a simple IDOR vulnerability example but intuitive and interesting. Thanks to TryHackMe and John Hammond for this room.
Thats all :) .